Relying on a standard email disclaimer for HIPAA to achieve compliance is a common, but dangerous, mistake. Real compliance goes far beyond a block of text at the bottom of your emails; it demands a full strategy built on a secure, hosted email platform that provides end-to-end encryption. A simple confidentiality notice offers no real email privacy and can’t technically protect Protected Health Information (ePHI).
Why Your Disclaimer Isn't Enough for HIPAA
So many organizations think that slapping a confidentiality notice into their email signature is all it takes to be HIPAA compliant. It’s a huge misconception that overlooks the core principles of email security and privacy.
While a disclaimer is a good-faith effort and can act as a warning, it provides absolutely zero technical protection for the data itself. Imagine putting a "Fragile" sticker on a glass box and then shipping it without any padding. The warning is there, sure, but it won't stop the contents from shattering. The same applies to email privacy; a notice doesn't stop interception.
The real problem is with standard email services. Free or consumer-grade versions of platforms like Gmail or Outlook just weren't built with healthcare-level security in mind. They don't typically offer end-to-end encryption by default, which means a message containing sensitive patient data could be read by unauthorized parties while it's traveling across the internet or sitting on a server. This is a fundamental violation of email privacy.
The Real Risks of Unsecured Email
This isn't just a theoretical threat—unsecured email is a leading cause of security incidents in healthcare. It's a sobering fact, but a staggering 95% of all healthcare security breaches are tied back to email. That number alone should tell you everything you need to know about its inherent risks for handling ePHI.
The gap between what people think a disclaimer does and what it actually does creates a massive compliance risk. Trusting a disclaimer means you're ignoring the technical safeguard requirements spelled out in the HIPAA Security Rule.
True compliance and email security are about building layers of protection:
- Secure Hosted Email: You absolutely need to use a hosted email platform that prioritizes security, will sign a Business Associate Agreement (BAA), and offers serious privacy features.
- Encryption: All emails containing ePHI must be encrypted, both while they're in transit and when they're stored, to ensure confidentiality and privacy.
- Access Controls: You have to control who can see or send patient information. It’s that simple.
- Employee Training: Your staff is your first line of defense. They need to be trained on secure email practices and the importance of patient privacy.
A HIPAA-compliant email disclaimer is part of your risk management strategy, not a security solution. Its real job is to warn recipients, give instructions if an email is misdelivered, and show you're trying to do the right thing. It can't replace the technical safeguards needed to actually secure ePHI.
It's easy to get tangled up in the myths surrounding email disclaimers and what HIPAA actually requires. Let's clear a few things up.
Disclaimer Myths vs. HIPAA Reality
There's a lot of confusion out there. Here's a quick look at what people often believe versus what HIPAA actually demands for secure communication and email privacy.
| Common Myth | HIPAA Reality |
|---|---|
| "A disclaimer makes my email HIPAA-compliant." | False. A disclaimer offers no technical protection. HIPAA's Security Rule requires technical safeguards, like encryption, to protect ePHI in transit and ensure privacy. |
| "As long as I have a BAA with my email provider, I'm covered." | Not quite. A BAA is essential, but you still have to configure your hosted email platform correctly (e.g., enable encryption) and train your staff on its proper use for email security. |
| "My free Gmail account is secure enough if I add a disclaimer." | Absolutely not. Standard, free email accounts are not inherently HIPAA-compliant and typically lack the necessary security controls, privacy guarantees, and encryption for handling ePHI safely. |
| "If an email is sent to the wrong person, my disclaimer protects me legally." | It might help show good faith, but it doesn't absolve you of responsibility for a breach. You are still accountable for safeguarding the data and protecting patient privacy under HIPAA. |
Ultimately, relying on these myths creates a false sense of security that can lead to serious breaches, privacy violations, and costly penalties.
Moving Beyond Disclaimers to True Security
At the end of the day, a disclaimer is a legal and administrative tool, not a technical one. It’s a piece of the puzzle, but it’s not the whole picture of email security.
To get a much deeper understanding of what real compliance involves, our complete guide is a great place to start: https://typewire.com/blog/read/2025-06-24-hipaa-compliance-for-email-your-complete-security-guide
True email security requires robust technical solutions, like automatically encrypting or blocking outbound communications that contain sensitive data. Without that kind of foundational security from a hosted email platform, even the most perfectly worded email disclaimer for HIPAA is just an empty promise.
Crafting a Disclaimer That Actually Works
Let's be clear: a HIPAA email disclaimer isn't a magic force field. It won't single-handedly stop a data breach or guarantee email privacy. Think of it more like a crucial part of your overall risk management strategy—a clear, firm set of instructions designed to minimize the fallout when an email inevitably goes astray.
