When you search for "PGP encryption online," you'll find a ton of browser-based tools that promise to secure your emails in a few clicks. It seems incredibly convenient, but this approach comes with serious hidden risks that can completely undermine your email privacy.
Think of it this way: using one of these sites is like handing a sealed, confidential letter to a stranger and asking them to deliver it. You're trusting that they won't peek inside, but you have absolutely no way to be sure. True email security depends on keeping your private data under your control, not handing it over to an unknown third party.
The Allure and Dangers of Online PGP Encryption
It's easy to see why people gravitate toward online PGP tools. You just visit a website, paste your message, and get an encrypted block of text back. No software to install, no complicated setup. That instant gratification, however, comes at a huge cost to your email security.
The core problem is that most of these web-based tools do the encryption work on their server, not on your computer. This server-side processing goes against the entire philosophy of strong email privacy, which is built on the principle that you—and only you—should ever have access to your private keys and unencrypted messages.
When you use a random online tool for your email, you're placing blind trust in an unknown entity. You have no idea if their server is logging your original message, your password, or even the private key you might be using. This creates a gaping vulnerability that defeats the whole purpose of using PGP for email security.
Understanding the PGP Standard
PGP, or Pretty Good Privacy, has been the gold standard for secure communication since it was created way back in 1991. It works by cleverly combining symmetric and asymmetric cryptography to lock down messages. If you want to dive deeper into how that works, you can learn more about the differences between symmetric and asymmetric key encryption in email in our detailed guide.
Because PGP is decentralized, it doesn't rely on a single, central authority, making it incredibly resilient against surveillance and a cornerstone of modern email privacy.
At its heart, PGP's security model is built on personal control and verifiable trust. The second you perform these critical cryptographic operations on a third-party server, you give that control and trust away, creating an unacceptable risk for any truly private email communication.
At the end of the day, solid email privacy isn't just about encryption—it's about maintaining a secure environment from top to bottom. While PGP protects the contents of your messages, overall security involves many layers. For example, securing website communications often starts with fundamental steps like installing an SSL certificate to protect data as it travels across the internet.
Why Server-Side PGP Tools Betray Your Privacy
The entire security promise of PGP hinges on one golden rule: your private key must never, ever leave your control. It’s the one thing that belongs only to you. The second you copy-paste that key or an unencrypted email into a website offering "PGP encryption online," you've broken that rule.
Think of it like this: using a web-based PGP tool is the digital equivalent of handing your house key to a stranger and asking them to lock up for you. You're just trusting they'll do the right thing. Did they make a copy? Did they even bother to lock the door? You have no way of knowing for sure.
When you use one of these sites, you're placing that same blind trust in an unknown server. That server can easily log your private key, store your sensitive messages, or worse. This isn't just a theoretical risk; it's a gaping security hole for your email communications.
The Server-Side Security Trap
The fundamental problem here is server-side processing. When a website does the heavy lifting of encryption or decryption for you, it needs direct access to the raw materials—your unencrypted message and, often, your private key. This single step completely undermines the whole point of end-to-end email security.
This diagram shows exactly why this setup is so dangerous. It places a third-party server right in the middle of your private communications.
