Standard email services from major tech companies often come with a hidden cost: your privacy. These free platforms frequently scan your messages to build advertising profiles, share data with third parties, and leave your sensitive communications exposed to data breaches and surveillance. For anyone seeking to protect their personal or professional correspondence, switching to a dedicated secure email provider is no longer a niche concern; it's an essential step in safeguarding digital identity.
This guide provides a detailed, side-by-side comparison of the leading contenders for the title of best secure mail service. We move past the marketing claims to give you a clear, actionable breakdown of what truly matters. You'll get an in-depth look at providers like Typewire, Proton Mail, and Tuta, comparing their core security features, privacy policies, pricing, and usability. Understanding core concepts like end-to-end encryption is vital, and we'll show you exactly how each service implements it.
Instead of generic advice, you'll find practical insights, direct links, and screenshots to help you choose the right platform for your specific needs, whether you're an individual reclaiming your privacy or a business securing its communications. Let's find the service that puts you back in control of your inbox.
1. Typewire
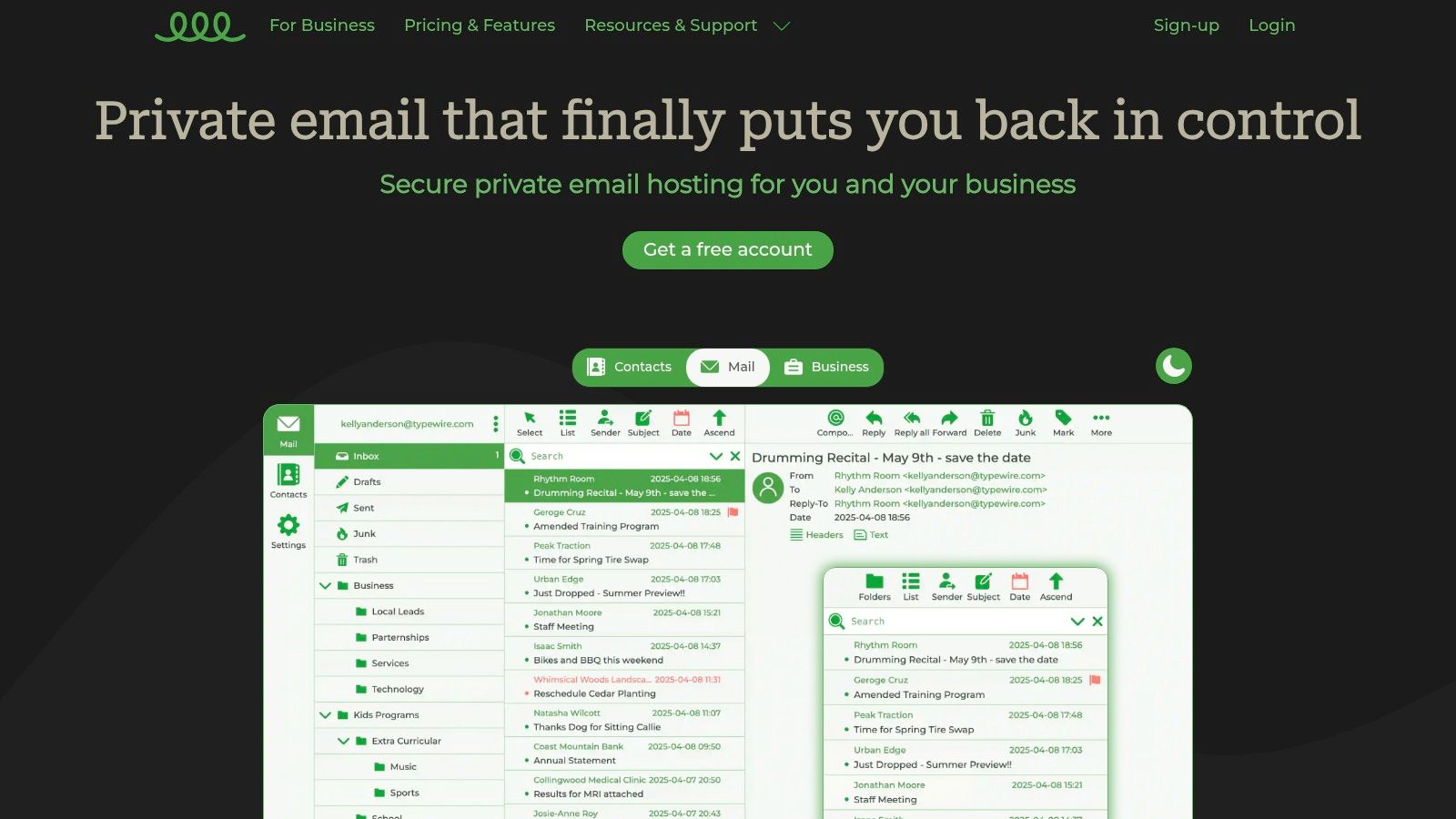
Typewire positions itself as a premier choice for the best secure mail service, particularly for users who demand absolute data sovereignty. It’s an engineered solution for individuals and businesses aiming to reclaim their digital privacy from the ground up, built on a foundation of zero ads, zero tracking, and a strict no-data-mining policy. This service is ideal for those who see their email as a private communication channel, not a product to be monetized.
