In an increasingly connected environment, providing a personal phone number for every new online account has become the norm. While often presented as a security measure, this practice can compromise your privacy by linking your digital identity directly to your real-world one. For many, finding an email without phone number verification is a critical step towards reclaiming digital anonymity and reducing their data footprint. This demand isn’t just about privacy; it’s about control over your personal information and avoiding targeted advertising or potential data breaches.
This guide is designed to help you navigate the options. We’ve compiled a comprehensive list of the best email providers that respect your privacy by not mandating a phone number at signup. Each entry is thoroughly analyzed, covering key features, practical use cases, and honest limitations. You’ll find direct links and screenshots to streamline your decision-making process, ensuring you can quickly identify the service that best fits your specific needs. While avoiding phone verification is a key step, it’s also wise to secure your new account with robust methods; you can learn more about two-factor authentication to understand alternative security layers that don’t rely on your phone number. Let’s dive into the providers that put your privacy first.
1. Proton Mail
Proton Mail is a top-tier choice for anyone seeking a private email without phone number verification. Based in Switzerland, it operates under strict privacy laws and is renowned for its end-to-end and zero-access encryption. This architecture ensures that not even Proton can read your emails, offering a level of security that sets it apart from mainstream providers. The signup process is a key differentiator; it explicitly allows users to verify their identity via a simple CAPTCHA or an alternative email, completely bypassing the need for a phone number.
The platform offers a permanently free plan, which is ideal for individual users, though it comes with storage limitations. Paid plans unlock more features, including custom domains, increased storage, and access to the full Proton privacy suite (VPN, Drive, Calendar). This makes it a scalable solution for both personal use and for businesses that prioritize data security. The user interface is clean and modern, making it easy to navigate for those transitioning from other services.
Key Details
- Pricing: Starts with a robust free plan. Paid plans begin at €3.99/month.
- Verification Method: CAPTCHA or recovery email.
- Unique Offering: Full end-to-end encrypted ecosystem (Mail, Calendar, Drive, VPN).
- Best For: Privacy-conscious individuals and businesses needing a secure, scalable email solution.
Pros & Cons
| Pros | Cons |
|---|---|
| Strong Swiss privacy laws | Free plan has limited storage (1 GB) |
| No phone number required | Advanced features are behind a paywall |
| End-to-end encryption by default | Phone support only for specific business tiers |
For a more in-depth look at its features, you can learn more about Proton Mail and similar services.
Website: https://proton.me
2. Tuta (formerly Tutanota)
Tuta is another Germany-based powerhouse for private email without phone number verification. It is built on a foundation of open-source, end-to-end encryption that covers not just emails but also its calendar and contacts. Tuta has a strong public commitment to user anonymity, explicitly stating that a phone number is never required to create an account. For maximum privacy, users can even sign up over the Tor network, making it a go-to choice for those needing to protect their identity.
The platform provides a generous free plan suitable for personal use, though it has some feature limitations. A key point to note is that new free accounts may undergo a manual approval process lasting up to 48 hours to prevent abuse. Upgrading to a paid plan removes this waiting period and unlocks additional benefits like custom domains and increased storage. Tuta also supports privacy-centric payment methods, including Bitcoin, Monero, and even cash, further reinforcing its dedication to user anonymity.
Key Details
- Pricing: A capable free plan is available. Paid plans start at €3/month.
- Verification Method: No personal information required; new accounts may be reviewed.
- Unique Offering: End-to-end encrypted calendar and contacts, plus privacy-focused payment options.
- Best For: Activists, journalists, and anyone requiring maximum anonymity in their communications.
Pros & Cons
| Pros | Cons |
|---|---|
| Strong commitment to anonymous sign-up | New free accounts may face a 48-hour approval hold |
| Open-source and fully encrypted | Fewer third-party integrations than mainstream providers |
| Accepts Bitcoin, Monero, and cash payments | No IMAP/POP3 support for third-party clients |
Website: https://tuta.com
3. Typewire
Typewire is a Canadian-based email provider designed for users seeking a private email without phone number verification while prioritizing data sovereignty and simplicity. Operating under Canada’s strict privacy laws (PIPEDA), Typewire offers a straightforward alternative to Big Tech email providers that scan messages for advertising. The signup process respects user privacy, requiring only an email address for verification–no phone number needed. This makes it an accessible option for individuals and businesses who want to reclaim control over their communications.