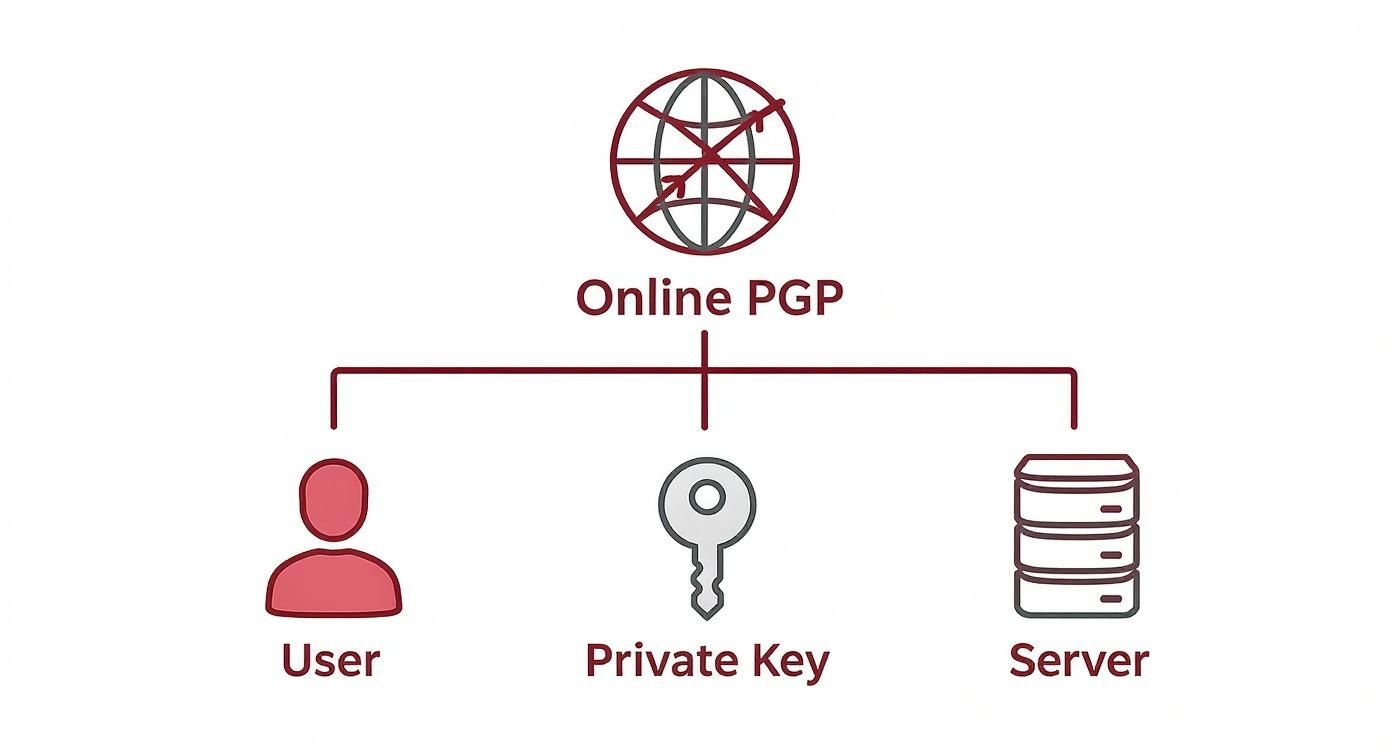
As you can see, the server becomes a middleman with full access to your secrets. It's an unnecessary and avoidable vulnerability in your pursuit of email privacy.
A core principle of strong digital security is minimizing your "attack surface"—the number of potential points of failure. Server-side PGP tools do the exact opposite. They introduce a massive, unverifiable third-party risk into your workflow, completely nullifying the privacy you were trying to achieve.
Once your private key has been exposed on a server, you have to consider it compromised forever. There's simply no way to know if it was copied. This means anyone with access to that server could potentially decrypt not just your future emails, but every past message ever encrypted with the matching public key.
Comparing PGP Encryption Methods
The convenience of web-based tools is tempting, but it comes at a steep price for your email security. To really understand the difference, it helps to see the methods side-by-side.
| Feature | Server-Side Online Tool | Client-Side Application | Secure Hosted Email |
|---|---|---|---|
| Private Key Location | On a third-party server | On your local device only | On your local device only |
| Data Exposure | High risk; plaintext & key on server | Low risk; data stays on your device | Low risk; encryption is end-to-end |
| Control | None; you trust the server | Full control over your keys | Full control over your keys |
| Security Model | Centralized and fragile | Decentralized and robust | Decentralized and robust |
| Primary Weakness | Malicious or compromised server | Compromised user device | Compromised user device |
This table makes it clear: any method that takes your private key off your device introduces a critical point of failure that dedicated client-side tools and secure hosted email platforms are specifically designed to avoid.