The platform’s core strength lies in its infrastructure. By operating exclusively on privately owned Canadian data centers, Typewire sidesteps the privacy ambiguities associated with major third-party cloud providers like AWS or Google Cloud. This commitment ensures that your data is governed by Canadian privacy laws and remains shielded from the extensive data-gathering ecosystems common among mainstream email services. This makes it a compelling option for professionals and businesses handling sensitive information.
Key Features and User Experience
Typewire’s feature set is both practical and powerful. The modern web interface is fast and responsive, offering both light and dark modes to suit user preference. Migrating from services like Gmail or Outlook is designed to be a straightforward process, minimizing downtime for businesses.
- Custom Domain Hosting: A crucial feature for businesses, allowing you to use your own domain (e.g.,
you@yourbusiness.com) to maintain a professional brand identity. - Intuitive User Management: Team administrators can easily add, remove, and manage user accounts, making it scalable for small to medium-sized businesses.
- Advanced Threat Protection: The service employs sophisticated, adaptive anti-spam and virus filtering to keep your inbox clean and secure from evolving threats.
Practical Use and Implementation
For a small business, setting up Typewire involves registering a domain (or using an existing one) and creating user accounts through the simple admin panel. The process is designed to be accessible even for non-technical users. For instance, a small marketing agency can create individual mailboxes for its team, set up aliases for roles like contact@ or support@, and manage everything from a single, secure dashboard.
The emphasis on a clean, ad-free environment directly translates to enhanced productivity. Without distracting ads or "promotional" emails cluttering the interface, users can focus entirely on their communications.
Pricing and Plans
Typewire offers a tiered pricing structure that includes a free plan for basic personal use. Paid plans unlock more storage, custom domain support, and advanced features for teams. While specific pricing details require a visit to their website, the model is flexible enough to accommodate everyone from individual privacy advocates to growing businesses. A 7-day risk-free trial is available, allowing you to fully test the service before committing.
| Feature Highlights | Typewire |
|---|---|
| Data Hosting | Private, Canadian data centers |
| Privacy Model | Zero ads, no tracking, no data mining |
| Custom Domains | Yes, on paid plans |
| User Management | Yes, for teams |
| Spam/Virus Filtering | Advanced and adaptive |
| Free Trial | 7 days |
Pros:
- Complete data ownership and privacy with a zero-ads policy.
- Operates on privately owned Canadian infrastructure, ensuring data sovereignty.
- Flexible plans with custom domain support and easy team management.
- Fast, modern web interface with a smooth migration process.
Cons:
- Pricing tiers are not fully detailed upfront and require a site visit.
- Lacks native integrations with third-party cloud storage and collaboration tools.
Website: https://typewire.com
2. Proton Mail
Proton Mail is a titan in the secure email space, renowned for its unwavering commitment to privacy and robust security architecture. Based in Switzerland, it operates under some of the world's strictest privacy laws, ensuring your data is legally protected from foreign surveillance. The service is built on a zero-access encryption model, meaning not even Proton can read your emails or access your files.
This makes it an exceptional choice for individuals and businesses who demand the highest level of confidentiality. Proton's ecosystem extends beyond email, offering an integrated suite of privacy-focused products, including a calendar, cloud drive, and VPN service.
Key Features and User Experience
Proton Mail provides a clean, modern interface that is intuitive for users migrating from services like Gmail. One of its standout features is the Easy Switch tool, which simplifies the process of importing emails, contacts, and calendars from other providers. This seamless migration support lowers the barrier to entry for those looking to enhance their digital privacy.