The platform stands out for its zero-access encryption architecture, meaning that even Typewire staff cannot read your messages. Unlike providers that rely on third-party cloud infrastructure, Typewire owns and operates its own data center in Vancouver, BC, ensuring your data never leaves Canada and remains protected from foreign surveillance laws. The service is entirely ad-free and includes robust spam filtering, IMAP/SMTP support, and mobile apps for both Android and iOS. Custom domain support (up to 5 domains) makes it particularly appealing for businesses wanting professional, branded email addresses.
Key Details
- Pricing: Starts at CA$0.80/month for the Starter plan. Premium plans begin at CA$7.91/month per user.
- Verification Method: Email address only–no phone number required.
- Unique Offering: Privately-owned Canadian infrastructure with zero-access encryption and full data sovereignty under Canadian privacy laws.
- Best For: Privacy-conscious Canadians, businesses requiring data residency compliance, and anyone seeking a straightforward email solution without Big Tech surveillance.
Pros & Cons
| Pros | Cons |
|---|---|
| Zero-access encryption with Canadian data sovereignty–your emails stay private under PIPEDA protection | Email-focused service without integrated calendar, VPN, or productivity suite |
| Ad-free experience with no message scanning for advertising or data mining | Starter plan limited to 50 emails/day (Basic and Premium plans have unlimited sending) |
| Affordable and straightforward–custom domain support | Limited to Canadian data center location (no server choice in other regions) |
Website: https://typewire.com/
4. StartMail
StartMail is a premium, privacy-focused service from the creators of the Startpage search engine. It provides a secure email without phone number verification, operating under strong Dutch privacy laws. The signup process is designed for anonymity, requiring only a recovery email or a secure recovery key, ensuring you can create an account without tying it to your personal phone number. It’s built on the principle of user-owned data, meaning it never reads your emails or tracks your activity for advertising purposes.
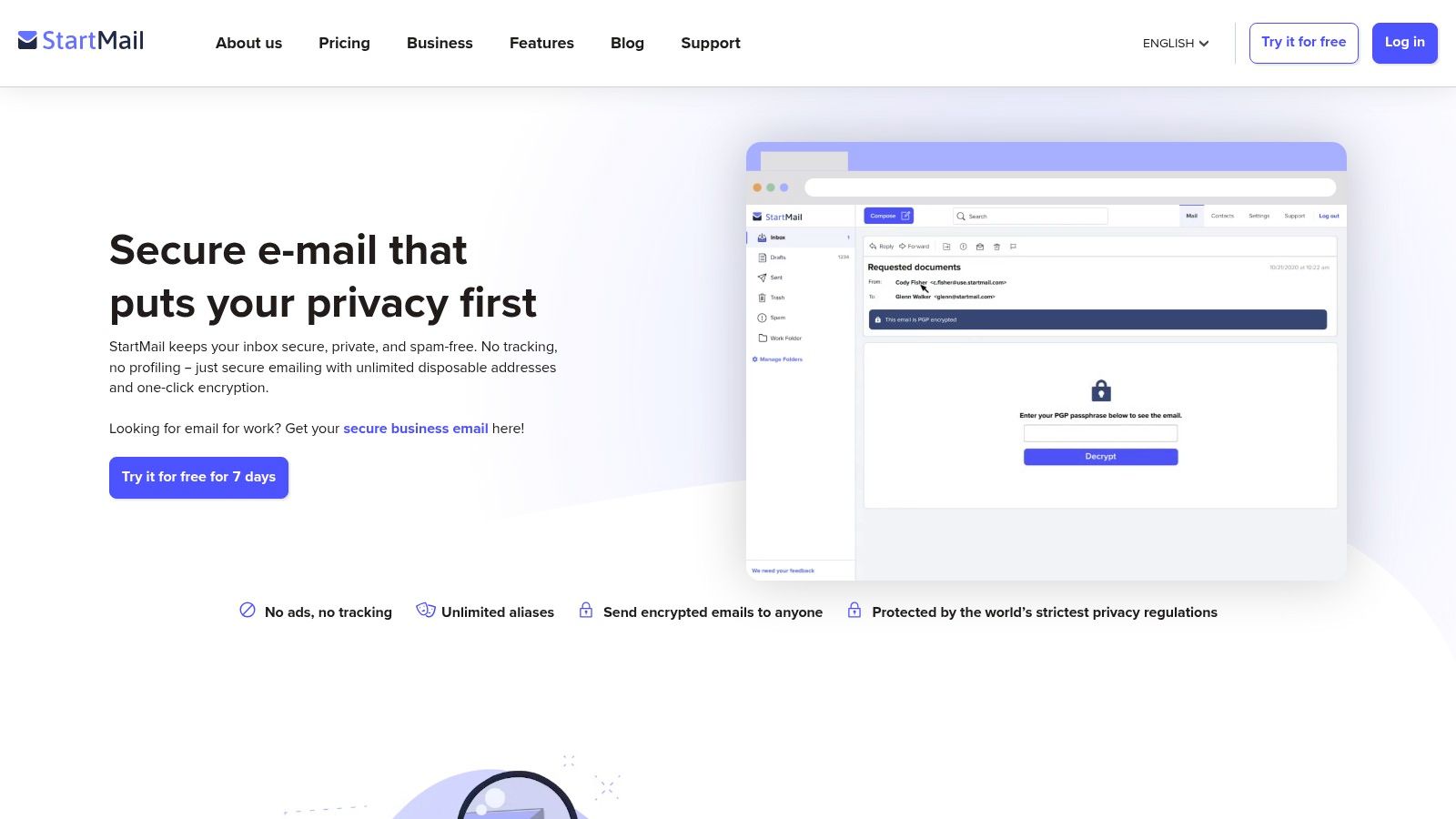
While StartMail does not offer a permanent free plan, it provides a 7-day free trial to test all its features. Its standout capability is the creation of unlimited, disposable email aliases, which helps protect your primary address from spam and tracking. The platform also accepts Bitcoin for annual plans, adding another layer of privacy for payments. The user interface is straightforward and functional, making it easy for users to manage their privacy settings and aliases effectively.
Key Details
- Pricing: No free plan. Paid plans start at $5.00/month (billed annually). 7-day free trial available.
- Verification Method: Recovery email or a one-time recovery key.