Understanding the True Risk
The ease of use offered by online PGP tools is a dangerous illusion. These services take a powerful, decentralized security protocol and twist it into a centralized liability, destroying your email privacy in the process.
Here are just a few of the critical vulnerabilities you're exposed to:
- Man-in-the-Middle (MitM) Attacks: An attacker could intercept the connection between you and the website, grabbing your private key and emails in transit.
- Malicious Code: The site itself could be running hidden JavaScript that captures everything you type or secretly sends your key to another server.
- Server Logs: The web server might be configured to log all data it processes. This could include your plain text emails and private keys, creating a treasure trove for hackers.
For anyone serious about real email security, understanding these risks is non-negotiable. True protection only comes from workflows that keep your keys firmly and exclusively in your possession. To explore how to achieve this properly, take a look at your guide to end-to-end email encryption, which dives into much safer alternatives.
A Safer Way to Use PGP in Your Browser
After all that talk about the dangers of server-side tools, you might be ready to give up on "PGP encryption online" entirely. But there's a much safer way to get the convenience of encrypting in your browser without handing over your private keys. The answer is client-side encryption.
This model shifts all the heavy lifting from some unknown server back to your own computer. Your browser becomes the workspace, but the critical cryptographic magic—the encryption and decryption—happens locally. Your private key never travels across the internet or gets stored on a third-party server. This is a fundamental step toward achieving genuine email security within a webmail environment.
How Browser Extensions Bring PGP to Webmail
The easiest way to get started with client-side PGP is by using a trusted browser extension. These add-ons hook directly into popular webmail providers like Gmail or Outlook, layering PGP security right on top of the interface you already know.
Mailvelope is a great example of this in action. It's an open-source extension that adds end-to-end encryption to your email. When you go to write a message, Mailvelope steps in. It takes your plain text, encrypts it right there on your machine with your locally stored key, and then drops the encrypted block of text back into the compose window. The original, unencrypted email never even gets seen by your webmail provider's servers.
This approach gives you the best of both worlds. You get to stick with the familiar webmail you're used to, but with the rock-solid security of PGP protecting your conversations.
By performing all cryptographic functions locally, client-side tools restore the fundamental principle of PGP security—your private keys remain private. The browser becomes a secure workstation, not a point of vulnerability for your email privacy.
Key Features of Secure Client-Side Tools
When you're looking for a browser-based PGP tool, you want something that puts you in control and is completely transparent. Any solid tool should have these non-negotiable features:
- Local Key Management: You should be able to generate, import, and manage your PGP key pairs entirely within the extension. Your keys should never be sent to a remote server.
- Seamless Webmail Integration: The add-on should be smart enough to detect when you're writing an email and offer simple, intuitive buttons to encrypt or sign your message.
- Open-Source Code: Reputable tools like Mailvelope make their source code public. This allows security experts worldwide to pick it apart, check for flaws, and verify that there are no hidden backdoors. That transparency is how you build real trust in your email security tools.
This client-side method is a huge step in the right direction for email privacy. While encrypted email isn't yet mainstream, it's gaining ground. Only about 11% of users worldwide regularly use email encryption, but businesses are catching on faster, with 51% of companies implementing end-to-end email encryption. Of course, for this to be truly effective, the underlying website must also follow best practices for securing web applications. These numbers show a clear trend: people are waking up to the need for secure communication, and client-side PGP tools are here to meet that demand.
The Gold Standard: Dedicated PGP Email Clients
While browser-based extensions strike a decent balance between convenience and security, they still live inside a web browser—an environment that can be unpredictable. For anyone who needs the absolute highest level of email privacy, the best solution isn't in your browser at all. It's on your desktop. This is where dedicated email clients truly shine as the gold standard for PGP encryption online.
Think of a dedicated client as a purpose-built fortress just for your email. A browser has to juggle countless tabs, scripts, and extensions, but a desktop client like Thunderbird is built for one job: managing your email securely and efficiently. This focused design dramatically shrinks the "attack surface," cutting down the risk of meddling from bad web scripts or sketchy add-ons.

