Why Your Small Business Is a Prime Target
Let's be honest, cybercriminals often see small businesses as low-hanging fruit. I've spent a lot of time chatting with cybersecurity pros and business owners who've unfortunately learned this the hard way. A recurring theme? It's not just about smaller IT budgets. It's a cocktail of factors that make small businesses particularly vulnerable. Think valuable data, employees who are generally more trusting of emails, and, sometimes, outdated security practices.
These weaknesses can be surprisingly subtle. For example, predictable email address patterns can make it easier for attackers to guess your employees' addresses and start sending targeted phishing emails. Another common vulnerability is a lack of employee awareness about these phishing scams. I remember speaking with a business owner who was devastated after their entire system was locked down by ransomware. It all started with one employee clicking a link in a seemingly harmless email. That one click cost them thousands.
This brings us to a vital point: email security for small businesses isn't just a tech issue; it’s a business survival issue. Your reputation, your cash flow, and your customer relationships are all at risk. Small businesses are increasingly targeted, and the stats are pretty grim. A staggering 46% of all cyber breaches hit businesses with fewer than 1,000 employees, and these businesses are bombarded with malicious emails at a rate of one in 323. The resulting financial and reputational damage can be crippling. In 2021, 61% of small and medium-sized businesses were targeted by cyberattacks, with malware being the most common attack vector at 18%. For a deeper dive into these unsettling trends, check out this resource on small business cybersecurity statistics.
Here's another insightful article you might find helpful: Email Security for Small Business: Protect Your Data Now
Think of it this way: you wouldn’t leave your front door unlocked, right? Email security is the digital lock on your business. And these days, that lock needs some serious reinforcement. Hoping for the best isn't a strategy. You need to be proactive. Understanding why your business is a target is the first step toward building a solid defense.
Understanding the Risks: Why Small Businesses Are Targeted
Let's take a closer look at why small businesses are so often in the crosshairs of cybercriminals:
- Limited Resources: Smaller businesses often have tighter budgets, which can mean less investment in robust security solutions and dedicated IT staff.
- Less Sophisticated Security: This can translate to outdated software, weaker passwords, and fewer security protocols in place.
- Valuable Data: Even small businesses hold valuable data that cybercriminals crave, from customer information to financial records.
- Employee Vulnerability: Employees are often the weakest link in the security chain. They may be more susceptible to phishing scams and other social engineering tactics.
To illustrate the difference in impact, let's look at some real-world data. The table below compares cyberattack statistics for small businesses versus larger enterprises:
Small Business vs. Enterprise Cyber Attack Statistics
| Business Size | Attack Rate | Average Detection Time | Financial Impact |
|---|---|---|---|
| Small Business | High (e.g., 1 in 323 emails containing malware) | Often longer due to limited resources | Can be devastating, potentially leading to business closure |
| Enterprise | Lower (more resources for defense) | Typically shorter due to dedicated security teams and advanced tools | Significant but often less crippling due to greater financial stability |
As you can see, the impact of a cyberattack on a small business can be far more severe, highlighting the critical need for effective email security measures. While larger companies have more resources to detect and respond to threats, small businesses can face significant financial strain and even closure. This is why taking proactive steps to secure your email is not just a good idea; it's essential.
Understanding Business Email Compromise Attacks

Business Email Compromise (BEC) attacks… they're the kind of thing that keeps small business owners up at night. And honestly, they're a lot more common – and a lot sneakier – than you might think. Forget your typical spam email; these attacks are carefully planned, personalized, and designed to take advantage of the trust and fast-paced communication that’s just part of doing business. Instead of a smash-and-grab, it’s more like a con artist picking a lock.
Let's break down how these attacks usually unfold. First, there's the intel gathering. Attackers do their homework, studying your business connections, how you communicate, and your online presence. They’re looking for weak points, any little detail they can use to their advantage. This can go on for weeks, even months, as they build credibility, pretending to be a trusted supplier, a higher-up in your company, or even a close business contact.
Then comes the sting – often disguised as a perfectly normal request for a wire transfer or access to sensitive data.
What makes BEC attacks so dangerous is they rely on social engineering, not technical hacking. They exploit human nature, using tricks like pretexting to create convincing stories and manipulate their victims. Imagine getting an email from your CEO needing a wire transfer for a time-sensitive deal. It sounds legitimate. And that’s the point. Your regular spam filters often miss these attacks because they don't have the usual red flags of a malicious email.