- Unique Offering: Unlimited disposable email aliases and Bitcoin payment option for enhanced anonymity.
- Best For: Users who prioritize alias management and are willing to pay for a dedicated, ad-free privacy service.
Pros & Cons
| Pros | Cons |
|---|---|
| Strong focus on privacy with Dutch jurisdiction | No permanent free tier is available |
| Unlimited email aliases for all users | Fewer integrated tools (like calendar/drive) than some competitors |
| Accepts Bitcoin for enhanced payment privacy | User interface is functional but less modern than some rivals |
Website: https://www.startmail.com
5. Posteo
Posteo is a standout German-based service for those needing an email without phone number verification, combining robust privacy, sustainability, and affordability. Based in Germany, it benefits from strong data protection laws. Its signup process is designed for complete anonymity; it doesn’t ask for any personal information, including a phone number, and even allows for anonymous payment via bank transfer, PayPal, or sending cash by mail. This commitment to user privacy is a core part of its identity.
The platform is entirely ad-free and powered by green energy, appealing to users who value both privacy and environmental responsibility. For a very low monthly fee, users get a secure, encrypted email service with a clean, functional interface. While it lacks a free plan, its pricing is incredibly accessible. Posteo’s feature set is more minimalist compared to larger suites, focusing on providing an excellent core email experience with strong security like two-factor authentication and DANE/TLS encryption.
Key Details
- Pricing: Begins at a highly affordable €1/month.
- Verification Method: No personal data or verification is required.
- Unique Offering: Anonymous cash-by-mail payment option and a strong focus on sustainability.
- Best For: Users seeking maximum anonymity and a simple, secure, and eco-friendly email service.
Pros & Cons
| Pros | Cons |
|---|---|
| Very affordable pricing | No phone support available |
| Strong privacy ethos without phone requirement | More minimalist feature set than some competitors |
| Anonymous signup and payment options | No free plan is offered |
For a deeper dive into its privacy-first approach, you can explore Posteo and similar secure services.
Website: https://posteo.de
6. mailbox.org
mailbox.org is a German-based paid email provider that offers a strong alternative for users looking for an email without phone number verification. Operating under Germany’s strict data protection laws, it prioritizes security and user privacy. While it is a premium service, it offers a 30-day free trial that allows you to test its features. During signup, you can register completely anonymously without providing a real name or phone number, which is a key advantage for privacy-focused users.