Why Desktop Clients Offer Superior Security
The biggest win with a dedicated client is complete local control. Your private keys are created, stored, and managed right on your own machine. They never touch a third-party server or even get stored by the browser. That’s a level of isolation that no online tool can ever really match, providing the ultimate in email security.
On top of that, you can work entirely offline. You can write encrypted emails, look through old conversations, and manage your keys without an internet connection. You only go online when you’re actually ready to hit send or check for new mail, which keeps your sensitive work shielded from online threats.
A dedicated desktop client puts you in the driver’s seat of your own privacy. By handling all cryptographic operations locally and integrating them seamlessly into your workflow, it transforms PGP from a complex tool into a natural part of your daily email communication.
Key Advantages of a Dedicated PGP Setup
Shifting your PGP workflow to a dedicated client brings some serious perks for both your email privacy and security.
- Total Key Sovereignty: Your private keys live on your computer and nowhere else. This is PGP working exactly as it was designed to, wiping out the risks that come with exposing keys online.
- Enhanced Workflow Integration: Encryption and decryption become a normal part of how you use email. Most clients have simple buttons to sign or encrypt a message, making it just as easy as sending a regular email.
- Offline Capability: Read, compose, and manage your encrypted communications securely, even when you're disconnected from the internet.
- Reduced Vulnerability: By operating outside the browser, you sidestep potential threats from malicious websites, rogue extensions, and browser-specific security holes.
Getting Started with a Desktop Client
Setting up PGP in a client like Thunderbird is surprisingly simple these days. Modern versions often have PGP/GnuPG support built right in, so it only takes a few steps to get going.
- Install a Trusted Client: Download and install a reputable, open-source email client like Mozilla Thunderbird.
- Generate Your Key Pair: Head to the end-to-end encryption settings and follow the on-screen guide to create your first PGP key pair (which includes a public key and a private key).
- Share Your Public Key: Export your public key file and give it to your contacts. Now they can send you encrypted emails.
- Send Your First Encrypted Email: When writing a new message, just click the "Encrypt" button before you send it. The client takes care of all the heavy lifting.
While dedicated clients offer top-tier security, it’s always good to know what’s out there. For a wider view of different email interfaces, take a look at our guide on the 12 best webmail clients of 2025 for privacy and security. But for maximum email privacy, this desktop approach gives you the ultimate control over your digital correspondence.
How Hosted Platforms Make PGP Effortless
While dedicated PGP clients give you ultimate control, what if you just want high-level email security without getting bogged down in the technical details? For many people, the perfect balance of email privacy and convenience is found with secure hosted email platforms. These services are built from the ground up to make PGP encryption a breeze for anyone.
Think of it like this: you could build your own high-performance car from scratch, or you could lease a luxury vehicle. Building it yourself offers total control, but leasing gets you top-tier performance and safety features right out of the box. Secure hosted email platforms are the luxury lease of email privacy.
Services like ProtonMail and Tutanota bake PGP’s powerful encryption right into their core. When you sign up, they automatically generate a key pair for you. From that moment on, any email you send to another user on the same platform is end-to-end encrypted by default. It's the most user-friendly way to achieve robust email security.
Trust Through Zero-Knowledge Architecture
The main trade-off with a hosted service is that you’re trusting someone else to handle key management. But the best platforms tackle this issue head-on with something called zero-knowledge architecture. It’s a fancy term for a simple promise: the system is designed so the service provider cannot access your unencrypted data, even if they wanted to.
Your data gets encrypted on your device before it ever touches their servers, and it can only be decrypted on your recipient's device. This means the provider stores nothing but scrambled, unreadable ciphertext. They hold the locked box, but only you and your contact have the keys. This is a game-changer for email privacy.
