Think of sending a standard email like sending a postcard. As it travels across the internet, anyone from your email provider to a hacker on a public Wi-Fi network could potentially read its contents. To truly secure your information, you need to go a step further.
You can either encrypt the email itself or password-protect the sensitive files you attach to it. Let's break down why this is so crucial and how you can start doing it.
Why Your Standard Email Isn’t Private

It’s easy to think of your inbox as a private digital vault, but that's a risky assumption. Without extra security, your emails are surprisingly exposed. Each message hops between multiple servers on its way to the recipient, creating several points where a determined attacker could intercept it.
You wouldn't mail your bank statements or a confidential contract on a postcard for the world to see, right? It's time we started treating our emails with that same level of caution. This is why knowing how to protect an email with password security is a practical skill everyone needs, not just a niche practice for the overly paranoid.
The Real Risks of Unsecured Messages
These threats aren't just hypotheticals—they have real-world consequences. Opportunistic hackers and targeted attacks can exploit these vulnerabilities in several ways:
- Data Breaches: If a company you've corresponded with suffers a breach, your private emails could be exposed.
- Man-in-the-Middle Attacks: Cybercriminals can intercept and read your messages on unsecured networks, like the Wi-Fi at a coffee shop.
- Phishing and Account Takeover: A single weak password can make your entire email account—and all the sensitive data inside it—a prime target.
Compromised passwords are still one of the biggest threats out there. Recent data shows that almost half (46%) of people have had at least one password stolen. What’s more, 35% of those thefts happened because of weak passwords, and another 27% were due to company data breaches. This really drives home how our personal habits and the security of the services we use both play a massive role. You can find more of these eye-opening password statistics and safety tips in this report.
The goal isn't to scare you, but to make you aware. The simple fact is that standard email has weak spots. Understanding this is the first and most important reason why adding a layer of password protection is essential for any sensitive information you send.
Lock Down Your Attachments with a Password
Sometimes the simplest solution is the best one. If you just need to send a single sensitive file, one of the easiest ways to protect it is to password-protect the attachment itself. Think of it as putting the document in a digital safe before you even attach it to the email.
This is my go-to method for sending things like signed contracts, tax forms, or other financial records. You're not encrypting the whole email, just the sensitive payload. The best part? You likely already have all the tools you need.
How to Add a Password to Different File Types
You don't need fancy software to do this. Most common programs have password protection built right in, and it usually only takes a few clicks.
Here's a quick rundown for the most common file types:
- For PDFs: If you have Adobe Acrobat, just open the file and head to File > Protect Using Password. You'll get an option to set a password required to open the document—that's the one you want.
- For Microsoft Office Docs: In Word or Excel, the path is File > Info > Protect Document > Encrypt with Password. Pop in a strong password, and you're all set. If you're deep in the Microsoft ecosystem, our complete guide to securing Outlook emails has even more tips.
- For ZIP Archives: Got a folder full of files? Zip them up. On Windows, right-click your files, choose Send to > Compressed (zipped) folder, then open that new ZIP file and find the option to add a password under the File menu. On a Mac, you can do this through the Terminal or with a simple third-party app.
As you can see in this screenshot from Adobe Acrobat, the process is incredibly straightforward.

You get a clear choice to require a password just for viewing the file, which is exactly what we need for a secure email attachment.
The Golden Rule: Never, ever send the password in the same email as the attachment. It’s the digital equivalent of taping the key to the front door.
So, how do you share the password? Use a completely different channel. A quick phone call, a text message, or a secure messaging app like Signal works perfectly. By separating the lock (the file) from the key (the password), you ensure that even if the email gets intercepted, the attachment is still just a useless, encrypted file to anyone else.
Sending password-protected attachments is a decent short-term fix, but it's not a sustainable strategy if you regularly handle sensitive information. Constantly zipping and encrypting files gets old fast. For a much more streamlined and robust solution, you should seriously consider moving to a dedicated secure email provider.
Companies like ProtonMail and Tutanota have built their entire platforms around privacy and security. Unlike mainstream services where security can feel like an add-on, for them, it's the main event.