Small businesses are especially vulnerable to BEC attacks. For companies with less than 1,000 employees, there’s a 70% weekly probability of facing at least one BEC attempt. And these attacks aren't just frequent; they're expensive too, with the average wire transfer request reaching $24,586 as of early 2025. Because they rely on human error, small businesses, which may not have the budget for extensive cybersecurity training or fancy email security tools, are prime targets. The rise of BEC attacks underscores the need for better defenses. Want a deeper dive into these stats? Check out business email compromise statistics.
Here’s another helpful resource: Business Email Compromise Prevention: Your Complete Guide. Understanding how these attacks work is the first step in protecting your business. Learn to spot the subtle warning signs, understand the psychological tactics used by attackers, and you’ll be much better prepared. Remember, email security isn’t just about technology; it’s about human awareness. That’s the key to real protection.
Building Your Email Security Foundation
Okay, let's get down to brass tacks. We're going to build email security that actually works for your small business—without breaking the bank or driving your team crazy. Think of it as building digital armor, and we'll start with two-factor authentication (2FA) that your employees will actually use.
Two-Factor Authentication: Double the Protection
Seriously, I can't overstate how crucial 2FA is. It’s like adding a deadbolt to your front door. Even if someone guesses your password (the first lock), they’ll still need that second factor—usually a code from your phone—to get in. This drastically reduces the risk of unauthorized access, even if passwords are somehow leaked.
Think about this: 43% of data breaches target small and medium-sized businesses. It's not if you'll be a target, but when. Setting up 2FA isn't about being paranoid, it's about being prepared. And choose a 2FA method that’s easy for your team. An authenticator app like Google Authenticator or Authy is usually more secure than SMS codes.
Email Authentication Protocols: SPF, DKIM, and DMARC
Next up: SPF, DKIM, and DMARC. These are the unsung heroes of email authentication. They work behind the scenes to verify that emails coming from your domain are actually from you. SPF (Sender Policy Framework) tells everyone which mail servers are allowed to send emails on your behalf. DKIM (DomainKeys Identified Mail) adds a digital signature to your outgoing emails, like a tamper-proof seal. And DMARC (Domain-based Message Authentication, Reporting & Conformance) ties SPF and DKIM together, telling receiving servers what to do with emails that fail authentication.
Setting these up might sound complicated, but it’s often easier than you think. Many email providers have simple interfaces to walk you through it. Think of it as setting up a burglar alarm for your email. It won’t stop all threats, but it makes things much harder for impersonators trying to use your domain for phishing scams.
Choosing The Right Email Provider and Maximizing Existing Tools
Your email provider is a big part of your small business email security. Look for providers that offer built-in security features like spam filters, antivirus protection, and data loss prevention tools. You’re probably already paying for some security features—make sure you’re actually using them! Take some time to explore your email settings. You might be surprised at what you find.
This screenshot shows the Microsoft 365 admin center. It's a central hub for managing a bunch of security settings. Here you can control everything from user access and multi-factor authentication to more advanced threat protection and data loss prevention. You can also keep tabs on security alerts and set up policies to protect your business from email threats. This centralized control makes it easier to manage and keep consistent security practices across your whole organization.
Finally, remember that security is an ongoing effort. Regularly check your settings, keep your software updated, and stay aware of the latest threats. Small businesses might be tempting targets, but with a solid security foundation, you can make yourself a much tougher target.
The Hidden Costs of Delayed Breach Detection

Let's talk about something that keeps security folks awake at night: the attacks you don't know about. The truth is, most breaches simmer under the surface for months. And while you're unaware, attackers are quietly picking your business apart.
Think of it like a tiny leak in a pipe. A small drip seems harmless at first, but eventually leads to serious water damage. A subtle breach is similar. Little by little, data disappears, accounts are compromised, and malware gets planted, setting the stage for a major system meltdown. Email security is crucial, especially for small businesses, yet vulnerabilities remain widespread.
Here's a real-world scenario: an employee falls for a phishing scam, giving attackers access to their email. The attackers might start small, tweaking forwarding rules to intercept sensitive emails. Weeks or months go by as they gather information, learning about your operations and identifying valuable targets. By the time you discover the breach, the damage can be devastating. Email security is a major concern for small businesses because data breaches are so common. A staggering 43% of all data breaches target small and medium-sized businesses (SMBs). Even more alarming? It takes an average of 207 days to detect a breach, leaving businesses exposed for over half a year. That’s plenty of time for attackers to exploit sensitive information like customer data, which, by the way, 87% of small businesses store. The threats are real: phishing, malware, and spoofing all prey on human error and can cause serious financial and reputational harm. Boosting email security is crucial for mitigating these risks and protecting your business from ever-evolving cyber threats. For a deeper dive into this, check out this helpful resource.
