When you decide to host your own email server, you're doing much more than just setting up software. You're building a private, secure communication channel on a server you control, giving you total command over your own data. This is a deliberate step away from the convenience-first model of hosted email platforms like Gmail or Outlook, prioritizing your email privacy and security above all else.
It's a choice for digital sovereignty. You're the one in charge.
Why Take Control of Your Email?
Let's be honest: running your own email server isn't a small weekend project. It’s a real commitment. So why do it? It really comes down to reclaiming your digital independence and ensuring unparalleled email security.
When you use a "free" hosted email platform, you're not the customer; your data is the product. Your emails are scanned, sorted, and analyzed to build shockingly detailed advertising profiles. By taking the reins yourself, you completely shut down that third-party surveillance, guaranteeing your email privacy.
This is a game-changer for anyone dealing with sensitive information. Think about a journalist protecting their sources or a small business keeping client strategies under wraps. When you control the server, you become the gatekeeper. There's no risk of your private financial data or business plans being mined for someone else's gain. You can find a deeper dive into these benefits in our guide on how setting up an email server boosts privacy and security.

Weighing Control Against Convenience
Choosing to self-host is a classic trade-off. You get unmatched control and privacy, but you also inherit the full responsibility for keeping everything running—maintenance, security, and uptime are all on you.
The global email market is massive, expected to hit over $97.1 billion by 2025, mostly because businesses are flocking to convenient hosted email platforms. While popular, these cloud solutions are built on a model that simply can't offer true data ownership or the same level of granular security control.
By managing your own email server, you're not just sending messages. You're creating a private communication channel where you make the rules, you control the encryption, and you can be absolutely certain no one is reading your mail.
Before diving in, it’s crucial to see exactly what you're signing up for. The differences between self-hosting and using a big-name provider are stark, especially when it comes to privacy, cost, and the sheer effort involved.
Self-Hosted Email vs Hosted Email Platforms: A Quick Comparison
This table breaks down the core differences, giving you a clear picture of what each path entails.
| Feature | Self-Hosted Email Server | Hosted Email Platform (e.g., Gmail, Outlook) |
|---|---|---|
| Email Privacy | Complete Control: No third-party scanning or data mining. Your data is yours alone. | Limited Privacy: Emails are scanned for advertising, analytics, and other purposes. |
| Email Security | Your Responsibility: You configure all security measures, from firewalls to encryption. | Managed Security: Handled by the provider, but you have limited control over policies. |
| Cost | Variable: Monthly server fees plus your time for setup and maintenance. | "Free" or Subscription: Often paid for with your data or a monthly subscription fee. |
| Effort Required | High: Requires technical skill for setup, deliverability, and ongoing maintenance. | Low: Minimal setup required; designed for ease of use and convenience. |
As you can see, the choice boils down to what you value most. If absolute control and privacy are non-negotiable, self-hosting is the only way to go. If you prioritize convenience and are comfortable with the privacy trade-offs of hosted email platforms, a major provider might be a better fit.
Building Your Server Foundation
Before you even think about installing software, you need a stable and reliable home for your email server. This isn't the place to cut corners. A solid foundation prevents a world of future headaches and is the bedrock of your email's privacy and security. Think of it as laying the groundwork for your own private communication fortress.
The first big decision is where to host it. Let's get one thing straight: don't even try to run this on your home internet connection. Most residential ISPs block port 25 (the port for sending email) and hand out dynamic IP addresses. Both are complete deal-breakers for getting your emails delivered. You absolutely need a reputable Virtual Private Server (VPS) provider.

Core Requirements for Your VPS
As you shop around for a VPS host, there are two non-negotiable technical features. Without these, your server will never reliably send email to major inboxes like Gmail or Outlook.
- A Static IP Address: This is your server's permanent address online. A consistent IP is the first step toward building a trustworthy sending reputation.
- Reverse DNS (PTR) Control: You must have the ability to set a PTR record. This critical record links your IP address back to your domain name, proving to other servers that you are who you say you are.