The platform is designed for users who are willing to pay a small fee for enhanced security, an ad-free experience, and reliable service. It’s important to note that trial accounts have temporary sending and storage limitations to prevent abuse. These restrictions are lifted as soon as you add funds, transitioning you to a full-featured account. The service also includes a full office suite with a calendar, contacts, and cloud storage, making it a comprehensive solution for individuals and small businesses.
Key Details
- Pricing: Starts at €1/month. A 30-day free trial is available.
- Verification Method: No personal data required for the trial.
- Unique Offering: Full office suite integration (calendar, contacts, cloud storage) and a strong reputation for deliverability.
- Best For: Users who need a reliable, paid email service with integrated productivity tools under strict German privacy laws.
Pros & Cons
| Pros | Cons |
|---|---|
| Anonymous registration is possible | Trial accounts have restrictions until funded |
| Based in Germany with strong privacy laws | It is a paid service with no permanent free plan |
| Includes a full suite of office tools | Phone support is only an optional callback service |
Website: https://mailbox.org
7. Mailfence
Mailfence is a strong contender for those needing a secure email without phone number verification. Operating from Belgium, it benefits from strong privacy laws and offers an integrated suite that includes encrypted email, calendars, and documents. The service is committed to digital freedom and privacy, explicitly designing its signup process to avoid mandatory phone number collection. Instead, users can verify their account with an alternate email address, which also serves as a recovery method, ensuring both security and accessibility.
The platform is completely ad-free, ensuring your data is never scanned or sold for marketing purposes. Mailfence provides a free plan with 500 MB of storage, while its paid tiers offer more space, custom domains, and POP/IMAP support. Its transparent approach is a key selling point; the company even publishes blog content detailing its commitment to phone-free registration. This makes it an excellent choice for users who value both privacy features and clear, user-centric policies.
Key Details
- Pricing: Starts with a free plan. Paid plans begin at €3.50/month.
- Verification Method: Alternate email address.
- Unique Offering: Integrated suite with email, calendar, and document storage under Belgian privacy law.
- Best For: Users and businesses looking for an ad-free, all-in-one productivity suite with transparent privacy practices.
Pros & Cons
| Pros | Cons |
|---|---|
| Strong Belgian privacy protection | Free plan has limited storage (500 MB) |
| No phone number required for signup | Paid plans can link your identity via payment details |
| Ad-free and no tracking across all plans | Full anonymity is harder to achieve on paid tiers |
Website: https://mailfence.com
8. Fastmail
Fastmail is a well-established, premium email service known for its speed, reliability, and strong feature set. While it is a paid-only service, it provides a solid option for those looking for an email without phone number verification. The standard signup process does not mandate a phone number; instead, you can secure your account with a recovery email. It’s important to note that during the 30-day free trial, Fastmail may request SMS verification as an anti-abuse measure, but this can be bypassed by subscribing and paying upfront.
Based in Australia, Fastmail offers a clean, ad-free experience with excellent spam filtering and intuitive mobile and web applications. It provides robust tools like custom domains, calendars, and contacts, making it a powerful alternative to mainstream providers for both individuals and businesses. The service prioritizes user control and privacy, ensuring your data is not scanned for advertising purposes. Customer support is responsive and helpful, typically handled through a ticket system.
Key Details
- Pricing: Paid plans start at $3/month. A 30-day free trial is available.
- Verification Method: Recovery email (SMS may be requested for free trials).
- Unique Offering: Mature, high-performance platform with excellent calendar and contact integration.
- Best For: Users and businesses seeking a reliable, fast, and ad-free paid email service.
Pros & Cons
| Pros | Cons |
|---|---|
| Mature, reliable service with good support | No permanent free tier |
| No default phone number collection on signup | Free trial may trigger SMS verification |
| Excellent spam filtering and fast apps | Based in a Five Eyes country (Australia) |
Website: https://www.fastmail.com
9. Runbox
Runbox is a solid Norwegian-based provider for users wanting a straightforward email without phone number verification. Operating under strong Norwegian privacy laws, it emphasizes security and sustainability, running on 100% renewable energy. The signup process is a key advantage; the phone number field is present but entirely optional, allowing you to create an account with just a username and password. While there isn’t a permanent free plan, Runbox offers a 30-day free trial that lets you test its full capabilities before committing.