The Ripple Effect of Undetected Breaches
Data loss is just the tip of the iceberg. A delayed breach detection triggers a chain reaction of problems:
- Financial Losses: Think ransomware payments, lost productivity, legal fees – it all adds up.
- Reputational Damage: A breach can shatter customer trust and damage partnerships, leading to lost business and long-term reputational harm.
- Regulatory Compliance Violations: Depending on your industry, failing to protect sensitive data can result in significant fines.
- Operational Disruptions: A breach disrupts daily operations, impacting customer service, project deadlines, and overall productivity.
Recognizing the Subtle Signs of a Breach
The tricky thing about ongoing attacks is they often hide in plain sight. This is why proactive monitoring is essential. Minor system slowdowns, unusual email patterns, or unexpected login attempts might seem insignificant individually. But together, they can point to a much bigger issue.
Imagine a sudden spike in website traffic at unusual hours, or employees reporting intermittent email issues. These could be signs of a distributed denial-of-service (DDoS) attack or a compromised email account. The takeaway? Don't dismiss seemingly small problems. Investigate them thoroughly. Early detection is your best defense against a catastrophic breach.
Training Your Team to Spot Threats
Let's be honest, your employees are the front line in the fight against cyberattacks. They can be your strongest asset or your weakest link. The difference? Smart security training. Forget the death-by-PowerPoint and the scary stories. Those might get attention, but they don't build lasting skills. What you really need is a security-conscious culture. This not only strengthens your defenses but can actually make everyone more productive.
Phishing Simulations: Turning Mistakes into Learning Opportunities
Think of phishing simulations like fire drills for your inbox. The goal isn't to point fingers, but to create learning opportunities. A good phishing simulation lets people experience a real-world threat in a safe environment. Instead of feeling ashamed, they learn and grow.
For example, I once ran a simulated phishing campaign and tracked who clicked. Then, I followed up with specific training for those who got caught. This personalized approach really made the training stick.
Real-World Scenarios: Making Security Training Stick
The best training uses real-world examples. Sharing stories of actual Business Email Compromise (BEC) attacks and discussing how to avoid them makes the threat much more real.
Also, consider scenarios specific to your business. If you handle financial transactions, for example, work through examples of suspicious payment requests. This practical approach helps your team connect their training to their everyday work.
The Psychology of Security Awareness: Building a Culture of Vigilance, Not Fear
Good email security training focuses on the human element without resorting to fear-mongering. You want to empower employees to be careful without paralyzing them with worry.
Explain why security measures are in place. When people understand the reasoning behind the rules, they’re more likely to follow them. One key tip is to make reporting suspicious emails easy and consequence-free. Reward people for reporting – even false alarms. This builds a culture of vigilance and encourages shared responsibility.
To illustrate the effectiveness of different training approaches, let's look at the following table:
Table: Email Security Training Effectiveness by Method
| Training Method | Employee Retention Rate | Threat Recognition Improvement | Implementation Cost |
|---|---|---|---|
| Annual Security Awareness Training (PowerPoint) | 30% | 15% | Low |
| Regular Phishing Simulations with Targeted Follow-up | 75% | 60% | Medium |
| Interactive Security Games and Quizzes | 60% | 40% | Low |
| Real-World Scenario Training with Group Discussions | 80% | 70% | High |
As you can see, more interactive and engaging methods, like phishing simulations and real-world scenario training, tend to yield significantly better results in terms of employee knowledge retention and threat recognition. While these may have a higher upfront cost, the long-term benefits in terms of reduced risk make them worthwhile investments.
Keeping Security Awareness Fresh: The Ongoing Challenge
Security awareness isn't a one-time thing. Threats evolve constantly, which means your training should, too. Regular refreshers are key. Short quizzes, interactive games, or even friendly competitions can keep security top-of-mind.
As your team grows, incorporate security training into onboarding. This sets a strong foundation from day one. By making security an ongoing priority, you continually strengthen your defenses and adapt to the ever-changing landscape of online threats.
Advanced Protection Strategies That Actually Work
Okay, so you've nailed the email security basics. But you're smart enough to know that's not where it ends. You want to take your small business email security to the next level. Excellent! You absolutely don't need a massive budget to get serious protection. Let's dive into some advanced strategies that actually make a difference.