A server without a static IP and proper reverse DNS is like sending a letter with no return address. It's immediately suspicious and one of the fastest ways to get your emails flagged as spam.
Choosing Your Operating System
With the server sorted, it's time to pick an operating system. For an email server, your top priorities are stability and security. This is exactly why experienced admins almost always stick with a Long-Term Support (LTS) release of a major Linux distribution.
Your best bets are:
- Debian: Famous for its rock-solid stability and methodical testing. It’s a conservative choice that puts reliability above everything else.
- Ubuntu Server LTS: Built on Debian, it strikes a great balance, offering stability with more up-to-date software and a massive support community.
Both have fantastic documentation and a huge user base, so you'll never be stuck for long if you hit a snag. And you'll need that reliability. The number of global email users is projected to hit 4.6 billion in 2025 and grow to over 4.8 billion by 2027. As you can see from the latest email user growth trends on omnisend.com, the scale is immense, and your infrastructure has to be up to the task.
The Domain Name Strategy
Here’s a pro tip that will save you a world of pain: register a new domain name just for your mail server. Seriously, do not use your primary business or personal domain.
Why? Email deliverability is a reputation game. If you make a mistake during setup—and almost everyone does at first—and get your IP or domain blacklisted, you've only damaged the reputation of your new, separate mail domain. Your main website and all its hard-earned SEO value are completely safe.
This simple separation is a firewall for your brand. It’s a small, cheap insurance policy against the inevitable rookie mistakes, ensuring your core digital identity stays pristine while you get your email server dialed in.
Installing Your Core Email Software
Alright, with the server prepped and ready, it's time for the main event: installing the software that will actually handle your email. Think of this as building the engine and the secure vault for your entire email system.
We're going to use a classic, rock-solid combination that powers a huge chunk of the internet's email infrastructure: Postfix as our Mail Transfer Agent (MTA) and Dovecot as our Mail Delivery Agent (MDA).
- Postfix is the bouncer at the door. It’s responsible for the heavy lifting of talking to other email servers—the actual sending and receiving. It has a stellar reputation for being secure, fast, and reliable.
- Dovecot is the meticulous librarian. Once Postfix accepts an incoming email, Dovecot files it away into the correct user’s mailbox. It's also what lets you securely access that mail with clients like Thunderbird or Apple Mail.
These two work in tandem to create a powerful, private, and secure email core.
First Up: Getting Postfix in Place
Postfix is your server's public-facing component, so its configuration is absolutely critical. From the moment you install it, your mindset should be "security first." The goal is to create a server that is incredibly helpful to your own users but a brick wall to everyone else.
One of the most immediate dangers you need to eliminate is the dreaded open relay. An open relay is just a misconfigured server that lets anyone on the internet send email through it. Spammers are constantly scanning for these, and becoming one is the fastest way to get your server's IP address blacklisted across the planet.
To slam that door shut, you'll configure Postfix to only relay mail under two very specific conditions:
- For authenticated users who have proven their identity with a valid login.
- For connections coming from the local server itself.
This is non-negotiable. It’s the first and most important line of defense you'll establish.
A properly locked-down Postfix server acts more like a private club with a bouncer than a public post office. It checks everyone's credentials at the door and flatly rejects anyone not on the list. This is foundational to your email security.
Setting Up Dovecot for Secure Mailbox Access
While Postfix manages the traffic in and out of your server, Dovecot is all about how you get to your mail. It handles the IMAP and POP3 protocols that your email clients use to connect, and your choices here directly define your email privacy.
The number one rule: enforce encryption. You have to disable all plaintext authentication methods. Allowing your username and password to be sent in the clear, even across a network you trust, is just asking for trouble. You'll configure Dovecot to only accept logins over a secure, TLS-encrypted connection.
This simple step ensures that from the moment your phone or laptop connects, your login details and your email content are shielded from any prying eyes.