For power users, Proton Mail offers advanced capabilities such as custom domains, aliases, and powerful Sieve filters for organizing your inbox. Users who prefer desktop clients can connect their accounts using the Proton Mail Bridge, an application that enables IMAP/SMTP support for apps like Thunderbird and Outlook while maintaining end-to-end encryption.
Here is a quick overview of what Proton Mail offers:
| Feature | Details |
|---|---|
| Encryption | End-to-end (E2EE) and zero-access encryption by default. |
| Jurisdiction | Switzerland (strong privacy laws). |
| Custom Domains | Supported on all paid plans. |
| Desktop Client Support | Via Proton Mail Bridge (paid feature). |
| Ecosystem | Includes Calendar, Drive, and VPN in bundled plans. |
| Open Source | Core applications are open-source and independently audited. |
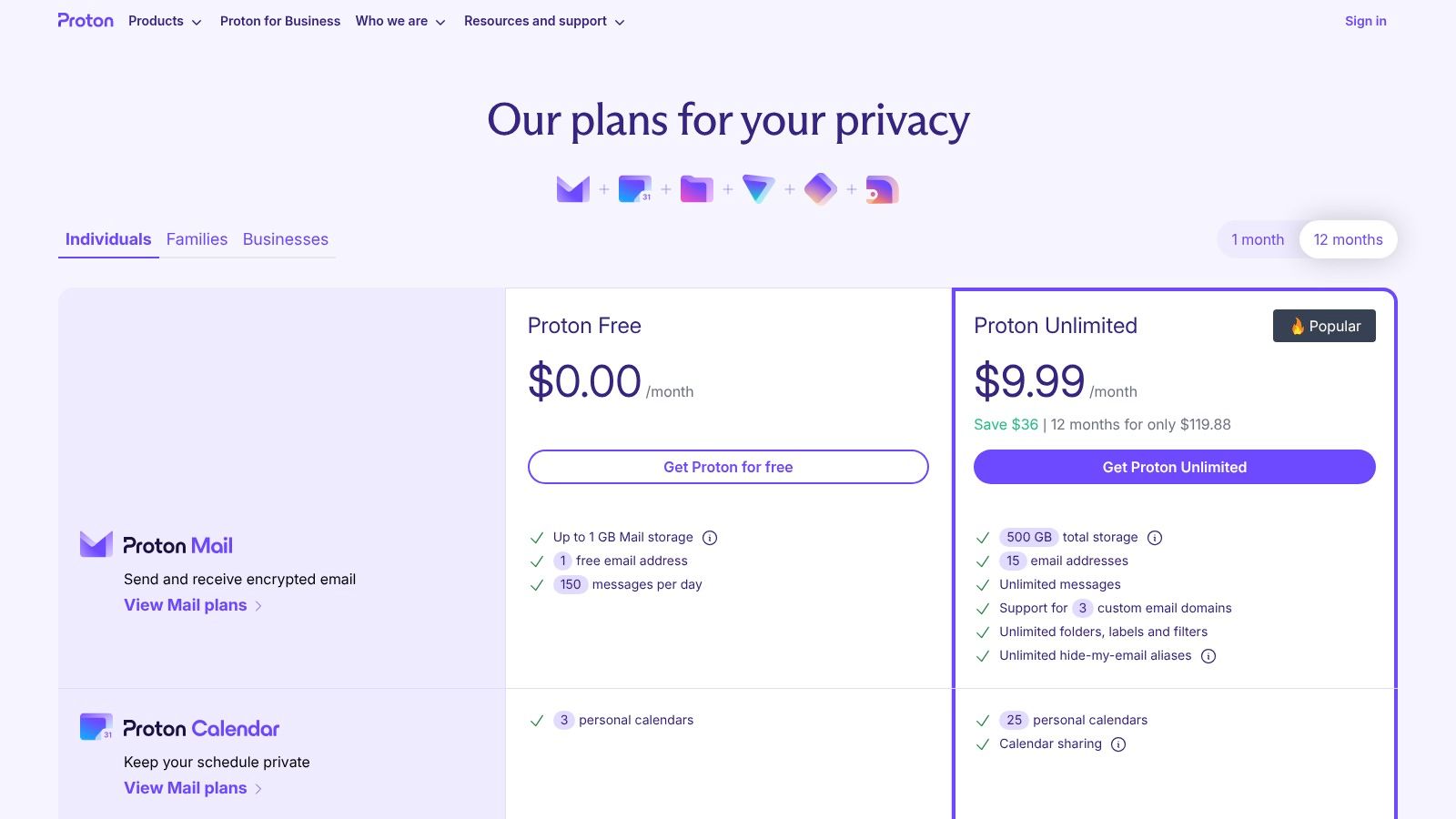
Pricing and Plans
Proton offers a functional free plan, which is great for testing the service, but it comes with limitations on storage (1 GB) and features. To unlock its full potential, a paid plan is necessary.
- Proton Free: Limited storage and features.
- Mail Plus: Starts at €3.99/month, offering more storage, custom domains, and the convenient
@pm.meshort domain address. - Proton Unlimited: Starts at €9.99/month, providing access to the entire Proton ecosystem (Mail, Calendar, Drive, VPN) with maximum storage.
While the free plan is a solid entry point, the paid tiers are where Proton Mail truly shines as a candidate for the best secure mail service, offering comprehensive tools for both personal and business use. You can explore their other plans and features directly on their website.
Website: https://proton.me/pricing
3. Tuta (formerly Tutanota)
Tuta, formerly known as Tutanota, is a formidable contender for the best secure mail service, operating out of Germany with a laser focus on encrypting everything by default. Its core principle is to protect your entire mailbox, not just the body of your emails. This includes subject lines, contacts, and even your calendar, all secured with end-to-end encryption.
Based in Germany, Tuta leverages the country's strong data protection laws (GDPR) to safeguard user privacy. The service's commitment to a strict, no-compromise encryption model means it has built its platform from the ground up, ensuring no third-party services like Google Push are used, thereby minimizing data exposure.
Key Features and User Experience
Tuta offers a clean, minimalist interface across its web, desktop, and mobile applications, providing a consistent user experience on any device. A key differentiator is its encrypted full-text search, which allows users to search their encrypted mailbox locally on their device without compromising privacy. This is a significant technical achievement that many competitors struggle with.
Another powerful feature is the ability to send password-protected emails to non-Tuta users, ensuring end-to-end encryption even when communicating externally. For those researching top private email providers for security, Tuta's comprehensive approach makes it a standout choice. The platform also supports two-factor authentication (2FA), including U2F hardware keys, for maximum account security.
Here is a quick overview of what Tuta offers:
| Feature | Details |
|---|---|
| Encryption | E2EE for emails (including subject lines), calendars, and contacts. |
| Jurisdiction | Germany (strong GDPR and privacy laws). |
| Custom Domains | Supported on all paid plans. |
| Desktop Client Support | Dedicated desktop clients for Windows, macOS, and Linux. |
| Unique Features | Encrypted full-text search, password-protected external emails. |
| Open Source | All client applications are open-source and available on GitHub. |
Pricing and Plans
Tuta's pricing is straightforward and highly competitive, making robust security accessible to a wide audience. The free plan is quite generous, offering a solid starting point for individual users.