Practical Email Encryption: Keeping Your Data Confidential
I know what you’re thinking: email encryption sounds like a headache. Truth is, it can be, if you pick the wrong system. If it's clunky and complicated, nobody will use it. Your team will revert to old habits, and clients will just shrug and move on. Trust me, I've seen it happen.
The trick is to find a solution that integrates smoothly with what you’re already using. One-click encryption is the goal. Something easy and intuitive.
For example, I’ve had good experiences with small businesses using ProtonMail or Tutanota for end-to-end encryption. They strike a nice balance between strong security and user-friendliness. The key takeaway here? Prioritize practical encryption that fits your workflow, not some overly complex system that gathers dust after a week.
Automated Threat Detection: Intelligent Security Working in the Background
Think of automated threat detection as having a tireless virtual security guard constantly monitoring your inbox. These systems use artificial intelligence (AI) to scrutinize incoming emails, catching suspicious stuff before it even lands in your employees' inboxes. This is where AI truly shines in email security. It’s not about replacing human intelligence; it's about making your team that much more effective.
Here’s a peek at the Microsoft Security portal. It shows just how much information is now available to help businesses understand and manage their security, from threat protection and vulnerability management to overall security scoring. It really highlights the powerful tools even small businesses can access. Having this kind of overview, even without a dedicated IT security team, is a game-changer.
These automated systems are designed to spot malicious links, dodgy attachments, and even those sneaky phishing attempts that can slip through traditional filters. And they learn and adapt over time, getting better at identifying emerging threats. It's a proactive approach that minimizes the risk of human error, adding a crucial layer of always-on protection.
Backup and Recovery: Your Safety Net
Let's be realistic: even with the strongest defenses, breaches can still occur. That’s why a solid backup and recovery plan is non-negotiable. It's your safety net, your plan B. Regularly backing up your email data means that even in a worst-case scenario, you can restore everything quickly and minimize any disruption.
You might be interested in this: 8 Email Security Best Practices to Implement Now
Look for a backup solution that’s secure, dependable, and easy to manage. Cloud-based options are worth considering for offsite storage, and remember to test those backups regularly! This isn't just about recovering data; it's about business continuity. A robust backup and recovery plan can be the difference between a minor hiccup and a major disaster. Being able to quickly restore your email communications is vital for keeping your customers happy and your operations running smoothly. Having that plan in place gives you peace of mind, knowing you can bounce back quickly if anything goes wrong. It's a foundational piece of comprehensive small business email security.
Your Email Security Action Plan