You'll also need to tell Dovecot how to store your mail. You have two main options:
- maildir: This modern format stores every email as an individual file. It's incredibly robust, meaning a single corrupted file won't take down your whole mailbox. It performs beautifully and is the hands-down recommendation for any new server.
- mbox: An older format that lumps all your emails into one giant file. It’s simpler in theory, but it’s prone to corruption and can really slow down as your mailbox gets bigger.
Do yourself a favor and choose maildir from the get-go. It will save you a lot of potential headaches down the road.
Tying Postfix and Dovecot Together
Now for the magic. To create a truly integrated system, Postfix and Dovecot need to talk to each other. When you want to send an email, Postfix needs to know you're a legitimate user. Instead of maintaining its own messy list of users, it can just ask Dovecot.
This is done using something called SASL (Simple Authentication and Security Layer). You’ll set up Postfix to hand off authentication duties to Dovecot. Here’s how that handshake works in practice:
- Your email client connects to Postfix to send a message, presenting your username and password.
- Postfix doesn't check them itself. Instead, it passes those credentials over to Dovecot through a secure, private channel.
- Dovecot verifies them against its user database.
- If everything checks out, Dovecot gives Postfix the green light: "Yep, this user is legit." Postfix then happily sends your email on its way.
This setup is not only efficient, but it also tightens up your security. By having Dovecot be the single source of truth for all user accounts, you simplify management and drastically reduce the chance of misconfiguration. It’s a perfect example of how the best email servers use modular, specialized components to build a secure and cohesive whole. This is what it really means to host an email server you can trust.
Solving the Email Deliverability Puzzle
Getting your server online is one thing, but making sure your emails actually land in someone's inbox is a whole different beast. Honestly, an email server that can't reliably deliver mail is more of a technical curiosity than a useful tool. This is where we tackle the single biggest hurdle for anyone wanting to host an email server: deliverability.
Navigating this puzzle is all about building trust, especially with giants like Google and Microsoft who operate the largest hosted email platforms. Your server, with its shiny new IP address, starts with zero reputation. You have to prove it’s a legitimate source of email and not just another spam bot churning out junk. The way you do this is by meticulously configuring your Domain Name System (DNS) records.
The Foundational DNS Records
Before we get into the heavy-duty authentication methods, let's nail the basics. These three DNS records are the bedrock of your server's identity, telling the world who you are and where your mail comes from.
- A Record (Address Record): The most straightforward piece. It simply points your mail subdomain (like
mail.yourdomain.com) to your server's static IP address. - MX Record (Mail Exchanger): This record is the traffic cop for your domain's email. It tells other mail servers, "Hey, if you have an email for @yourdomain.com, send it over here," pointing them to your server's A record.
- PTR Record (Pointer Record): Often called reverse DNS, this is the flip side of an A record. It maps your IP address back to your domain name, acting as a crucial verification step. Most VPS providers have a control panel where you can set this up.
Think of these records as your server's official ID. The A and MX records are your address, and the PTR record is the name on your mailbox. If they don't all match up, receiving mail servers see a red flag and might just reject your mail on the spot.
Mastering the 'Big Three' of Email Authentication
With the foundation solid, it's time to put the three critical email authentication standards in place: SPF, DKIM, and DMARC. These aren't optional anymore; they are your passport to the modern inbox. To really get a handle on this, it's worth understanding why emails go to spam in the first place.
This diagram shows how everything flows together—from the internet, through your Postfix MTA for sending, and to Dovecot for handling received mail.