The real goal here is to communicate, not intimidate. You want to immediately signal that the email contains sensitive information, establishing a clear line of responsibility the moment it lands in someone's inbox. Moving beyond a generic, copy-pasted block of text is the first step.
The Core Components of a Strong Disclaimer
A well-built disclaimer is doing several jobs at once. Each piece has a specific purpose, guiding how the recipient should handle the information and showing that your organization is serious about protecting ePHI and patient privacy.
Here’s a breakdown of what every effective disclaimer needs:
- Confidentiality Notice: This is your foundation. It needs to state, without ambiguity, that the email contains confidential and potentially legally privileged information, including Protected Health Information (ePHI).
- Intended Recipient Statement: Make it crystal clear who the message is for. A simple line stating the email is intended only for the addressee removes any doubt if it's accidentally forwarded or misaddressed.
- Prohibition of Unauthorized Use: This clause is your stop sign. It explicitly warns against sharing, copying, or distributing the email’s contents without permission.
- Instructions for Misdelivery: This is arguably the most critical component because it’s a direct call to action. Tell the person exactly what to do if they received the email by mistake.
Your disclaimer's real power is in its clarity. Ditch the dense legalese for plain English that anyone can understand. The objective is to instruct, not to sound like a lawyer.
The risk of a simple email mistake spiraling into a significant compliance issue is very real. This visual breaks down how quickly an unencrypted email can become a reportable incident.
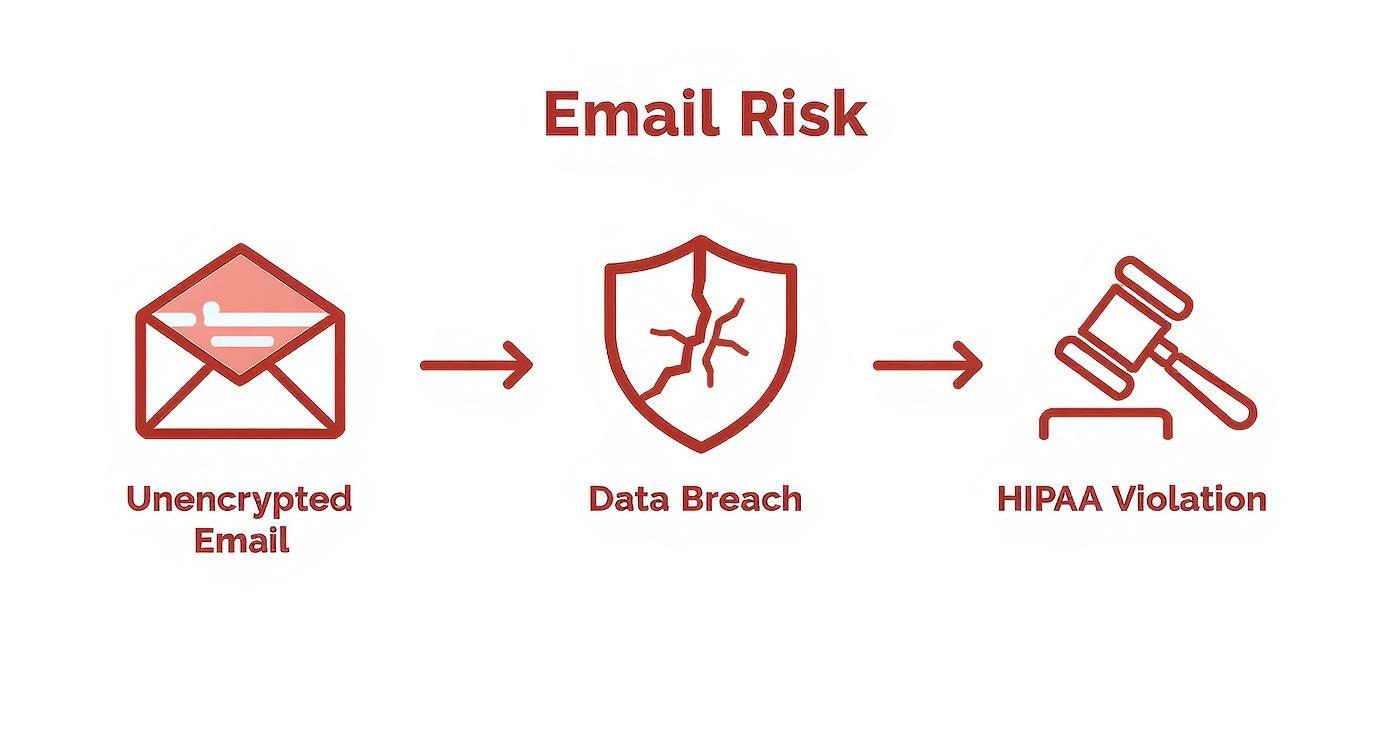
Seeing the direct line from an unencrypted message to a HIPAA violation really drives home why every layer of protection matters. Your disclaimer acts as a final, critical instruction at the point of potential exposure.
