Data breach prevention is more than just a set of security measures; it's a strategic philosophy. It’s about creating a layered defense that combines the right technology, smart policies, and, most importantly, well-trained people to stop attackers from getting their hands on your sensitive information. This isn't just about defense; it's about proactively protecting your company's most critical assets: its data and its hard-won reputation.
Building Your Modern Defensive Framework
Let's be real—the old way of dealing with security threats just doesn't cut it anymore. Waiting for a disaster and then scrambling with a dusty checklist is a recipe for failure. Modern security demands a complete shift in mindset, moving away from reactive damage control and toward proactive threat hunting. It’s about building a living, breathing framework where technology, processes, and people all work together as a single, unified defense.
This framework isn't something you just buy and install. It needs to be woven into the very fabric of your company culture. The ultimate goal is to move beyond simply checking compliance boxes and cultivate an environment where everyone is security-conscious. When every team member understands their role in protecting data, they stop being potential liabilities and become your greatest security asset—your human firewall.
Understanding the Core Pillars
A truly effective data breach prevention plan rests on a few essential pillars. If you neglect one, the others can't hold up the structure, no matter how strong they are. I like to think of it like a medieval fortress; you can have the tallest, thickest stone walls, but they're worthless if you leave the main gate wide open.
Here's a quick look at the essential components for a comprehensive and modern data breach prevention strategy.
Core Pillars of Data Breach Prevention
| Pillar | Focus Area | Primary Goal |
|---|---|---|
| Technological Controls | Hardware & Software | To create a robust digital shield using firewalls, encryption, and endpoint protection. |
| Procedural Policies | Documented Guidelines | To establish clear rules for data handling, access control, and incident response. |
| The Human Element | People & Training | To empower employees to recognize and report threats through ongoing security awareness. |
These pillars work in concert to create a defense-in-depth strategy that protects your organization from multiple angles.
The infographic below really drives home how critical both the financial and human sides of this equation have become.
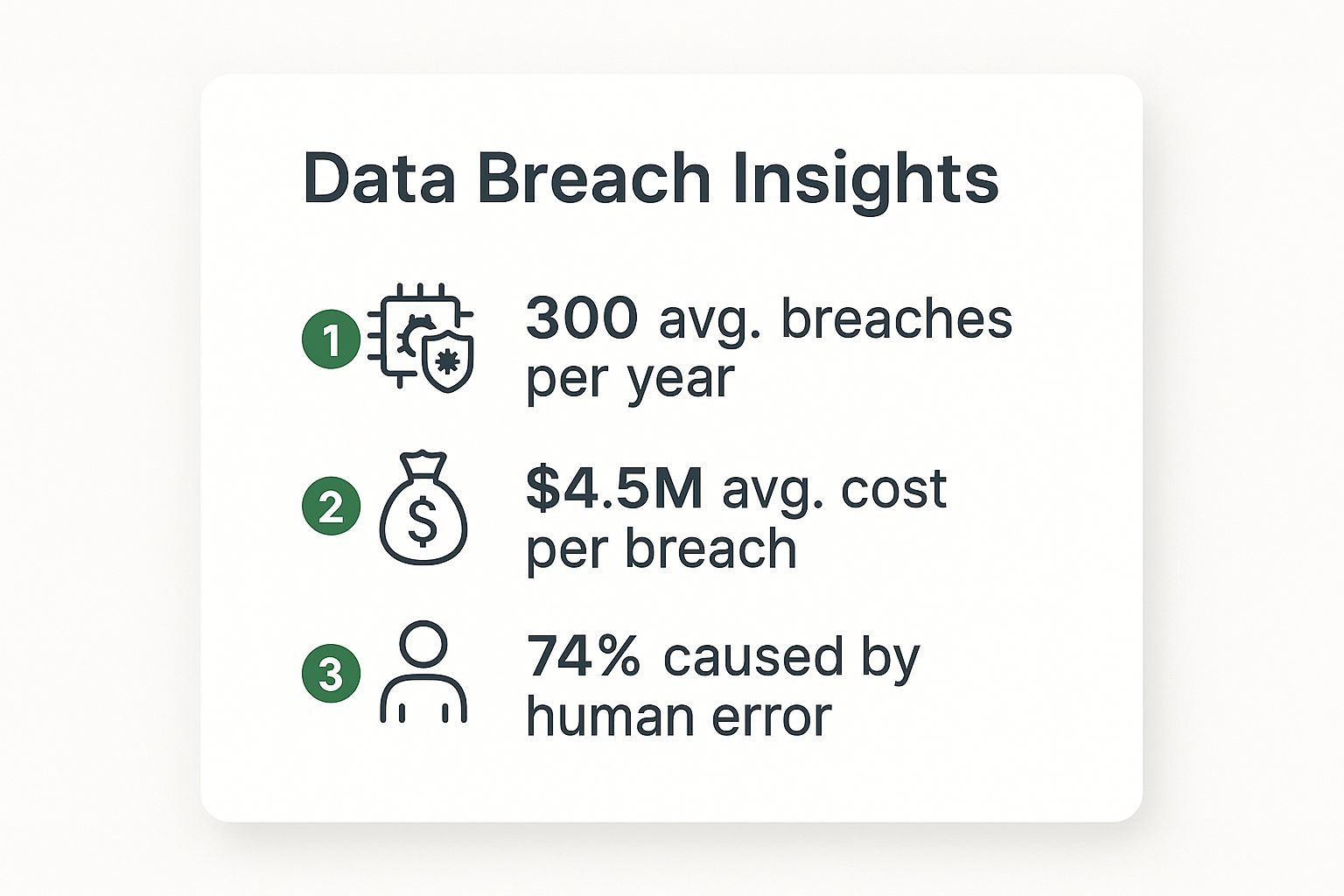
The numbers don't lie. Breaches are incredibly expensive, and a huge percentage of them can be traced back to human error. This data is a powerful reminder that any security strategy that doesn't prioritize its people is destined to fail.