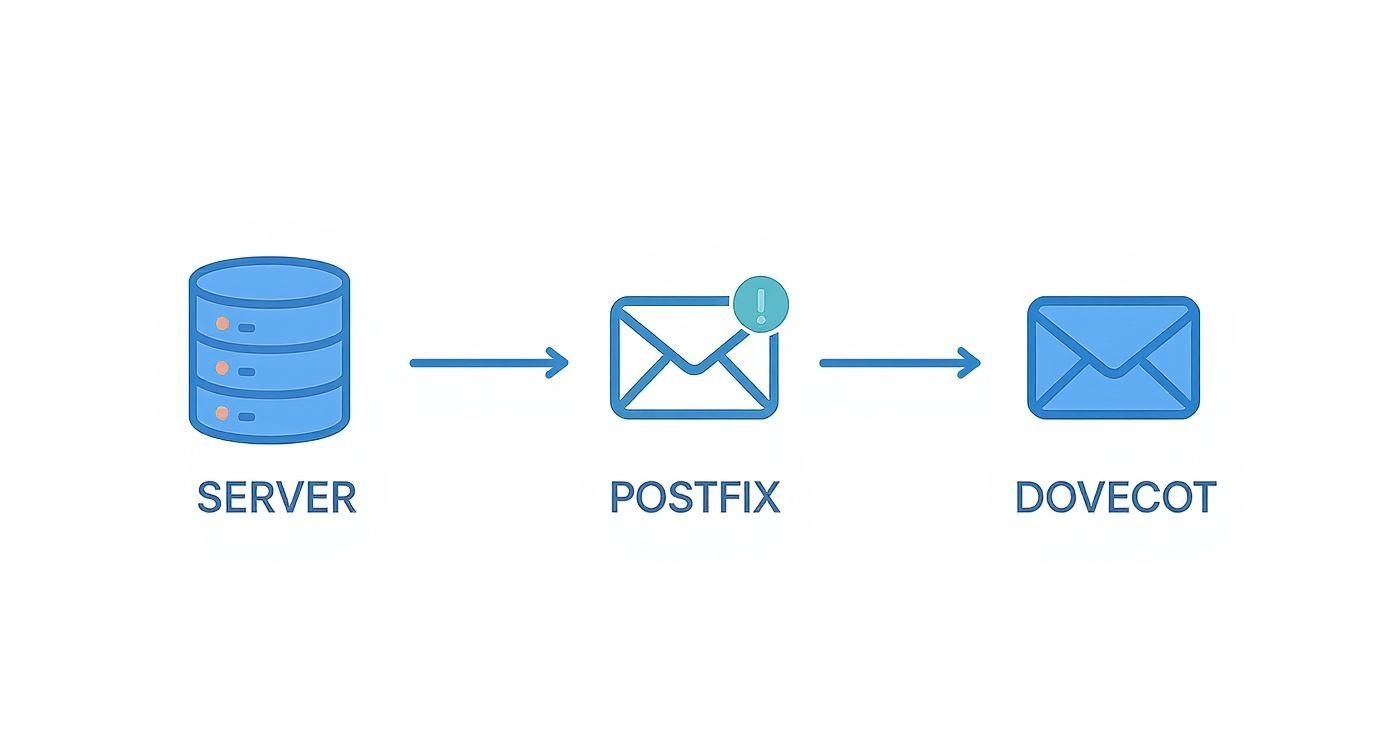
It’s a great visual of how these specialized pieces of software cooperate to manage the intricate process of sending and receiving email securely.
Sender Policy Framework (SPF)
An SPF record is a simple TXT record in your DNS that acts as a public guest list. It lists all the IP addresses that are authorized to send email on behalf of your domain. It essentially says, "If an email claims to be from my domain, it should only come from one of these servers."
A common, simple SPF record might look like this:"v=spf1 mx -all"
This tells receiving servers that only the hosts listed in your MX records are permitted to send mail. That -all part is important—it instructs them to reject mail from any other source. Getting this right is your first major win against domain spoofing.
DomainKeys Identified Mail (DKIM)
DKIM takes authentication to the next level by adding a digital signature to every single email you send. It works with a pair of cryptographic keys: a private key that stays on your server, and a public key you publish in your DNS.
Here’s how it works in practice:
- Your server uses its private key to sign the email's headers and body.
- The receiving server finds your public key via a quick DNS lookup.
- It then uses that public key to verify the signature.
A valid signature proves two things: the email is genuinely from your server, and it hasn't been messed with in transit. This builds a tremendous amount of trust. For a deeper dive, check out our real-world guide on how to authenticate email.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
DMARC is the capstone. It sits on top of SPF and DKIM and gives you control by telling receiving servers what to do if an email fails either of those checks. Your DMARC policy, another TXT record, lays down the law.