The platform stands out for its affordability and flexibility, with paid plans starting at a very low entry point. This makes it accessible for users who need a private, ad-free experience without the higher cost of other premium services. The interface is functional and clean, though perhaps less modern than some competitors. Support is reliable, offered 24/7 through a ticket and email system, backed by comprehensive documentation for self-service.
Key Details
- Pricing: No free plan, but a 30-day trial is available. Paid plans start from $19.95/year.
- Verification Method: No verification is required to sign up.
- Unique Offering: Strong focus on sustainability and extremely affordable entry-level plans.
- Best For: Budget-conscious individuals and small businesses looking for a reliable, private email host based in a privacy-friendly country.
Pros & Cons
| Pros | Cons |
|---|---|
| Strong Norwegian privacy protections | No permanent free plan available |
| Optional phone number at signup | User interface is less refined than some rivals |
| Very affordable paid plans | Migration tools are not as advanced |
Website: https://runbox.com
10. Kolab Now
Kolab Now is another robust, Swiss-based provider offering a secure email without phone number verification. It positions itself as a complete groupware solution, integrating email with calendars, contacts, and file storage, all under the protection of Swiss privacy laws. The signup process is straightforward, requiring only an alternative email address for verification, successfully avoiding any need for a phone number. This makes it an excellent choice for users and teams looking for a comprehensive, privacy-focused alternative to mainstream suites.
The platform offers a 30-day free trial, allowing users to fully test its capabilities before committing. Unlike services with permanent free tiers, Kolab Now is a premium-only service, which reinforces its commitment to a business model based on user subscriptions rather than data monetization. Its interface is functional, though some users might find the extensive feature toggles slightly complex initially. Security is enhanced with support for TOTP two-factor authentication, providing an additional layer of protection for your account.
Key Details
- Pricing: Starts at CHF 5.00/month for an “Email only” plan.
- Verification Method: Recovery email.
- Unique Offering: A full open-source groupware suite (email, calendar, contacts, files) with strong privacy guarantees.
- Best For: Individuals and teams needing a complete, private collaboration suite without phone verification.
Pros & Cons
| Pros | Cons |
|---|---|
| Based in Switzerland with strong privacy laws | No permanent free plan available |
| No mandatory phone verification required | Feature settings can be complex for beginners |
| Offers a full suite of collaboration tools | Less modern UI compared to some competitors |
Website: https://kolabnow.com
11. SimpleLogin
SimpleLogin offers a unique approach to getting an email without phone number verification by focusing on aliasing. Instead of a standalone inbox, it creates disposable email aliases that forward messages to your primary email address. This allows you to sign up for services without ever revealing your real email, effectively shielding you from spam and data breaches. The signup process itself is privacy-first, requiring only a username and password, with no demand for a phone number.
Acquired by Proton, SimpleLogin integrates seamlessly into the Proton ecosystem while remaining a powerful standalone tool. The free plan is generous, offering 10 aliases, which is plenty for personal use. Premium plans unlock unlimited aliases, custom domains, and the ability to send and reply directly from your alias. This makes it an excellent tool for developers, privacy advocates, or anyone looking to compartmentalize their digital life and reduce their online footprint.
Key Details
- Pricing: Starts with a free plan. Premium plans begin at $4/month.
- Verification Method: No verification required beyond a username and password.
- Unique Offering: Advanced email aliasing to protect your primary inbox.
- Best For: Users who want to protect their existing email from spam and tracking without creating a new primary account.
Pros & Cons
| Pros | Cons |
|---|---|
| Protects your real email address | Not a standalone email provider; requires a primary inbox |
| Open-source with a self-hosting option | The free plan is limited to 10 aliases |
| Strong integration with the Proton ecosystem | Custom domains are a premium feature |
You can explore the benefits and uses by checking out this in-depth guide to email alias services.
Website: https://simplelogin.io
12. addy.io (formerly AnonAddy)
addy.io offers a unique approach to getting an email without phone number verification by focusing on email aliasing and forwarding. Instead of being a primary inbox provider, it generates unlimited anonymous email aliases that forward messages to your real email address. This protects your primary inbox from spam and data breaches, as you never have to expose it. The signup process is simple and respects user privacy, requiring only a username and password, with no demand for a phone number.