The Financial Imperative for Prevention
Investing in proactive data breach prevention isn't just an IT line item—it’s one of the smartest business decisions you can make. The financial devastation from a single breach can be staggering, quickly piling up from regulatory fines, legal battles, lost customers, and irreversible brand damage.
The real cost of a breach extends far beyond the initial cleanup. It's the slow erosion of customer trust, the competitive disadvantage, and the long-term reputational harm that can cripple a business for years.
And the stakes are only getting higher. By 2025, the global cost of cybercrime is projected to hit an eye-watering $10.5 trillion a year, growing by 15% annually. This explosive growth sends a clear message: being unprepared is no longer an option.
Being prepared means having a solid incident response plan that outlines exactly how you'll detect, contain, and communicate during a crisis. You can learn more about the staggering financial impact and the need for readiness by digging into the latest data breach statistics. This groundwork is essential for understanding the actionable strategies we're about to cover, giving you a clear path to protecting your business in today's threat-filled environment.
Hardening Your Technical Defenses

Let's get down to the nuts and bolts. Your technology stack can either be your strongest shield or your biggest liability. To genuinely prevent a data breach, you have to move past simply installing antivirus software and get your hands dirty with the technical controls that form the real foundation of your security.
This isn't a "set it and forget it" task. These defenses need constant attention, regular updates, and smart configuration to stay ahead of attackers who are always changing their game. Think of it as reinforcing a fortress, brick by brick, making sure there are no cracks for an intruder to slip through.
Secure Your Primary Gateway: Email
It's no secret that email is the #1 attack vector for cybercriminals. Phishing attacks are behind a staggering number of security incidents, which makes advanced email security an absolute must. Your provider's default spam filter just won't cut it against the sophisticated, socially-engineered attacks we see today.
To truly lock down this critical channel, you need a multi-layered defense. This means implementing tools that can analyze links in real-time, detonate attachments in a safe sandbox environment, and spot impersonation attempts before they ever hit an employee's inbox. Proper setup here is everything. For a deeper dive, check out our complete guide to email security threats.