You can set policies like:
p=none: Just monitor what's happening and send reports. Great for starting out.p=quarantine: Tell servers to send any failing emails to the spam folder.p=reject: The strictest policy. Block failing emails from being delivered at all.
DMARC also provides invaluable reports, giving you feedback on who is sending email from your domain. This helps you spot abuse and dial in your security. Putting all three—SPF, DKIM, and DMARC—in place is the absolute gold standard for email deliverability and security today.
Hardening Your Email Server Security

Alright, your server is up, the core software is humming along, and you’ve got the basics of deliverability dialed in. Now comes the part where we shift from building to fortifying. When you host an email server, you're not just a sysadmin; you're the guardian of its integrity. This is where we turn a functional machine into a hardened fortress to protect your data and the privacy of everyone you correspond with.
The most critical layer of defense is encryption. Think of unencrypted email as a postcard—anyone who gets their hands on it can read it. We’re going to shut that down by enforcing TLS (Transport Layer Security) for everything. It's non-negotiable for private, secure communication.
Enforcing End-to-End Encryption with TLS
Forcing all connections to be encrypted is a fundamental step for both email privacy and security. Thankfully, this is no longer a costly or complex task. Tools like Let's Encrypt give you free, trusted TLS certificates, making it accessible to everyone. The objective here is simple: configure Postfix and Dovecot to flat-out refuse any connection that isn't encrypted.
This means that whether your email client is fetching mail or another server is trying to deliver mail, the entire conversation is scrambled. No more passwords or message content zipping across the internet in plain text.
By forcing TLS on all connections, you eliminate the risk of man-in-the-middle attacks where an eavesdropper could intercept and read your communications. It’s a simple change that massively boosts your security posture.
This is a key part of building a trusted communication channel. You can find more details in our complete secure email server guide to build bulletproof email systems, which explores encryption and other advanced security measures.
Building Your Anti-Spam and Antivirus Defenses
A server that’s constantly bombarded with junk mail and phishing attempts isn't just annoying; it's a security risk. Your next line of defense is a robust filtering system to keep the garbage out. We’ll integrate two open-source powerhouses directly into our mail flow:
- SpamAssassin: This thing is the Swiss Army knife of spam filtering. It scrutinizes every incoming email against a huge ruleset, giving each one a spam score. We’ll then tell Postfix to reject or quarantine anything that crosses a score threshold we define.
- ClamAV: This is your antivirus gatekeeper. It scans all attachments for viruses, malware, and other nasty payloads. Any email with a malicious file is stopped dead before it ever has a chance to land in an inbox.
Placing these tools in the delivery path means every single message gets a full security screening before it’s accepted.
Fine-Tuning Your Filters for Accuracy
The real magic of spam filtering isn't just blocking junk; it's doing so without dropping important emails into the void (what we call "false positives"). This is where self-hosting really shines. SpamAssassin is incredibly tunable, letting you adjust the "weight" of its rules to match the kind of email you normally receive.
For instance, if you're in finance, emails with terms like "invoice" or "wire transfer" might trigger generic spam rules. With your own server, you can simply lower the score for those specific rules to ensure legitimate messages get through. This level of customization helps you strike the perfect balance—a pristine inbox without the frustration of missed communications.
The Long Haul: Mastering Server Maintenance
Getting your server up and running is a huge milestone, but the real journey is just beginning. To successfully host your own email long-term, you have to embrace the discipline of ongoing maintenance. This isn't just a list of chores to check off; it's a professional mindset—the kind required to keep your private communication channel reliable, secure, and healthy for the long haul.
Think of your server as a living system that needs regular care. The most fundamental part of that care is applying software updates. Security holes are discovered all the time, and failing to patch your system promptly is like leaving your front door wide open. Most Linux distributions make this pretty straightforward, but it's on you to check for and apply those patches consistently.