From Theory to Practice: Real-World Examples
How you phrase your instructions matters immensely. I've seen disclaimers that actually make a breach worse. For example, asking someone to "reply to this email" if they aren't the intended recipient is a terrible idea—they might just re-transmit the very ePHI you're trying to contain by hitting "reply all."
Your goal is to stop the data from spreading and protect patient privacy, not to keep the conversation going on a compromised channel.
Here’s a much safer approach for misdelivery instructions:
"If you have received this email in error, please notify the sender immediately by telephone and permanently delete this message and any attachments from your system. You are prohibited from reading, copying, or distributing this message."
This is a much better instruction. Why? It shifts the communication to a secure channel (the phone) and directs the person to delete the data, effectively containing the potential breach. It’s these thoughtful details that make an email disclaimer for HIPAA a genuinely useful tool.
How State Consent Laws Throw a Wrench in Your Email Strategy
Just when you think you’ve got federal HIPAA rules figured out, you have to contend with state-specific privacy laws. This is where things get tricky, because these state regulations often set a higher bar for patient consent. For any practice that serves patients in more than one state, this adds a whole new level of complexity to email communications.
Frankly, a one-size-fits-all email disclaimer just doesn't cut it anymore. What passes for compliant in one state might be a clear violation in another, and that’s a risk no one can afford to take. It's a patchwork of rules that demands your full attention to email privacy.
The Shift to "Opt-In" Consent
The biggest change we're seeing is the move from implied consent to explicit "opt-in" consent. HIPAA generally permits emails about treatment, payment, and healthcare operations. However, a growing number of states are saying, "Not so fast." They require you to get a patient's clear permission before you send them any electronic messages.
This completely changes the game for how you handle patient email lists and outreach. Right now, several states have put these tougher opt-in rules in place. In fact, nine states have already adopted more protective standards that go beyond the federal baseline: Connecticut, Colorado, Texas, Tennessee, Virginia, Utah, Montana, and Iowa, with Indiana coming on board in January 2026. You can find more details on these evolving state requirements over at hipaajournal.com.
Remember, federal law is the floor, not the ceiling. State laws can—and often do—build on top of HIPAA, creating stricter patient protections that you are legally required to follow.
Ignoring these state-level rules is a recipe for compliance trouble. If you operate nationally, your email strategy has to meet the standards of the strictest state you work in. It's a hassle, for sure, but it’s absolutely necessary to protect both patient privacy and your practice.
Practical Steps for State Law Compliance
Staying on the right side of these regulations means you have to be proactive. It's not just about tweaking your email disclaimer for HIPAA; it’s about fundamentally rethinking how you get and track consent.
Here’s what you can do to get your strategy in line with state laws:
- Segment Your Patient Lists by State: Stop lumping everyone together. By organizing your email lists based on where patients live, you can make sure you’re applying the right consent rules to the right people. This is your best defense against accidentally breaking a state’s specific opt-in law.
- Use Crystal-Clear Consent Forms: When you ask for an email address, be direct. Use simple, unambiguous language that spells out exactly what they're agreeing to receive. A pre-checked box is a major no-no in many of these states; the patient has to take a clear, affirmative step to opt in.
- Customize Disclaimers for High-Risk States: While a single, robust disclaimer is a good start, think about adding a sentence or two for patients in states with strict opt-in laws. This can reinforce that you're communicating with them based on their prior consent.
Adapting to these rules is non-negotiable for maintaining patient trust. This is especially true in specialized fields like mental health. For a deeper dive, check out our guide on HIPAA-compliant email for therapists, which offers more targeted advice. At the end of the day, a well-organized and proactive approach is your best shield against compliance violations.
Deploying Disclaimers Across Your Organization

You can craft the most legally sound email disclaimer for HIPAA, but it’s completely useless if it isn't on every single email that leaves your organization. This is where many well-intentioned clinics and practices fall short in their email security strategy.
Relying on individual employees to manually copy and paste a disclaimer into their email signatures is a classic compliance mistake. It’s just not a matter of if it will fail, but when. Someone will inevitably forget, use an old version from a forwarded email, or even try to "fix" the wording themselves.