Implement Practical Multi-Factor Authentication
If you do only one thing on this list, make it multi-factor authentication (MFA). A massive number of breaches start with stolen or weak credentials. MFA stops this dead in its tracks by requiring a second piece of proof, making a stolen password useless by itself.
But how you roll it out matters. A clunky, frustrating MFA system will just lead to employee burnout and people looking for ways to get around it.
- Go with push notifications. They're so much friendlier than asking someone to type in a six-digit code from an app.
- Use trusted devices. Allow users to mark their main work computer as "trusted" to cut down on unnecessary prompts in a secure, known location.
- Be strategic. Start by applying MFA to your most critical systems—email, VPN access, and anything with admin privileges.
A common mistake I see is treating all MFA as equal. SMS codes are better than nothing, but they're vulnerable to SIM-swapping attacks. Whenever you can, push for app-based authenticators or, even better, physical security keys. That’s where you get the highest level of protection.
Encrypt Everything, Everywhere
Encryption is your last line of defense. If an attacker somehow gets past everything else and grabs your files, strong encryption makes sure all they have is unreadable nonsense. This isn't just a suggestion; it should be a mandate for data in all its forms.
Data at Rest: This is your data sitting on servers, hard drives, and in databases. Use full-disk encryption like BitLocker for Windows or FileVault for Mac on every single company laptop. Your cloud storage and databases should also be encrypted by default.
Data in Transit: This is data zipping across your internal network or the internet. Enforce TLS/SSL on all web traffic and use encrypted connections, like a VPN, for anyone accessing the network remotely. This prevents anyone from snooping on the data as it travels.
Create Digital Barriers and Moats
Not every part of your network needs to talk to every other part. The practice of network segmentation—dividing your network into smaller, isolated zones—is a game-changer for damage control.
For instance, your guest Wi-Fi should be completely walled off from your internal corporate network. No exceptions. Likewise, the servers holding sensitive financial data have no business being on the same network segment as the marketing department's computers. If one area is breached, the attack is contained. It’s the difference between a localized fire and the whole building burning down.
This strategy goes hand-in-hand with the principle of least privilege. Every user and every system should only have access to the bare minimum they need to do their job. A marketing intern doesn’t need access to HR files. The accounting software doesn't need to communicate with the development servers. By being ruthless with these boundaries, you shrink your attack surface and drastically limit the blast radius of any successful intrusion.
Using AI for Proactive Threat Hunting

Let's be realistic: your security team, no matter how sharp, is outmatched. Attackers are using automation to bombard defenses with thousands of attempts every minute. The only way to keep up is to fight automation with better automation. This is where Security AI fundamentally changes the game.
Instead of just chasing down alerts after the fact, AI-powered systems are constantly on the hunt. They sift through massive amounts of data—network traffic, login attempts, file access patterns—in real-time, looking for the tiny, almost invisible signs of an active attack. A human analyst might eventually spot that a single user account logged in from two different continents within minutes of each other, but an AI will catch it instantly.
From Reactive to Predictive Defense
The real power of AI in security is its ability to learn what "normal" looks like for your specific organization. This isn't a static set of rules you program once; it's a living, breathing understanding of your day-to-day operations that adapts over time.
When any activity deviates from this established baseline, the AI can flag it for your team or, even better, trigger an automated response. This is the crucial shift from a reactive security posture to a predictive one. You start stopping intrusions before they can blossom into full-blown, headline-grabbing data breaches.
Here’s how this plays out in the real world:
- Smarter Phishing Filters: Forget basic keyword matching. AI-driven email security analyzes the sender’s reputation, the context of the message, and even the underlying code of links and attachments. It's built to catch the sophisticated, targeted spear-phishing campaigns that sail right past traditional filters.
- Automated Response Workflows: Imagine an AI notices an employee account suddenly downloading an unusual volume of sensitive files at 3 AM. It can instantly lock the account, sever its network connection, and generate a high-priority ticket for your security team to investigate when they start their day. This all happens in seconds.