Okay, so we've covered a lot of ground on email security. Now, how do we actually do this stuff? Let's create a practical plan you can use right now. Think of it as phases, starting with some quick wins you can knock out this week, then moving on to bigger things down the line. We'll keep it realistic, budget-friendly, and focus on the changes that’ll give you the biggest bang for your buck.
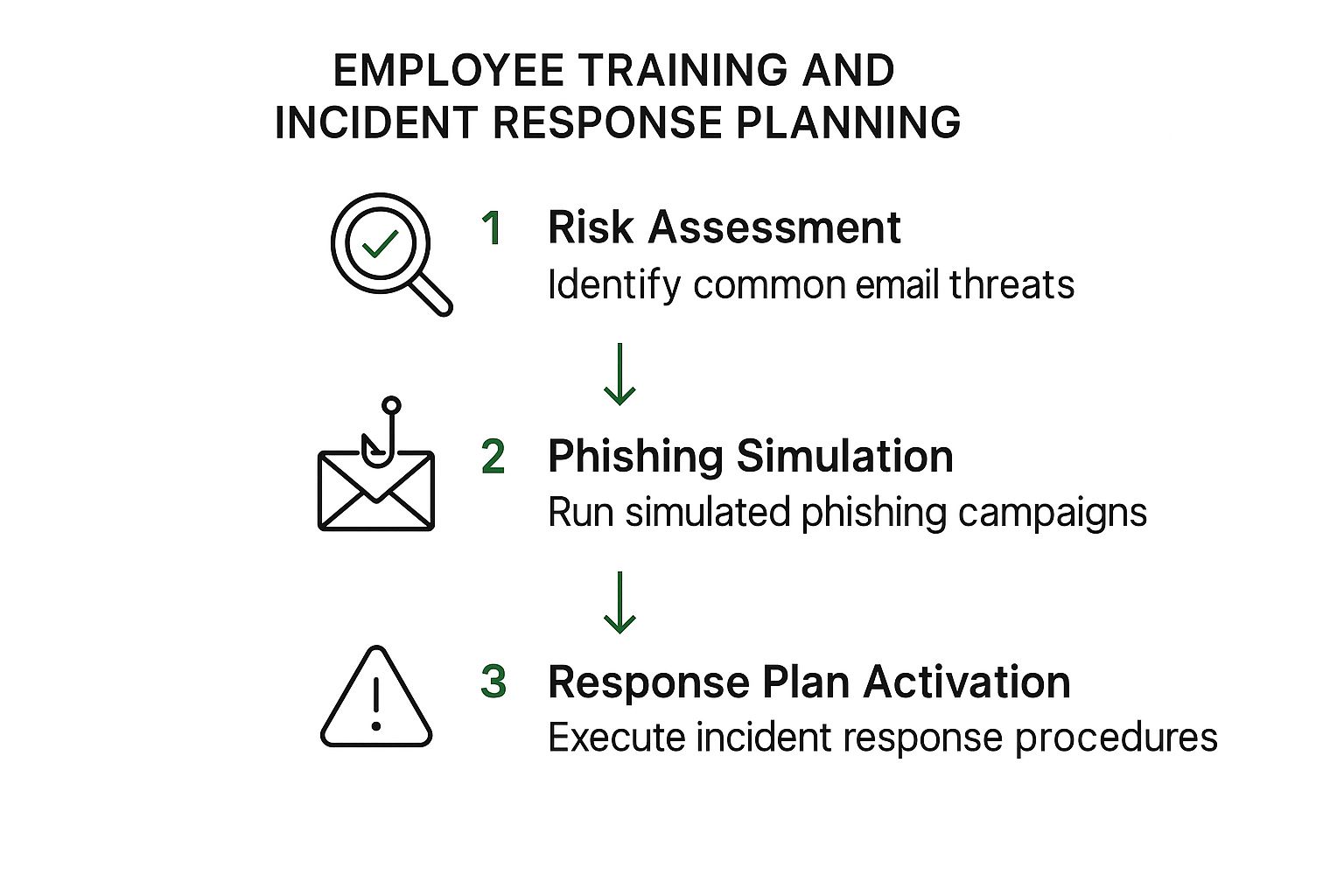
That infographic above shows a simple workflow for improving your team’s training and incident response. You start by looking at the risks you face – what are the most common email threats for small businesses? Then you test your team with some phishing simulations. Finally, you make sure you've got a clear response plan in place, just in case. This visual really drives home how important it is to know the risks, prepare your people, and have a plan ready to go. It's all about being proactive and turning your team into a security asset, not a vulnerability.
Quick Wins: This Week's To-Do List
- Enable 2FA: Seriously, if you do nothing else this week, turn on two-factor authentication (2FA) on every single email account. It’s the single best thing you can do right now to boost security.
- Review Email Settings: Take a few minutes to poke around your email provider’s security settings. Make sure your spam filters and antivirus protection are turned on and up-to-date. You might be surprised what's lurking in there.
- Quick Security Awareness Training: Get your team together for a short training session on common phishing scams. Even a quick 15-minute chat can make a world of difference.
Mid-Term Goals: Within the Next Month
- Implement SPF, DKIM, and DMARC: These email authentication protocols sound complicated, but they’re essential for stopping email spoofing and phishing. They're like a digital signature for your emails, making it much harder for bad actors to impersonate you.
- Advanced Phishing Simulation: Take your phishing simulations to the next level. Run a more in-depth test to see where your team's vulnerabilities are. This will help you tailor your training and make it even more effective.
- Develop an Incident Response Plan: What happens if (or when) someone clicks on a bad link? Having a documented incident response plan will help you contain the damage and get back on your feet quickly. It's like a fire drill for your email.
Long-Term Strategy: Ongoing Improvements
- Explore Advanced Threat Detection: As your business grows, you might want to look into automated threat detection systems. These systems can help you catch sophisticated attacks that might slip through traditional defenses.
- Regular Security Awareness Training: Security is a marathon, not a sprint. Regular training sessions will keep your team up-to-date on the latest threats and best practices. I like to do a quick refresher every quarter.
- Data Backup and Recovery: This isn't strictly email security, but it's crucial. A solid backup and recovery plan will save your bacon if you ever get hit with ransomware or a major data loss incident.
Whether you're handling security yourself or have someone else on it, these checklists and procedures will keep you in good shape. This isn’t just theory; it's the practical stuff that successful small businesses use every day. Ready to take control of your email security? Check out Typewire, a secure and private email platform designed for businesses just like yours. You can even start with a free trial: https://typewire.com