These services rely on end-to-end encryption. Think of it as an unbreakable, digital-sealed envelope. Your message gets scrambled the second you hit "send" and can only be unscrambled by the intended recipient. Crucially, no one in the middle—not your ISP, not even the email company—can decipher what's inside. It's a fundamental shift from how standard email works.
How Secure Email Providers Talk to Regular Inboxes
So, what happens when you send a secure message to someone still on Gmail or Outlook? This is where the magic happens.
Your recipient won't see your message pop up in their inbox. Instead, they’ll get a simple notification email containing a secure link. Clicking that link opens a private, encrypted web page where they'll need to enter a password you've shared with them beforehand (over the phone or via a secure messaging app, for instance). This neatly extends a cloak of privacy over the entire conversation, even when the other person isn't on the same platform.
While we're talking about passwords and security, it's a good time to remember the importance of protecting your own account, not just the messages you send. Multi-factor authentication is your best defense.
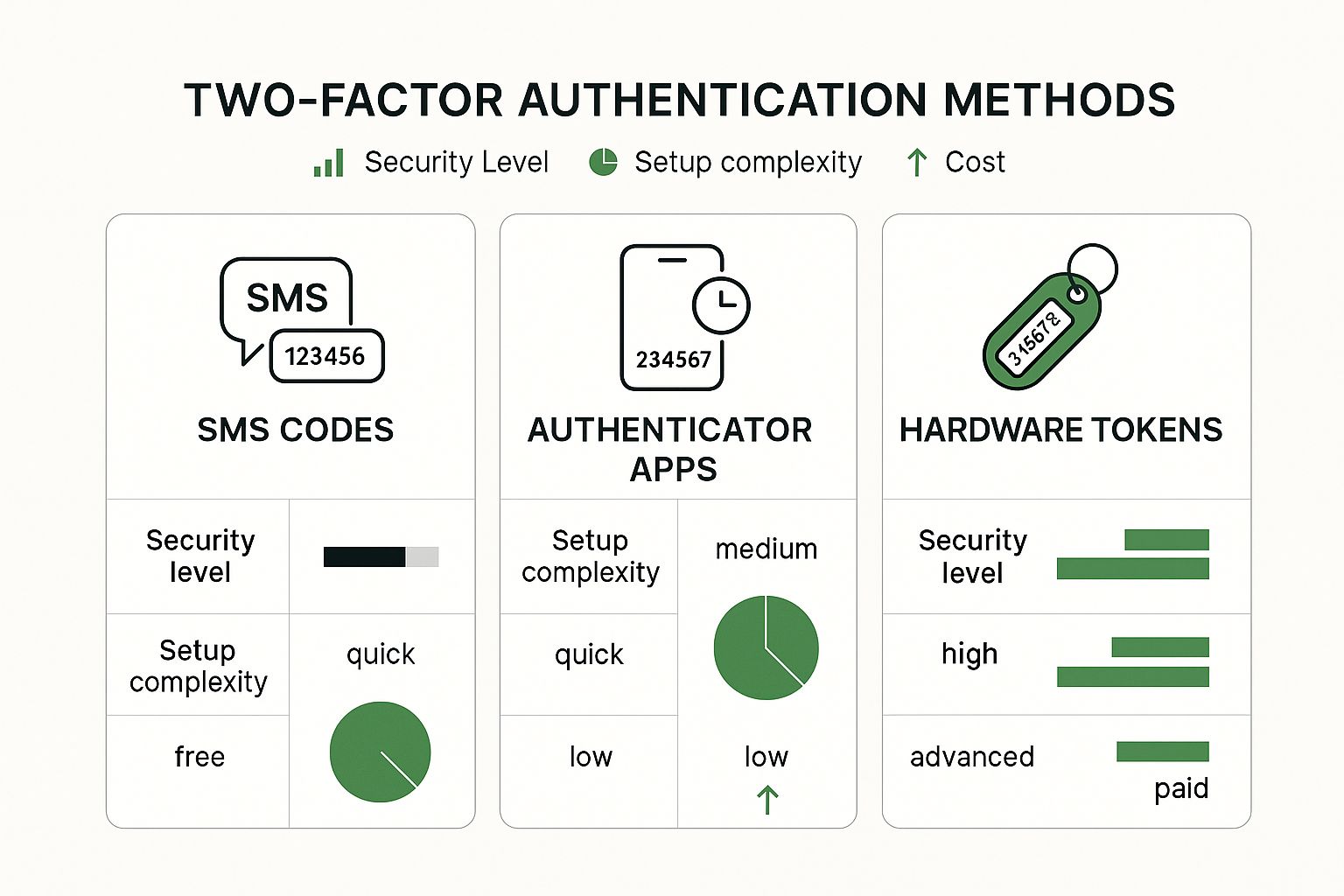
As you can see, there's a clear trade-off between convenience and security. Choosing the right method depends entirely on what you're trying to protect.