- Free: Provides 1 GB of storage for personal use.
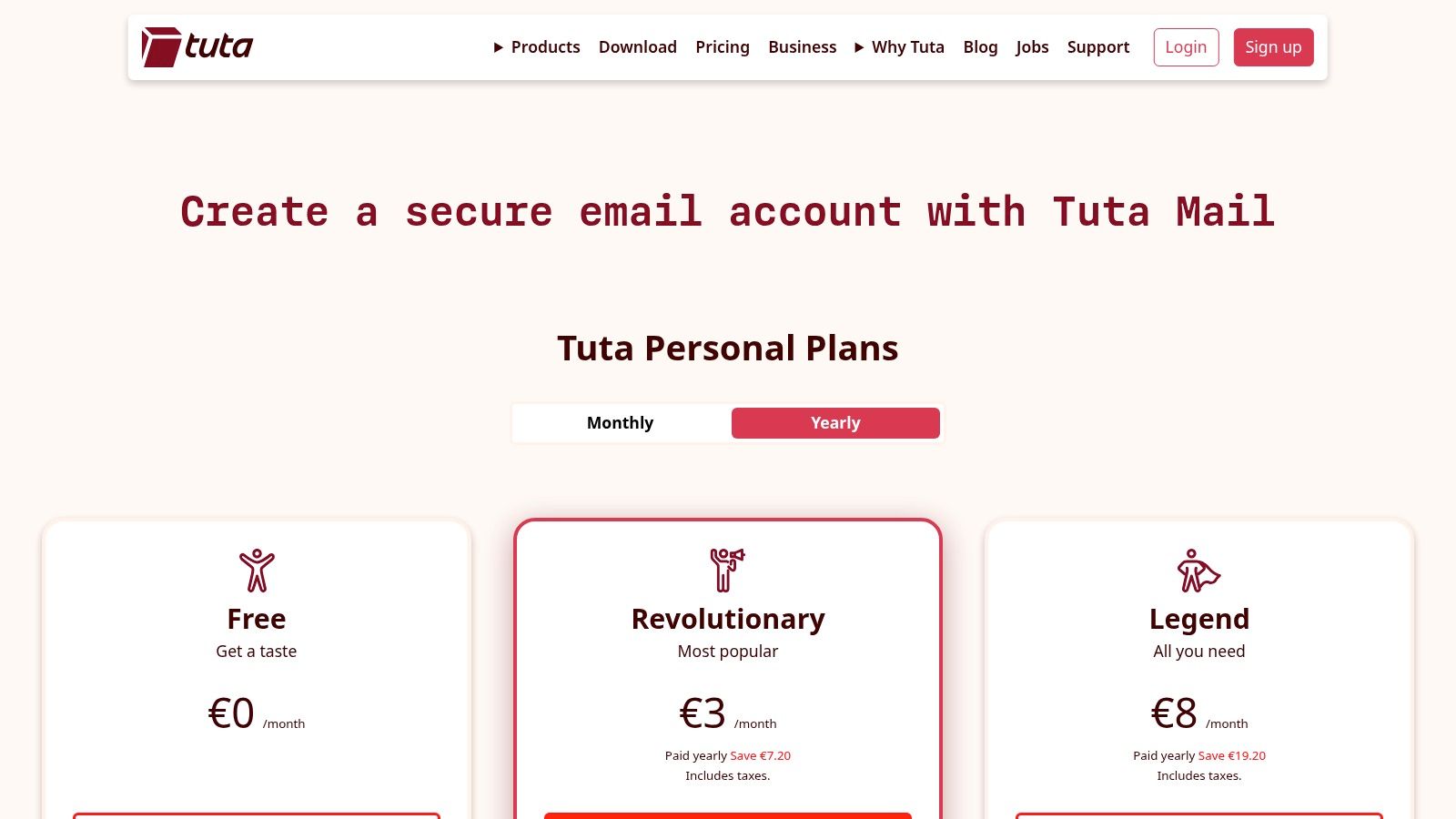
- Revolutionary: Starts at €3.00/month, offering 20 GB storage, multiple aliases, and custom domain support.
- Legend: Starts at €8.00/month, with 500 GB storage, more aliases, and additional premium features.
While the free plan is excellent for basic needs, the paid plans unlock the full suite of features necessary for professional or heavy personal use. Tuta's transparent pricing and uncompromising security model make it an excellent choice for anyone serious about digital privacy.
Website: https://tuta.com/pricing
4. StartMail
StartMail offers a streamlined and powerful approach to private email, focusing on user-friendly PGP encryption and robust alias management. Based in the Netherlands, it operates under strong GDPR and European privacy laws. The service is designed for users who want strong privacy controls without a steep learning curve, making it an excellent choice for those new to encrypted communication.
Its core philosophy is to make high-level security accessible. StartMail achieves this by integrating PGP encryption directly into its webmail interface, allowing users to send end-to-end encrypted messages with a single click. This ease of use, combined with powerful anti-tracking features, makes it a compelling contender for the best secure mail service.
Key Features and User Experience
StartMail's interface is clean and traditional, ensuring an easy transition for users coming from mainstream email providers. Its most distinctive feature is its unlimited email alias system, which includes disposable "burner" addresses. This allows you to create unique aliases for every service you sign up for, protecting your primary email from spam and data breaches.