Finding a Practical Maintenance Rhythm
A random, "I'll get to it when I get to it" approach to maintenance is a surefire way to run into trouble. The key is to build a predictable schedule for the most important tasks. Turn them into habits, not emergency reactions.
Here’s a simple, practical checklist to get you started:
- Weekly Updates: Set aside a specific time each week to run all security and software updates. This is your best defense against the latest threats.
- Daily Log Checks: Spend just a few minutes each day scanning your mail server logs. This is your number one diagnostic tool.
- Monthly Backup Tests: Never just assume your automated backups are working. Once a month, actually perform a test restore of a small mailbox or a key configuration file to prove your data is recoverable when you need it.
Your server logs are like a security camera system. Most days, you'll see nothing out of the ordinary. But when something is wrong—like a hundred failed login attempts from a single IP—the logs give you the evidence you need to act before it becomes a full-blown breach.
This proactive schedule is the foundation for maintaining both your email security and email privacy.
Making Sense of Logs and Staying Up-to-Date
Diving into logs can feel intimidating at first, but you're really just looking for patterns that scream "trouble." Beyond the obvious failed logins, keep an eye out for unusual delivery bounces, strange error messages from Postfix or Dovecot, or a sudden, unexplained spike in CPU or memory usage. These are often the earliest signs that an account has been compromised or something is misconfigured.
Finally, remember that the world of email is always changing. New security standards are adopted, and best practices evolve. Part of your commitment to self-hosting is staying informed. This means occasionally reading up on changes to standards like DMARC or new TLS protocols. Running a private, secure email server isn't a "set it and forget it" project. It's a continuous process of learning and adapting to keep your communications protected.
Common Questions About Hosting Email
Diving into self-hosting your own email server is a big step, and it's totally normal to have a few questions before you start. Taking back control of your email privacy is a rewarding journey, but it definitely has a learning curve. Let's tackle some of the most common things people wonder about.
Is It Cheaper to Host My Own Email Server?
At first glance, yes, it can look that way. A cheap VPS might only cost a few dollars a month, which seems like a steal compared to a premium plan from a hosted email platform.
But that's not the whole story. The real cost is your time. You have to factor in the hours spent on the initial setup, the ongoing maintenance, and the inevitable late-night troubleshooting sessions. For one person, a good privacy-first hosted service is almost always a better deal. For a small team or a group of tech-savvy friends, you might save some money in the long run, but only if you don't mind the time commitment.
What Is the Biggest Challenge for New Self-Hosters?
Deliverability. Hands down, this is the number one headache you'll face.
The big hosted email platforms like Gmail and Outlook are incredibly skeptical of new, unknown servers. Your server's fresh IP address has zero reputation, meaning your first emails are almost guaranteed to land in the spam folder or get rejected outright. You have to nail your SPF, DKIM, and DMARC records, but even then, it's a slow grind to build up a good sending reputation.
The thing about self-hosting is that you're not just a server admin; you're a reputation manager. Every single setting affects whether the rest of the world sees your emails as legitimate.
Can I Use My Home Internet to Host an Email Server?
I'm going to give that a hard no. It’s a really bad idea for a few key reasons.
Most home internet providers block port 25, which is the port used for sending email, specifically to stop their networks from being used for spam. On top of that, you're usually stuck with a dynamic IP address that changes and is likely already on a blocklist. Running a server also probably violates your ISP's terms of service. The only real way forward is to get a Virtual Private Server (VPS) from a solid hosting company. That gives you the static IP and network freedom you absolutely need.
If you're weighing the pros and cons and want to see what a managed service looks like, you can learn more about business email solutions to get a better sense of the landscape of hosted email platforms.
If all this sounds like a bit much, but you're still serious about email security and privacy, Typewire is the answer. As a privacy-focused hosted email platform, we manage all the technical headaches for you. You get the control and privacy of your own email domain without having to become a full-time server administrator.
Start your 7-day free trial and see what a truly private inbox feels like at https://typewire.com.