This kind of inconsistency completely undermines the purpose of the disclaimer, which is to show you're making a consistent, good-faith effort to protect PHI. For real email security, you have to take human error out of the equation. The only reliable way to do that is to deploy the disclaimer automatically at the server level using a secure, hosted email platform.
Centralized Management on Hosted Email Platforms
This is where modern, secure hosted email platforms become your greatest asset. If you’re using a business-grade service like Microsoft 365 or Google Workspace, you already have the tools you need for centralized, automated deployment.
These platforms are designed for this kind of administrative control. You can create what are often called "transport rules" or "mail flow rules." It sounds technical, but it’s really just a simple "if-then" command for your email server.
You can set up a rule that says something like: "If an email is sent from anyone inside our company to anyone outside, then automatically attach this specific disclaimer to the end of the message."
The difference this makes is night and day.
- You get 100% consistency. No exceptions. Every single email gets the same, approved disclaimer.
- It’s tamper-proof. Users can't edit, shorten, or remove the disclaimer. What legal approves is what goes out.
- Updates are instant. Need to change the wording? You update the rule in one central place, and it immediately applies to everyone.
By deploying your disclaimer centrally via your hosted email platform, you're turning it from a hopeful suggestion into an enforced policy. This is a critical administrative control that demonstrates you're serious about the HIPAA Security Rule.
The choice between manual and automated implementation is a crucial one. Let's break down why a centralized system is the only truly viable option for HIPAA compliance.
Disclaimer Implementation Showdown
| Feature | Manual Implementation (Per User) | Centralized Management (Platform Level) |
|---|---|---|
| Consistency | Low. Prone to user error, forgotten disclaimers, and outdated text. | 100%. The same approved disclaimer is applied to every email, every time. |
| Security | Weak. Users can alter or remove the disclaimer, creating legal risk. | Tamper-Proof. Centrally controlled and cannot be modified by the end-user. |
| Management | Inefficient. Requires training and auditing every single user. Updates are slow. | Effortless. Update the rule once, and it instantly applies to the entire organization. |
| Compliance | Risky. Difficult to prove consistent application during a HIPAA audit. | Strong. Provides a clear, auditable trail of consistent policy enforcement. |
As the table shows, relying on individual users introduces far too many variables and risks. A centralized, automated approach isn't just easier—it's a fundamental part of a sound email security and compliance strategy.
Best Practices for Disclaimer Placement
Automating your disclaimer is step one, but how it appears is just as important. We've all seen those endless email chains where a clunky, full-page legal notice gets tacked onto every single reply.
It’s messy, unprofessional, and makes the actual conversation nearly impossible to follow.
The best practice today is to configure your hosted email system to be a bit smarter. A well-designed rule will add the full legal disclaimer only once, at the very bottom of the entire email thread. Subsequent replies in the same conversation won't keep adding it.
This approach keeps communication clean and professional while ensuring your legal bases are covered. It shows you respect the recipient's time and inbox, which is vital when you're discussing sensitive health information.
Your Email Security Checklist Beyond the Disclaimer

An email disclaimer for HIPAA is a good administrative signal, but let's be honest—it's just the beginning. It's time to look past the signature block and focus on the technical and procedural safeguards that actually protect patient data. A disclaimer won't stop a hacker, and it certainly can't undo a misaddressed email. Only a layered email security strategy can do that.
Relying on a disclaimer as your main defense is like putting a "Beware of Dog" sign on a house with unlocked doors. It offers no real protection for email privacy. True HIPAA compliance requires a secure email environment built on a hosted email platform where the disclaimer is just one small piece of a much larger, more robust system.
Fortifying Your Technical Safeguards
Your first and most important line of defense is always technical. Your organization needs to implement safeguards that actively protect electronic protected health information (ePHI) from unauthorized access, whether it's sitting in an inbox or flying across the internet.
Here are the technical controls I always recommend starting with:
- Mandatory End-to-End Encryption: This is completely non-negotiable. Every single email containing ePHI must be encrypted from the moment it leaves your outbox until the intended recipient opens it. For a deeper dive, check out our essential guide on HIPAA-compliant email encryption.
- Strict Access Controls: Not everyone in your organization needs to see patient data. You must implement role-based access, limiting ePHI visibility strictly to authorized staff who need it to do their jobs.
- Secure Hosted Email Platforms: Using a secure email provider that will sign a Business Associate Agreement (BAA) is critical. Platforms like Typewire are built from the ground up with privacy and security in mind, giving you the compliant infrastructure you need.