This model offers a powerful, user-friendly path to secure communication. The need for it is clear; cybersecurity statistics show over 5.5 billion accounts were breached worldwide, a staggering figure that highlights just how critical strong encryption has become for email security. You can dig deeper into insights on global password security trends to see the scale of the problem.
A zero-knowledge framework is a commitment to user privacy. It ensures that even the company providing the email service is mathematically prevented from reading your messages, creating a powerful foundation of trust that is verifiable through its design.
The Benefits of a Hosted Approach
For anyone who values convenience but isn't willing to compromise on core email security, a hosted platform brings some major advantages to the table.
- No Technical Setup: Key generation, management, and encryption are all handled for you automatically.
- Seamless User Experience: Sending a secure email feels just like sending a regular one.
- Cross-Platform Accessibility: Get to your secure email from any device using their web interface or dedicated apps.
- Built-in Privacy: These platforms are purpose-built for privacy, sidestepping the risks tied to general-purpose email providers that may scan your emails for advertising.
This approach solves the central challenge of making PGP encryption online both safe and simple. By going with a reputable hosted email provider that has a proven zero-knowledge model, you get world-class email security without the steep learning curve. That makes it an excellent choice for individuals and businesses focused on privacy.
PGP and Email: Answering Your Questions
Diving into email security can feel a little overwhelming, and it's normal to have a few questions as you start exploring PGP. Let's clear up some of the most common points of confusion so you can feel confident about protecting your email privacy.
Can I Trust Just Any Client-Side PGP Tool I Find Online?
In a word, no. While running encryption on your own machine (client-side) is the right move for email security, you have to be able to trust the code your browser is running. This is where reputation is everything.
You should always stick to well-known, open-source browser extensions like Mailvelope, which has been publicly audited for security flaws. Avoid obscure websites offering one-off encryption services. A malicious site could easily serve up code designed to snatch your private key, even while claiming everything happens locally on your computer.
Isn't PGP Outdated with Apps Like Signal Around?
Not at all. Encrypted messaging apps are brilliant for quick, back-and-forth conversations, but email plays a completely different role in our lives. Email is the universal, decentralized backbone for professional, official, and long-term communication. PGP is the battle-tested standard for locking down email privacy.
Plus, PGP offers features that are essential in business and legal settings, like digital signatures for authentication. This gives you a mathematical way to prove who sent a message and that it hasn't been altered since it was sent—something most instant messaging apps aren't built for.
Think of it this way: PGP and secure messaging apps aren't competitors. They’re complementary tools for different jobs. PGP secures the formal world of email, while apps like Signal protect your real-time chats.
What's the Real Difference Between PGP and S/MIME?
Both PGP and S/MIME encrypt and sign emails, but they're built on completely different philosophies of trust. This distinction is crucial for your email security strategy.
-
PGP (Pretty Good Privacy): PGP runs on a decentralized model called the "web of trust." People vouch for each other's identities by signing their public keys. It’s an independent, grassroots approach favored by privacy advocates and anyone who prefers not to rely on a central company.
-
S/MIME (Secure/Multipurpose Internet Mail Extensions): S/MIME is centralized. It relies on official Certificate Authorities (CAs)—the same kind of organizations that issue SSL/TLS certificates for websites—to verify a user's identity. This top-down structure is a natural fit for corporate and government environments where a clear hierarchy of trust already exists.
Do I Need to Bother with PGP if I Use a Service like ProtonMail?
If you're just emailing another ProtonMail user, then no—you don't have to think about PGP at all. The platform handles all the encryption and decryption for you behind the scenes, a core benefit of such hosted email platforms.
But the moment you need to send a secure email to someone on a standard provider like Gmail or Outlook, understanding PGP becomes incredibly valuable. Secure email services let you import your contact's public PGP key. This allows you to send them a fully end-to-end encrypted message, extending your bubble of email privacy to connect with anyone, no matter what email service they use.
Ready for an email experience that puts your privacy first? Typewire offers secure, private email hosting with no ads, no tracking, and zero data mining. Start your 7-day free trial and take back control of your inbox. Explore Typewire's features today.