The platform also allows users to send password-protected emails to recipients who don't use PGP, ensuring the message content remains secure in transit and at rest. Furthermore, StartMail is fully compatible with any IMAP/SMTP client like Outlook or Thunderbird, allowing you to manage your secure email within your favorite desktop application.
Here is a quick overview of what StartMail offers:
| Feature | Details |
|---|---|
| Encryption | One-click PGP end-to-end encryption and password-protected messages. |
| Jurisdiction | Netherlands (GDPR compliant). |
| Custom Domains | Supported on all plans. |
| Desktop Client Support | Full IMAP/SMTP support for third-party clients. |
| Aliases | Unlimited custom and burner aliases to protect your main address. |
| Privacy Protections | Blocks tracking pixels and anonymizes IP addresses in email headers. |
Pricing and Plans
StartMail simplifies its offering by forgoing a permanent free plan in favor of a full-featured 7-day free trial. This approach lets potential customers test all premium features before committing.
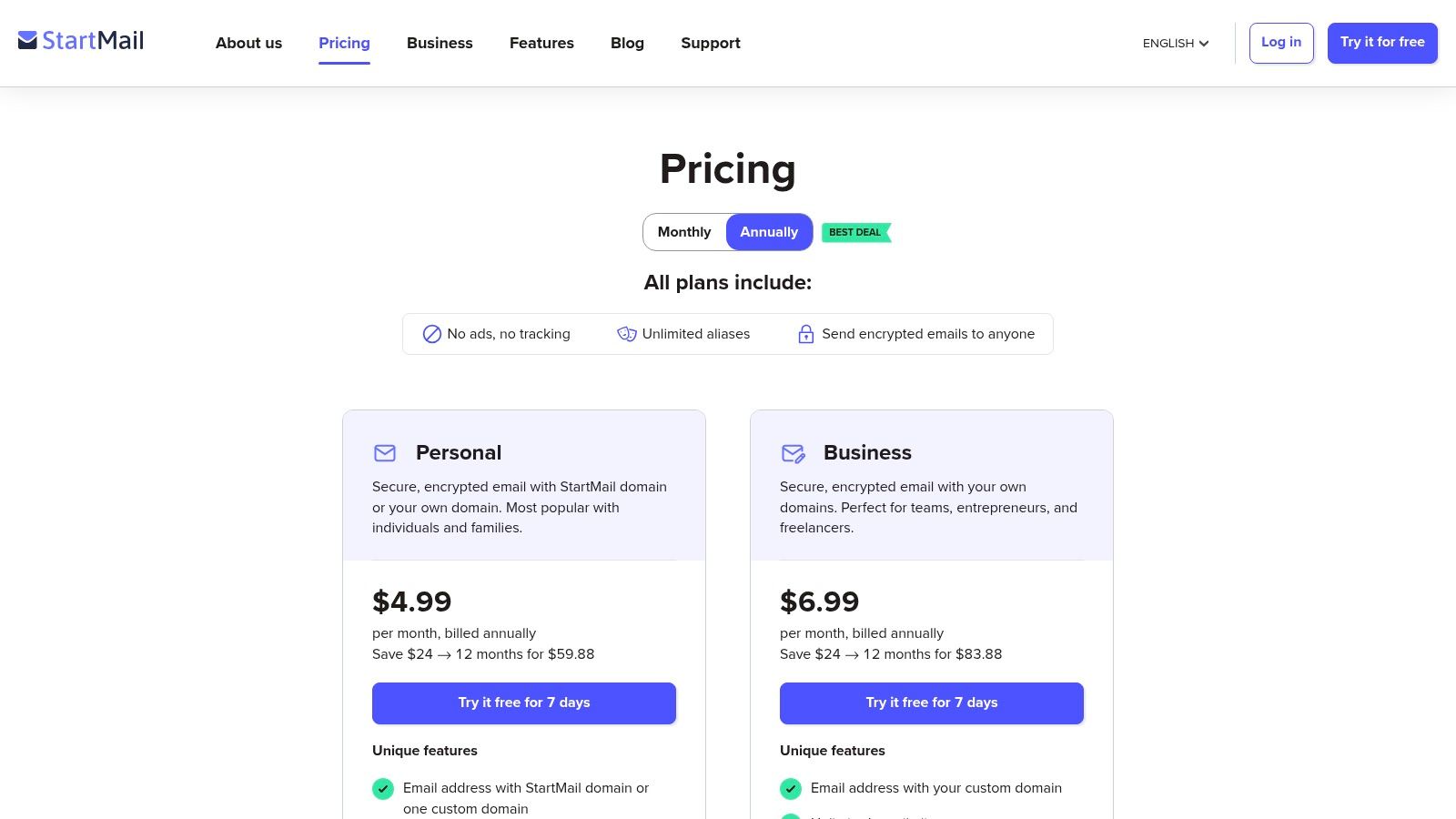
- Personal Plan: Starts at $5.00/month (billed annually), providing 10GB of storage and support for one custom domain.
- Custom Domain Plan: Starts at $5.85/month (billed annually), offering expanded features for business use, including user management for your domain.
The straightforward pricing and the ability to pay with Bitcoin for annual plans underscore its commitment to privacy. While it lacks a free tier, the trial provides ample opportunity to see if StartMail’s balance of simplicity and power is the right fit for your security needs.