More Than Just Encryption
These privacy-focused email services usually come loaded with extra tools that give you more control over your communications. They go far beyond just basic encryption.
- Self-Destructing Emails: A great feature for highly confidential information. You can set a timer, and after it expires, the email automatically vanishes from the recipient's inbox.
- Anonymous Sign-Ups: Most don't ask for personal information when you create an account, which adds another layer of anonymity.
Even with these powerful tools, the human element is often the weakest link. It’s pretty shocking to learn that over 36% of people still write their passwords down on paper. And in 36% of cloud breaches, attackers got in simply by using stolen—but valid—credentials. These figures, highlighted in a report on password security challenges and statistics, underscore why good habits are just as important as good software.
Key Takeaway: Switching to a secure provider makes high-level encryption the default setting for your communication. It’s a proactive, set-it-and-forget-it approach for anyone regularly dealing with sensitive data who wants privacy without the hassle.
Comparing Email Security Methods
To help you decide which path is right for you, let's break down the different methods we've discussed. Each has its place, depending on your specific needs for security, convenience, and technical comfort.
| Method | Best For | Security Level | Ease of Use |
|---|---|---|---|
| Password-Protected Attachments | Sending occasional sensitive files to any email address. | Moderate: Protects the file, not the email body. | Moderate: Requires manual steps for sender and recipient. |
| PGP/GPG Encryption | Tech-savvy users needing maximum security and control. | Very High: The gold standard for encryption. | Low: Steep learning curve and requires key management. |
| Secure Email Provider | Everyday secure communication and protecting all messages by default. | High: Seamless end-to-end encryption. | High: Works just like regular email, but with built-in privacy. |
Ultimately, the best method is the one you'll actually use consistently. For most people who want a simple yet powerful way to protect their digital conversations, a secure email provider offers the perfect balance of security and usability.
Taking Email Security to the Next Level with PGP

When you need to go beyond just password-protecting a file and lock down the entire email itself, it’s time to look at PGP. Pretty Good Privacy, or PGP, is the industry standard for serious email encryption. It's the tool of choice for journalists, activists, and anyone who simply cannot afford for their communications to be intercepted.
While the name sounds a bit technical, the concept is straightforward. PGP operates on a system known as public-key cryptography. Think of it like having a personal mailbox with two different keys.
- Public Key: This is like the mail slot on your mailbox. You can give copies of this key to everyone. They can use it to drop a message into your box, but they can't open the box or see what's inside.
- Private Key: This is your personal, secret key. It's the only key in the world that can open your mailbox and retrieve the messages. You never, ever share this one.
This two-key system is what makes PGP so powerful. Even if someone manages to snatch your email in transit, all they'll see is a block of unreadable, scrambled text. Without your private key, it’s completely useless.
How to Get Started with PGP
The first step is usually to integrate PGP into your current email client, whether you use Outlook, Thunderbird, or Apple Mail. You’ll need a specific tool to handle the encryption. A couple of popular, long-standing options are Gpg4win for Windows users and GPG Suite for Mac.