The platform is open-source, providing transparency and allowing users to self-host if they prefer maximum control. It operates on a freemium model, with a generous free tier offering substantial functionality for casual users. Paid plans are very affordable and unlock advanced features like custom domains, more recipients, and PGP encryption for enhanced security. Browser extensions and mobile apps make it seamless to generate new aliases on the fly whenever you need to sign up for a service.
Key Details
- Pricing: A generous free plan is available. Paid plans start at just $1/month.
- Verification Method: Requires only a destination email address to forward to.
- Unique Offering: Open-source, self-hostable email aliasing service with unlimited aliases.
- Best For: Users who want to protect their primary email address from spam and tracking without creating multiple inboxes.
Pros & Cons
| Pros | Cons |
|---|---|
| Protects your real email address | Security is dependent on your primary email provider |
| Transparent and open-source | Not a standalone email client; requires an existing inbox |
| Generous free tier and low-cost paid plans | Some advanced features require a paid subscription |
Website: https://addy.io
13. Temp-Mail
Temp-Mail is the go-to solution for creating a disposable email without phone number verification. It provides instant, temporary inboxes that self-destruct after a set time, making it perfect for one-time signups, forum registrations, or avoiding marketing spam from untrusted websites. The service is entirely browser-based and requires no personal information, offering a new email address the moment you visit the site. This focus on speed and anonymity makes it a powerful tool for quick verification needs.
The platform is designed for immediate use, generating a random email address automatically upon arrival. While the core service is free and ad-supported, premium plans offer enhanced features like custom email names, extended storage time for messages, multiple simultaneous mailboxes, and an ad-free interface. This makes it a versatile option, scaling from a quick, disposable tool to a more robust temporary inbox manager for frequent users.
Key Details
- Pricing: Core service is free. Premium plans are available for more features.
- Verification Method: None required; email is generated instantly.
- Unique Offering: Instant, no-signup-required disposable email addresses.
- Best For: Quick, one-off website signups and protecting your primary inbox from spam.
Pros & Cons
| Pros | Cons |
|---|---|
| Fastest way to get an email address | Frequently blocked by major online services |
| No personal information required | Messages are temporary and not secure |
| Completely free for basic use | Unsuitable for important or personal accounts |
For more tips on managing unwanted messages, you can learn how to effectively block spam emails.
Website: https://temp-mail.org
13-Platform Email Verification Feature Comparison
| Provider | Core Features / Security ✨ | User Experience ★★★★☆ | Value Proposition 💰 | Target Audience 👥 | Unique Selling Points 🏆 | Price Points 💰 |
|---|---|---|---|---|---|---|
| Proton Mail | End-to-end encryption, no phone verification required | Intuitive UI, import tools, alias support | Strong privacy, free & paid plans | Privacy-focused individuals & businesses | Large privacy suite (VPN, Calendar, Drive) | Free; Paid from $5/month |
| Tuta | Anonymous signup, supports Tor & VPN, e2e encryption | Reliable over Tor/VPN, manual approval holds | Privacy-friendly payments, no phone needed | Privacy advocates, anonymity seekers | Accepts Bitcoin/Monero payments | Free & Paid plans available |
| StartMail | Unlimited aliases, no ads/tracking, Bitcoin payments | Simple pricing, easy alias management | Strong privacy, 7-day free trial | Privacy-minded personal/business users | Alias management, Bitcoin payment option | Paid only; from ~$5/month |
| Posteo | Anonymous signup, green-powered, strong security | Minimalist UI, ad-free experience | Very affordable, eco-friendly | Eco-conscious privacy users | Cash by mail payments, sustainability focus | €1/month |
| mailbox.org | Anonymous registration, optional callback support | Reliable deliverability, 30-day trial | Good reliability, privacy-forward | Privacy-focused professionals | Optional phone callback support | Paid only; from €1/month |
| Mailfence | No phone, alias support, 2FA, ad-free | Clear phone-free signup guidance | Secure suite, recovery email required | Security-conscious users with alternate email | Belgian jurisdiction, blog education | Free & Paid from €2.50/month |
| Fastmail | Strong spam filtering, 2FA, no default phone | Excellent apps, 30-day trial | Reliable service, no default phone collection | Mature users and businesses | Strong apps, solid support | Paid only; from $3/month |
| Runbox | Optional phone, budget plans, 24/7 support | Less refined UI, solid documentation | Affordable pricing tiers | Budget-conscious, privacy-minded users | Low-cost plans, no mandatory phone | ~$1.40/month |