Website: https://www.startmail.com/pricing
5. Mailfence
Mailfence is a Belgium-based secure email provider that prioritizes interoperability and user control. Operating under strong Belgian privacy laws, it offers a full suite of privacy-focused tools, including encrypted email, calendars, contacts, and document storage. Its main strength lies in its standards-based approach, making it one of the best secure mail service options for users who want to integrate with existing desktop clients like Outlook or Thunderbird without compromising on security.
The service is built around OpenPGP encryption, providing users with complete control over their key management. This makes it an ideal choice for privacy-conscious individuals and businesses who value flexibility and compatibility with established email protocols. Additionally, Mailfence donates 15% of its Ultra plan revenue to organizations that fight for digital rights, such as the Electronic Frontier Foundation (EFF).
Key Features and User Experience
Mailfence offers a comprehensive feature set that balances security with usability. Unlike services that require a dedicated bridge application, Mailfence provides direct support for IMAP, SMTP, POP, and Exchange ActiveSync. This native compatibility allows for a seamless setup with virtually any standard email client or mobile device, a significant advantage for users who prefer their own applications.
The platform provides an integrated key store, simplifying the process of creating, importing, and managing OpenPGP keys. It also supports custom domains with full DKIM, SPF, and DMARC records to prevent spoofing and improve deliverability. While its user interface may feel less modern than some rivals, it is clean, functional, and provides easy access to its powerful suite of tools.
Here is a quick overview of what Mailfence offers:
| Feature | Details |
|---|---|
| Encryption | End-to-end encryption using OpenPGP with integrated key management. |
| Jurisdiction | Belgium (strong privacy laws). |
| Custom Domains | Supported on all paid plans. |
| Desktop Client Support | Native IMAP, POP, SMTP, and Exchange ActiveSync support. |
| Ecosystem | Includes Calendar, Documents, and Groups. |
| Payment Options | Accepts credit cards, PayPal, and cryptocurrencies for enhanced privacy. |
Pricing and Plans
Mailfence provides a functional free plan with limited storage, which is a great way to explore its core features. For professional use, its paid plans offer excellent value and a broader set of capabilities.
- Free: 500 MB of email storage and 500 MB for documents.
- Entry: Starts at €3.50/month, providing 10 GB of email storage and custom domain support.
- Pro: Starts at €9.50/month, with 50 GB of email storage and priority support.
- Ultra: Starts at €29.00/month, offering 100 GB of email storage and extensive customization options.
The platform encourages long-term commitment by offering significant discounts on multi-year subscriptions. Its flexible payment options, including Bitcoin and Litecoin, cater to users who prioritize anonymity in all aspects of their digital life.
Website: https://mailfence.com
6. Hushmail
Hushmail carves out a specific and crucial niche within the secure email landscape, focusing primarily on the healthcare and business sectors. Based in Canada, it provides specialized, HIPAA-compliant communication tools that go beyond standard email. This includes encrypted email, secure web forms with e-signature capabilities, and the essential Business Associate Agreements (BAAs) required for healthcare providers in the United States.
This strong focus on regulatory compliance makes it a go-to choice for professionals in law, therapy, and healthcare who handle sensitive client information and require verifiable security. Hushmail is designed to simplify compliance without sacrificing usability, offering a straightforward platform for secure digital communication.
Key Features and User Experience
Hushmail’s platform is built for professional use cases, particularly where sensitive data collection is involved. Its standout feature is the integration of secure web forms, allowing users to create and embed custom forms on their websites to securely receive information from clients. These forms can include e-signatures, making them ideal for client intake, consent forms, and other official documentation.
The service provides a clean webmail interface and supports IMAP/POP for use with third-party email clients like Outlook or Apple Mail. While its personal privacy features aren't as stringent as zero-knowledge providers, its implementation of various secure email protocols is tailored for business compliance and ease of use, ensuring messages to non-Hushmail users can also be encrypted.
Here is a quick overview of what Hushmail offers:
| Feature | Details |
|---|---|
| Encryption | OpenPGP encryption. Encrypted if both parties use Hushmail or via a secure portal. |
| Jurisdiction | Canada (subject to local laws). |
| Compliance | HIPAA-compliant plans with Business Associate Agreements (BAAs) available. |
| Secure Forms | Create secure, e-signable web forms to collect sensitive client data. |
| Email Archiving | Included in specific business plans for record-keeping. |
| Free Trial | A 14-day free trial is available for healthcare plans. |
Pricing and Plans
Hushmail’s pricing structure is aimed at professionals and businesses, with plans tailored to specific industries. There is no free plan, but a trial is offered for its specialized healthcare services.
- Hushmail for Healthcare: Starts at $11.99/month, includes a BAA, and secure forms.
- Hushmail for Small Business: Starts at $7.99/month, offering custom domains and secure forms.
- Hushmail for Law: Starts at $11.99/month, designed for legal professionals.
- Hushmail Personal: A basic plan is available for personal use at $49.98/year.
For businesses needing the best secure mail service with a clear path to HIPAA compliance, Hushmail is an exceptional and highly specialized solution.
Website: https://www.hushmail.com/plans/
7. PreVeil
PreVeil offers a unique approach to secure email, designed specifically for organizations that need to add a layer of end-to-end encryption and compliance to their existing email infrastructure. Instead of replacing services like Microsoft 365 or Gmail, PreVeil integrates with them, creating a secure enclave for sensitive data. This makes it an ideal solution for businesses handling regulated information, such as defense contractors (CMMC, ITAR) and healthcare providers (HIPAA).