This kind of rapid response is a massive advantage. The data below shows just how much faster organizations using AI can shut down threats.

The key takeaway here is how dramatically AI shrinks an attacker’s window of opportunity. It reduces the time they have inside your network from months down to just days.
The financial impact is just as significant. Research shows that as of 2025, roughly 61% of organizations have adopted some level of security AI. These companies don't just identify and contain breaches nearly 100 days faster than their peers; they also see an average cost saving of $2.2 million. You can dig deeper into how AI is changing the security landscape by reviewing the latest data breach statistics on Spacelift.io.
Integrating AI Security Tools and Biometrics
Choosing the right AI security tools is key. Start by identifying your greatest vulnerabilities. Is it email-based threats? Insider risks? Network intrusions? Pick a solution that excels in that area first, then expand. Look for platforms with intuitive dashboards that play nicely with your existing security tools to avoid adding unnecessary complexity.
A common mistake I see is companies investing in a powerful AI tool without dedicating the time to tune it properly. If you don't, you'll just get hammered with false positives, and your team will quickly start ignoring the alerts—defeating the whole purpose.
On top of AI, biometrics add a uniquely personal layer of security. Using fingerprints, facial recognition, or even behavioral patterns like typing cadence for authentication makes it incredibly difficult for an attacker to use stolen credentials. When you integrate biometrics into your multi-factor authentication (MFA) strategy, you create a nearly foolproof way to verify user identity, which is a cornerstone of modern data breach prevention.
Navigating Third-Party and Supply Chain Risk

You can build the most secure digital fortress imaginable, but it won’t matter if you give a key to a partner who leaves it on the sidewalk. That, in a nutshell, is the reality of supply chain risk. Every single vendor, contractor, or SaaS tool you bring into your ecosystem is a potential backdoor into your network.
To truly prevent data breaches, you have to look beyond your own four walls and start scrutinizing the security of everyone you do business with. The uncomfortable truth is that you’re only as secure as your weakest link. A vulnerability in what seems like a minor third-party app can easily spiral into your next major security headache.
Before You Sign on the Dotted Line
The vetting process is your first, and arguably most important, line of defense. Too often, security is treated like an afterthought—a simple checkbox on a procurement form. It needs to be a core part of your evaluation, right up there with price and functionality.
Before you even think about integrating a new partner or tool, you have to do your homework with thorough security due diligence. This goes way beyond asking if they're "secure." You need to ask for proof.
- Request Security Documentation: Ask to see their security policies, the results from recent penetration tests, and any relevant certifications like SOC 2 Type II or ISO 27001. A vendor who takes security seriously will have this information ready to go.
- Issue a Security Questionnaire: Use a standardized framework to dig into their specific controls. Something like the Consensus Assessments Initiative Questionnaire (CAIQ) is great for covering everything from their encryption standards to their incident response plan.
- Scrutinize Data Handling: Get crystal-clear answers on what data they'll access, how it will be stored, and who on their team can see it. If their answers are vague, that’s a huge red flag.
This isn't just a compliance exercise; it’s a way to gauge their security culture. A vendor that gets hesitant or defensive when you ask these questions is telling you everything you need to know.
Writing Security Clauses with Teeth
Your contract is where the rubber meets the road. Vague promises of "best-practice security" are completely worthless. Your agreements need specific, enforceable clauses that spell out exactly what you expect and what happens if they fail to meet those expectations.
A common mistake is simply accepting a vendor's standard contract without pushing for security amendments. Your legal and security teams must collaborate to embed your specific requirements into the final agreement. If they won't agree to reasonable terms, be prepared to walk away.
Here are a few clauses that should be non-negotiable:
- Right to Audit: This gives you the contractual right to assess their security controls, whether you do it yourself or hire a third-party auditor.
- Breach Notification: The contract must define a strict timeframe for them to notify you of a security incident that affects your data. This should be within 24 to 48 hours, not weeks.