| Kolab Now | Email verification only, full collaboration suite | Transparent updates, 30-day trial | Swiss jurisdiction, strong privacy | Teams needing groupware and privacy | Collaboration tools, TOTP 2FA | Paid only; from €5/month |
| SimpleLogin | Email aliasing, 2FA/WebAuthn, free & premium | User-friendly alias management | Reduces spam, open-source with self-hosting | Users needing spam reduction & privacy | Integration with Proton Mail, open-source | Free; Premium from $5/month |
| addy.io | Email aliasing, PGP, custom domains, open-source | Transparent development, apps/extensions | Strong privacy, self-hosting option | Privacy-focused, open-source enthusiasts | Open-source, strong privacy focus | Free; Paid plans from $2/month |
| Temp-Mail | Disposable inbox, no signup, premium multiple inboxes | Instant email, mobile apps | Fast, no personal info needed | One-time verifications, quick email needs | No phone required, instant disposable emails | Free; Premium from $5/month |
Choosing Your Path to a Phone-Free Inbox
Navigating the world of digital communication without surrendering your phone number is not only possible, it’s a critical step toward reclaiming your online privacy. As we’ve explored, the landscape of providers offering email without phone number verification is diverse, catering to a wide range of needs from uncompromising end-to-end encryption to practical, feature-rich inboxes for business use. The journey to a more private digital life begins with understanding that you have a choice.
The key takeaway from this extensive list is that no single provider is universally perfect. Your ideal service depends entirely on your specific threat model, technical comfort level, and daily communication requirements. The decision is a trade-off between absolute anonymity, usability, and features.
Synthesizing Your Options
To make a well-informed decision, reflect on the core priorities that drove you to seek a phone-free email solution. Let’s distill the primary use cases we’ve seen:
- For Maximum Security and Anonymity: If your primary goal is to protect sensitive communications from surveillance, providers like Proton Mail and Tuta are your strongest contenders. Their foundation in zero-access, end-to-end encryption ensures that no one, not even the company, can read your messages.
- For the Privacy-Conscious Professional: Users who need a balance of strong privacy, professional features like custom domains, and robust calendar and contact integration will find excellent options in StartMail, mailbox.org, and Mailfence. These services prioritize user privacy while delivering a polished, business-ready experience.
- For Data Sovereignty and Simplicity: If you prioritize knowing exactly where your data is stored and want straightforward email without complexity, Typewire offers Canadian-hosted email with zero-access encryption and privately-owned infrastructure. It’s ideal for users and businesses who value data residency under strong privacy laws without needing a full productivity suite.
- For Strategic Anonymity and Spam Control: If your goal is less about encrypting every message and more about compartmentalizing your digital identity, alias services are invaluable. Tools like SimpleLogin and addy.io empower you to create unique, disposable email addresses for every online service, effectively shielding your primary inbox and identity from data breaches and spam.
Your Next Steps to Implementation
Choosing a provider is the first step; implementing it effectively is the next. Before you commit, take advantage of free trials or basic-tier accounts to test the user interface and workflow. Does the mobile app meet your needs? How intuitive is the process of setting up filters or aliases?
Consider a gradual transition. Start by using your new, private email for new online sign-ups. Over time, you can migrate more sensitive or important accounts away from your old, data-hungry provider. This measured approach ensures a smooth and manageable shift toward a more secure communication habit.
Ultimately, opting for an email without phone number verification is a deliberate act of digital self-defense. It’s about drawing a line and deciding who gets access to your personal information. By selecting a service that aligns with your values and security needs, you are not just getting a new inbox; you are building a more resilient and private foundation for your entire digital life.
Is your business struggling to manage its email infrastructure or seeking a more secure, custom-branded communication platform? For a comprehensive solution that goes beyond a single inbox, consider Typewire. We specialize in building and managing secure, scalable email hosting solutions tailored to your organization’s specific needs, ensuring privacy and reliability are at the core of your operations. Learn more at Typewire.