The service is built on a zero-trust security model, ensuring that not even PreVeil can access user data. This architecture is particularly effective for organizations that need the best secure mail service for compliance without overhauling their entire IT workflow. It seamlessly adds military-grade encryption directly into familiar tools like Outlook and the Gmail web interface.
Key Features and User Experience
PreVeil's greatest strength is its non-disruptive integration. Users can continue working within Outlook or Gmail, sending and receiving encrypted messages and files with a simple click. The platform automatically handles key management and encryption in the background, making it accessible even for non-technical team members. The user experience is designed to be as frictionless as possible to encourage adoption.
For administrators, PreVeil provides a powerful admin console for managing users, enforcing security policies, and accessing detailed audit logs for compliance purposes. Its ransomware-resilient restore capability is a standout feature, allowing organizations to securely recover their encrypted data even if their primary systems are compromised.
Here is a quick overview of what PreVeil offers:
| Feature | Details |
|---|---|
| Encryption | End-to-end (E2EE) and zero-trust security design. |
| Jurisdiction | United States (focused on US federal compliance like CMMC and ITAR). |
| Integration | Works on top of Microsoft 365, Outlook, and Gmail. |
| Compliance Support | HIPAA, CMMC 2.0, NIST 800-171, ITAR, FERPA, GLBA. |
| Admin Controls | Comprehensive admin console with user management and audit logs. |
| File Sharing | Secure, end-to-end encrypted file sharing is integrated. |
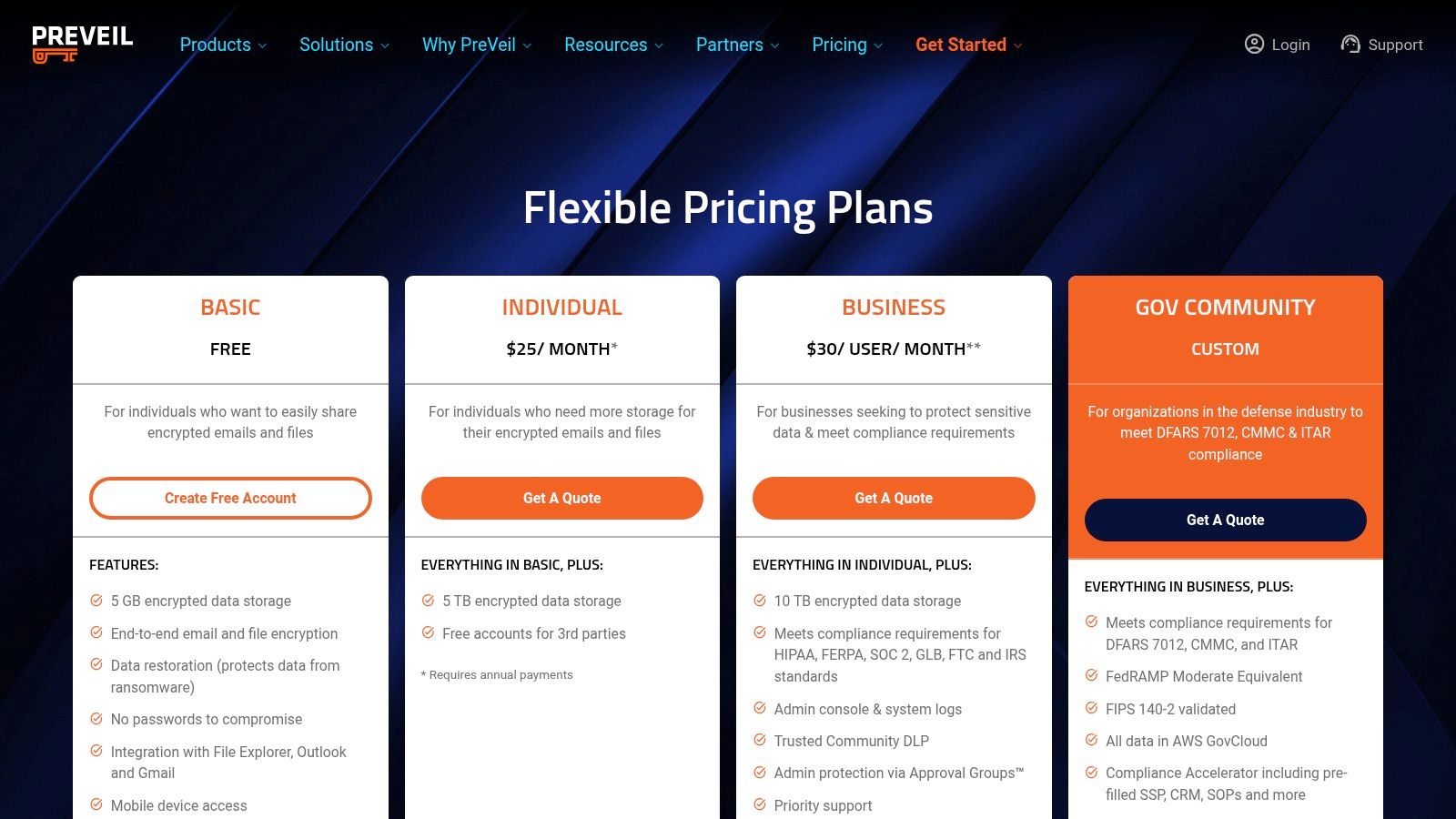
Pricing and Plans
PreVeil's pricing is structured for business and enterprise use, with plans that reflect its compliance-focused features. It offers a free plan for basic individual use, but its core value lies in the paid tiers.