- Data Handling and Destruction: Clearly define how your data must be encrypted, where it's stored, and—critically—how it will be securely destroyed when your business relationship ends.
- Liability and Indemnification: The agreement must clearly state their financial responsibility if a breach on their end leads to damages on yours.
These clauses create real accountability. They make sure your security standards extend to everyone who touches your data, effectively making your partners an extension of your own defense.
This comprehensive view of risk is becoming more critical every single year. The chart below visualizes the various pathways attackers are using to breach organizations today.

Notice the significant role of vulnerability exploitation—a common way attackers compromise supply chain partners.
This visual highlights a critical finding from the latest research: third-party involvement in breaches has doubled year-over-year. This surge is largely driven by attackers exploiting these exact kinds of vulnerabilities. Despite growing awareness, a shocking number of these perimeter-device weaknesses remain unpatched, leaving the door wide open. You can find more powerful insights on evolving cyber threats by reading the full 2025 Data Breach Investigations Report from Verizon.com. This reality reinforces the urgent need for a proactive and resilient approach to managing your entire supply chain.
Have a Battle-Ready Incident Response Playbook
Let's be realistic for a moment. Even with the best defenses in the world, you have to assume that a security breach is a matter of when, not if. The real difference between a contained security event and a full-blown disaster is having a well-rehearsed Incident Response Plan (IRP). This isn't just a document you write and forget; it's a living playbook your team needs to know inside and out.
When things go sideways, panic is the enemy. A solid IRP eliminates the guesswork and frantic scrambling, guiding your team with a clear, coordinated, and efficient reaction. Without one, people get lost, critical steps are missed, and the damage from a breach can snowball with every passing hour.
Who's on Your Response Team?
First things first: build your response team. A breach isn't just an IT problem—it's a business problem. That means you need people from across the company at the table.
Your team should absolutely include folks from:
- IT and Security: These are your technical front-line soldiers. They’re the ones who will actually find, contain, and kick out the threat.
- Executive Leadership: You need someone with the authority to make the tough calls, like approving emergency spending or deciding to take a critical system offline.
- Legal Counsel: The minute a breach is confirmed, you're on the clock with breach notification laws. Legal has to navigate this minefield.
- Human Resources: Was an employee involved? HR will lead any internal investigations and handle the fallout.
- Communications/PR: They become your single source of truth, managing the message to employees, customers, and the public.
Get crystal clear on who does what before a crisis hits. Who makes the final call on shutting down a server? Who is the only person allowed to speak to the media? Any ambiguity here will come back to bite you.
The 6 Phases of a Real-World Response
A truly effective IRP follows a proven, six-phase structure. Knowing these phases helps you move methodically from the initial alert all the way through to the final post-mortem.
| Phase | What You're Trying to Do | What It Looks Like in Practice |
|---|---|---|
| Preparation | Get your house in order. | Write the IRP, assemble the team, get the right tools, and train everyone. |
| Identification | Figure out if it's real and how bad it is. | Dig into alerts, pour over logs, and determine the scope and severity of the incident. |
| Containment | Stop the bleeding. Fast. | Isolate the infected machines, segment your network, and cut off the attacker's access. |
| Eradication | Get the intruder out for good. | Remove the malware, patch the vulnerabilities, and force-reset every compromised password. |
| Recovery | Carefully bring things back to normal. | Restore systems from clean backups, double-check their security, and monitor like a hawk. |
| Lessons Learned | Don't make the same mistake twice. | Hold a no-blame post-incident review and update your playbook with what you learned. |
Each of these phases is non-negotiable. I've seen teams try to rush from containment straight to recovery without proper eradication, only to find the attacker waltzing right back in a week later.
Practice Makes Permanent: Run Tabletop Exercises
A plan on paper is just a piece of paper. You have to pressure-test it to see where it breaks. This is where tabletop exercises are invaluable. These are basically fire drills for your security team, where you walk through a realistic breach scenario.