Once you have the software installed, the workflow generally follows these steps:
- Create Your Keys: You'll start by generating your unique key pair—one public, one private. During this process, you’ll create a strong passphrase to protect your private key. Think of it as the master password for your entire setup, so make it a good one.
- Exchange Public Keys: To communicate securely with someone, you need their public key, and they need yours. You'll typically email your public key file to them, and they'll import it into their PGP software.
- Encrypt Your Message: Now, when you compose a message to that person, you'll select their public key from a dropdown menu. Your software then scrambles the message content before it even leaves your outbox.
When you receive an encrypted email, your PGP tool will automatically detect it. It will then prompt you for your passphrase, use your private key to decrypt the message, and reveal the original text. For a more detailed walkthrough of this and other methods, our guide on sending secure emails provides a complete protection playbook.
PGP offers rock-solid, military-grade security, but it's not a "flick of a switch" solution. It has a bit of a learning curve and, crucially, requires both you and your recipient to be using it. This makes it ideal for specific, high-stakes communication rather than your daily back-and-forth.
Creating Passwords That Actually Protect You
An encrypted email is only as secure as the password that locks it down. If you want to understand just how high the stakes are, look no further than the aftermath of major data breaches. One recent analysis of compiled leaks uncovered a mind-boggling 16 billion stolen credentials.
What's really worrying is that deep dives into these breaches consistently find that a staggering 94% of passwords get reused across different accounts. This one simple mistake is a security nightmare, turning a single compromised login into a domino effect that can give an attacker the keys to your entire digital kingdom. You can explore more on these password breach findings to see the full, sobering picture.
Adopt Modern Password Hygiene
Forget the old advice about just swapping a letter for a symbol and adding a number. In today's world, real password strength comes from length and uniqueness, not just complexity.
Here’s what works now:
- Use a Password Manager: This is non-negotiable for serious security. Tools like 1Password or Bitwarden generate and remember long, random passwords for every single one of your accounts. You only need to remember your one master password.
- Embrace Passphrases: A long, memorable phrase is exponentially stronger than a short, complex password. For example, "blue-guitar-sings-loudly-at-midnight" is far more secure and easier to remember than something like
P@ssw0rd1!.
Key Takeaway: The single most impactful step you can take right now is to turn on two-factor authentication (2FA) for your email account. It adds a critical second layer of verification, making a stolen password practically useless to a hacker.
Ultimately, your journey to better email security starts with building a solid password foundation. Our complete guide on how to password protect an email now walks you through several other effective methods.
Common Questions About Email Security
Even with the best tools in hand, you're bound to have a few lingering questions about how password protection works in the real world. Let's dig into some of the most common ones I hear.
Can I Password-Protect an Entire Email in Gmail or Outlook?
Unfortunately, no. Standard email services like Gmail and Outlook don't have a built-in feature for slapping a password on the entire email message itself.
That said, you do have workarounds. Gmail offers a "Confidential mode" that adds some basic restrictions, and both platforms let you password-protect individual attachments (like a Word doc or PDF) before you hit send.
What's the Best Way to Share the Password?
Whatever you do, never send the password in the same email as the file. That's like locking your front door and leaving the key under the mat—it completely defeats the purpose.
The only safe way is to use a totally different communication channel. I always recommend one of these options:
- A quick phone call or text message.
- An encrypted messaging app like Signal.
By separating the encrypted file from its password, you create a significant barrier for anyone trying to intercept your information. Even if they get the email, the attachment remains securely locked without the separate key.
Is Switching to a Secure Email Provider Worth It?
If you regularly handle sensitive information—whether for business or personal reasons—then absolutely. Making the switch is one of the smartest moves you can make for your digital privacy.
Providers like ProtonMail build end-to-end encryption right into the service. This gives you a much higher level of default security without having to mess with manual setups like PGP. It’s a proactive way to ensure your conversations stay private, all the time.
Ready for an email experience that puts your privacy first? At Typewire, we offer secure, private email hosting with zero tracking and no ads. Take control of your communications and see the difference.