- PreVeil Free: For personal, non-commercial use.
- PreVeil GovCommunity: A free plan for individuals working in the US Defense Industrial Base to collaborate securely.
- PreVeil Business: Starts at $30/user/month (billed annually, 5 user minimum), includes compliance features, admin console, and full integration.
- PreVeil Enterprise: Custom pricing for larger organizations needing advanced features and dedicated support.
While not aimed at the average consumer, PreVeil is a powerful and cost-effective solution for businesses that require verified, high-level security and compliance within their existing email environment.
Website: https://www.preveil.com/new-pricing-page
Secure Mail Services: Feature Comparison of Top 7
| Service | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Typewire | Moderate: Private data centers, no cloud integration | Moderate: Custom domain, team tools | High privacy, ad-free, secure messaging | Privacy-conscious users, SMBs, IT pros | Full data ownership, advanced spam/virus filters |
| Proton Mail | Moderate: Requires Proton Bridge for full desktop use | Moderate to high: Paid plans for storage/domains | Strong E2E encryption, integrated services | Consumers and businesses valuing privacy | Swiss jurisdiction, open-source, bundled ecosystem |
| Tuta | Moderate to high: No IMAP/POP support for strict E2E | Moderate: Limited import, multi-platform apps | Very strong encryption including metadata | Privacy-focused individual/family/business | End-to-end encryption including subjects & contacts |
| StartMail | Low to moderate: IMAP support, no POP3 | Low to moderate: Paid plans only | Easy PGP email encryption, alias support | Users needing aliasing and easy client integration | Unlimited burner aliases, anti-tracking features |
| Mailfence | Moderate: Supports multiple protocols, built-in keys | Moderate: Paid plans, flexible payments | Encrypted email with interoperability | Privacy users needing standard mail clients | OpenPGP with key management, protocol compatibility |
| Hushmail | Moderate: Compliance-focused, onboarding available | Moderate to high: Specialized plans | HIPAA-compliant, secure for healthcare/legal sectors | Healthcare, legal, SMBs requiring compliance | HIPAA compliance, BAA support, e-signatures |
| PreVeil | High: Integrates with existing providers plus admin tools | High: Enterprise-focused, minimum seats | Enterprise-grade encryption with compliance | Organizations needing E2E over Outlook/Gmail | E2E plus compliance, audit logs, ransomware resilience |
Making Your Final Choice: Actionable Steps to Secure Your Communications Today
Navigating the landscape of secure email can feel overwhelming, but as we've explored, the market is rich with powerful alternatives to surveillance-based free services. From Proton Mail's established reputation and comprehensive suite to Tuta's focus on full encryption and sustainability, each provider offers a unique approach to digital privacy. We've seen how services like Mailfence integrate a full office suite, while StartMail prioritizes PGP simplicity and alias creation for enhanced anonymity.
The central theme is clear: taking control of your digital correspondence is not only possible but also increasingly accessible. Whether you're a journalist protecting sources, a small business safeguarding client data, or simply an individual tired of being the product, a dedicated secure email provider is a fundamental step toward digital sovereignty. The providers we've reviewed, including Typewire, Proton Mail, Tuta, and others, prove that you don't have to sacrifice usability for security.
How to Choose the Best Secure Mail Service for You
Making the final decision requires moving from comparison to introspection. Your "best" service is the one that aligns perfectly with your specific threat model, workflow, and technical comfort level. Generic advice won't suffice; you need a personalized strategy.
To finalize your choice, follow these actionable steps:
-
Define Your Non-Negotiables: Start by listing your absolute must-haves. Is a custom domain for your business critical? Do you require HIPAA compliance for your medical practice, as offered by services like Hushmail? Perhaps you need the ability to host the service on your own private server for complete data control, a unique advantage of Typewire. Create a short list of 2-3 deal-breakers.
-
Evaluate Your Ecosystem: Consider how you'll interact with others. Do you primarily communicate with other security-conscious users, making end-to-end PGP encryption seamless? Or do you need a simple way to send encrypted messages to contacts still using Gmail or Outlook? Services that offer encrypted messages via a secure link and password can be invaluable here.
-
Test Drive Before You Commit: Words on a page can only tell you so much. Almost every service, from Proton Mail to Mailfence, offers a free, albeit limited, plan or a free trial. Sign up for your top two or three contenders. Send some test emails, explore the interface, and check out the mobile app. This hands-on experience is the single most effective way to determine which platform feels right for your daily use.
-
Plan Your Migration: Switching email providers is a significant step. Start by forwarding messages from your old account to your new secure one. Gradually update your contacts and online accounts with your new address. It’s a process that takes time, but the peace of mind that comes with knowing your communications are truly private is a worthwhile reward.
Ultimately, the journey to find the best secure mail service is an investment in your digital freedom. By taking these deliberate steps, you are not just choosing a tool; you are making a conscious decision to protect your right to private conversation in an increasingly intrusive world.
Ready to take the ultimate step in securing your digital communications with a self-hosted solution? Explore Typewire, the open-source platform designed for those who demand complete control and data sovereignty. Visit Typewire to learn how you can deploy a private, secure email server for your team or business today.