A tabletop exercise is the closest you'll get to a real crisis without the actual damage. It's your chance to find the flawed assumptions, communication gaps, and weak spots in your plan before an attacker does it for you.
Run these drills at least twice a year. Kick things off with a classic scenario, like a phishing email that escalates into a full-blown ransomware attack. As the facilitator, throw curveballs at them: "The attacker just posted on social media that they have your customer data," or "A reporter is on the phone asking for a comment." Watch how your team communicates, follows the plan, and makes decisions under fire. This is how you build the muscle memory needed for a real-world event.
For any organization serious about hardening its defenses, protecting sensitive communications is a top priority. For some practical, hands-on advice, check out our data loss prevention email setup guide, which offers real-world configurations for protecting one of your most vulnerable attack vectors. At the end of the day, it’s this proactive planning and practice that turns a reactive group into a truly resilient one.
Frequently Asked Questions About Data Breach Prevention
When you're in charge of protecting sensitive information, you'll inevitably run into some tough questions. Getting clear, practical answers is essential for making the right calls for your organization. Let's dig into some of the most common and critical questions that come up when building a solid data breach prevention strategy.
This isn't about repeating textbook definitions. It's about giving you actionable advice you can put to work immediately.
What Is the Single Biggest Cause of Data Breaches?
If you cut through all the technical noise, the answer is almost always human error. This is usually kicked off by social engineering, especially convincing phishing emails. It just takes one clever message and one employee who's a little distracted to click a bad link, and suddenly an attacker is inside your network.
Sure, technical vulnerabilities are a real threat, but that split-second human mistake is still the most common way attackers get their foot in the door. This is exactly why consistent security awareness training is just as vital for data breach prevention as any firewall or fancy software. A sharp, well-informed team is your best first line of defense, period.
How Can a Small Business Prevent Breaches on a Tight Budget?
You don't need a Fortune 500 security budget to make a real difference. By focusing on the fundamentals that give you the most bang for your buck, even the smallest businesses can build a respectable defense against the most common threats.
For the highest impact, focus your resources here:
- Enforce Multi-Factor Authentication (MFA) on every important account, starting with email and admin logins. This one action shuts down the threat of stolen passwords.
- Create a strong password policy, but don't stop there. Pair it with regular, engaging security training that teaches your team how to spot and report phishing attempts.
- Keep all your software updated. Seriously. Patching known vulnerabilities is one of the most effective security moves you can make, and it costs you nothing but a little time.
- Back up your critical data often and keep it offline or separate from your main network. This is your get-out-of-jail-free card in a ransomware attack.
These foundational steps create a surprisingly powerful defense against the vast majority of attacks you'll face, all without breaking the bank.
A lot of people think cybercriminals only go after big corporations. The reality is that small businesses are often seen as easier targets because they’re assumed to have weaker defenses. Don't fall into that trap—mastering the basics is your strongest move.
Does Cyber Insurance Mean I Don't Need a Prevention Strategy?
Absolutely not. That’s a dangerous way of thinking that can lead to disaster. Think of cyber insurance as a financial safety net, not a replacement for a solid prevention plan. It’s there to help cover costs after a breach happens—things like legal fees, customer notifications, and recovery services.
Insurance does nothing to stop the breach in the first place, nor can it fix the often-permanent damage to your company's reputation and the trust you've built with customers.
In fact, the link between having insurance and having a prevention strategy is tighter than ever. Most insurance carriers now require you to have strong security controls in place—like mandatory MFA, endpoint protection, and a formal incident response plan—just to get a policy. If you don't, you'll be looking at higher premiums or might even be denied coverage entirely. Prevention reduces your risk; insurance just helps manage the financial fallout if that risk becomes reality. This is especially true for targeted attacks, which is why we created a complete guide on business email compromise prevention to help you secure your most vulnerable channel.
Ready to secure your communications with an email provider that puts privacy and security first? At Typewire, we offer private email hosting with no ads, no tracking, and zero data mining, all run on our own secure infrastructure. Take control of your data and start your free 7-day trial today at https://typewire.com.