A truly secure email system doesn't rely on warnings; it relies on technical enforcement. The goal is to make it incredibly difficult, if not impossible, for sensitive data to fall into the wrong hands, even when human error occurs.
With the technology in place, you then need to manage the human side of the equation.
Strengthening Your Administrative and Physical Controls
Even the most advanced technology can be defeated by a simple mistake. This is precisely why ongoing training and crystal-clear policies are just as vital as encryption. One of the most common—and costly—mistakes is simply sending an email to the wrong person.
Email misdelivery is a surprisingly huge source of healthcare data breaches, accounting for roughly 8% of all breaches reported to the HHS Office for Civil Rights. That translates to thousands of incidents every year, many from preventable mistakes. For example, failing to use the Blind Carbon Copy (BCC) feature when emailing a group of patients is still one of the most common HIPAA violations we see.
To fight back against these human-centric risks, your email security checklist must include:
- Ongoing Phishing and Security Training: Regularly train employees to spot phishing attempts, understand the critical importance of using BCC, and always double-check recipient addresses before hitting "send."
- Data Minimization Policies: Instill a "less is more" mindset. Enforce a strict policy of only including the absolute minimum necessary ePHI in any email.
- Secure Device Policies: Make sure all devices used to access ePHI—including personal phones and laptops—are properly secured with strong passwords, screen locks, and remote wipe capabilities.
Moving beyond just disclaimers, a solid strategy for HIPAA compliant data transfer is what truly protects electronic protected health information (ePHI). This holistic view, which combines strong technology with vigilant human oversight, is the only way to build a truly compliant and secure email strategy.
Common Questions About HIPAA Email Disclaimers
Trying to get your HIPAA email disclaimer right often brings up a lot of practical, real-world questions. It's easy to get bogged down in the details. Let's cut through the confusion and tackle some of the most common questions with quick, straightforward answers.
Does a Disclaimer Make My Standard Gmail Account HIPAA Compliant?
No, and it's not even close. This is probably one of the most dangerous myths I see. A disclaimer is just text—it has no technical power to secure your data or ensure email privacy.
To be truly HIPAA compliant, you have to use an email service that will sign a Business Associate Agreement (BAA) with you. This is a non-negotiable contract where the provider legally commits to protecting PHI according to HIPAA’s rules. The service itself must also offer critical security features, most importantly end-to-end encryption.
A standard, free Gmail or Outlook account just doesn't cut it for handling ePHI. Your disclaimer, no matter how perfectly written, can't change that fundamental fact.
Where Is the Best Place for a Disclaimer in an Email Chain?
We’ve all been on those email chains where every single reply has the same long legal notice pasted at the bottom. It’s a mess, it's hard to read, and it looks unprofessional.
The modern and much cleaner approach is to configure your hosted email platform to be smarter. You can set it to add the disclaimer just once—at the very bottom of the entire email thread. This keeps the conversation flowing smoothly while ensuring the full legal notice is always attached to the message for anyone who gets looped in.
Pro Tip: A well-placed disclaimer shows respect for the recipient's time and inbox. Adding it once per thread maintains professionalism and clarity without sacrificing your compliance documentation. It's a small tweak that makes a huge difference.
Can a Disclaimer Legally Protect Me from a HIPAA Violation?
A disclaimer won't give you a get-out-of-jail-free card for a HIPAA violation. It’s better to think of it as a crucial piece of your "good faith" effort to stay compliant, not as a legal shield that negates a lack of email security.
What it does do is show regulators that you have policies in place and are actively warning people about confidential information. It also gives an unintended recipient clear instructions on what to do, which can help minimize the damage from a potential breach. But it will never excuse you from your core duty to technically secure ePHI or to report a breach if one happens.
Are There Specific Words I Have to Include for HIPAA?
HIPAA doesn't give you a script. The law is more concerned with the disclaimer’s function and clarity than with specific legal jargon.
That said, any effective disclaimer needs a few key elements to communicate the message clearly. You should always include phrases that get the point across, like:
- "This email may contain confidential and privileged information."
- "Intended for the recipient named above only."
- "Unauthorized use, disclosure, or distribution is strictly prohibited."
The most critical part is providing simple, actionable instructions. Tell people exactly what to do: "notify the sender immediately by telephone" and "permanently delete this email if you are not the intended recipient." Your goal is to leave absolutely no room for doubt.
Ready to move beyond disclaimers and build a truly secure email foundation? Typewire provides private, secure email hosting built on an infrastructure that prioritizes your privacy and control. With end-to-end encryption and a commitment to zero tracking, we give you the tools to communicate with confidence. Start your free trial and experience secure email.