Sending an email securely isn't just one action—it's a two-part strategy. You need to protect the message while it's traveling and also protect the message's content itself. This means combining Transport Layer Security (TLS) with end-to-end encryption.
Think of it this way: TLS is the armored truck carrying your letter across the internet. It stops anyone from snatching it off the road. But end-to-end encryption is like writing that letter in a secret code that only your friend can decipher. Even if someone hijacks the truck, the letter inside is just gibberish to them.
Your Quick Guide to Secure Email
Getting these two layers right is the foundation of real email privacy. Without both, you're leaving a weak link in the chain.
The image below shows how this works in practice. Before your message even leaves your outbox, it gets scrambled using a public key, making it completely unreadable to anyone except the one person who holds the matching private key.
This process ensures that from the moment you hit "send" to the moment your recipient opens it, the content remains completely private.
Core Components of Secure Email
So, where do you start? Focusing on a few key technologies and habits will give you a rock-solid defense against the most common threats. It's not just about the tools you use; it's about how you use them.
To get started, let’s look at the essential pieces that make up a secure email setup. The table below breaks down the must-have components, what they do, and why they matter.
Core Components for Sending Email Securely
| Component | What It Does | Key Benefit |
|---|---|---|
| TLS/SSL Encryption | Secures the connection between your email client and the server, protecting data in transit. | Prevents eavesdropping as your email travels across the internet. |
| End-to-End Encryption (E2EE) | Encrypts the actual content of your message, making it readable only by the intended recipient. | Protects your message's content even if a server is compromised. |
| Email Client Configuration | Involves setting up tools like PGP/GPG or S/MIME within your email app (e.g., Outlook, Thunderbird). | Gives you direct control over encrypting and signing your messages. |
| User Vigilance | Involves practices like verifying recipient addresses and identifying phishing attempts. | Provides a critical human firewall against social engineering attacks. |
These components work together to create layers of security, making it exponentially harder for anyone to intercept or read your private communications.
To put this into practice, here’s what you need to focus on:
-
Confirm TLS is Active: Dive into your email client’s settings and make sure it’s set to use TLS (often listed as SSL/TLS) for both incoming and outgoing mail servers. This is non-negotiable.
-
Embrace End-to-End Encryption: For anything truly sensitive, you need tools like PGP/GPG or S/MIME. They are the industry standard for locking down the content of your emails so no one but the recipient can ever see it.
-
Build Smart Security Habits: Technology alone isn't enough. Always double-check who you're sending emails to. Be deeply suspicious of unexpected links or attachments. With an estimated 3.4 billion phishing emails sent every single day, your own judgment is one of your best defenses. You can learn more about these phishing statistics at Keepnet Labs.
Combining strong technical tools with sharp, mindful habits is what creates a truly resilient security posture. It's about building a system that's tough for attackers to break at every level.
For a more detailed breakdown, check out our guide on top tips for safe and private messaging.
Why Standard Email Is No Longer Enough
We tend to think of our email inbox as a private space, but that's a dangerous misconception. A standard email isn't a sealed letter; it's much more like a postcard. Anyone from network administrators to malicious actors can potentially read its contents as it travels from sender to receiver. This basic lack of privacy is why sending email securely has become a non-negotiable part of modern life.
The threats we face today are a world away from the clumsy spam of the past. Simple password protection and out-of-the-box filters just don't cut it anymore against attackers who are more motivated and better equipped than ever before.
The Evolving Threat Landscape
Forget generic spam. Today's biggest risks come from highly sophisticated and personalized phishing campaigns. Attackers comb through social media profiles and data breach dumps to craft emails that look incredibly convincing, easily slipping past outdated security filters.
Another persistent danger is the man-in-the-middle attack, especially if you ever use public Wi-Fi. In these situations, an attacker can position themselves between your device and the email server, intercepting and reading everything you send and receive. You wouldn't even know it was happening. These vulnerabilities are precisely why securing your email must be part of a larger comprehensive cybersecurity strategy.
Take a look at this classic example of a phishing attempt. It’s designed to create a sense of urgency, tricking you into giving up your credentials.
The red flags are subtle—a slightly off logo or a strange sender address—but they're often the only warning you'll get.
Recent Phishing Threat Evolution
The data shows a clear and worrying trend. Phishing isn't just growing in volume; it's also becoming much more refined.
| Year Span | Volume Increase | Primary Tactic Shift |
|---|---|---|
| 2019-2020 | 150% Year-over-Year | From generic, mass emails to targeted "spear phishing." |
| 2021-2022 | 61% Increase | Growth in brand impersonation and Business Email Compromise (BEC). |
| 2023-Present | Ongoing | Rise of AI-powered phishing and QR code-based "quishing." |
As the numbers show, attackers are constantly adapting their methods to bypass defenses and exploit human trust.
Why Human Error Is a Major Factor
At the end of the day, even the best technology has its limits. The most common point of failure isn't a firewall; it's a person. A single, momentary lapse in judgment—clicking a bad link, entering a password on a fake site, or even a simple typo in a recipient's email address—can open the door to a massive data breach.
I've seen it happen to even the most security-conscious people. Attackers are masters of social engineering, and one well-timed, convincing email is sometimes all it takes.
Relying on default email settings is like leaving your front door unlocked. Sure, you might be fine for a while, but you're counting on luck. Sooner or later, someone will come along and take advantage of the easy access.
The bottom line is that standard email is inherently vulnerable. If you want to keep your conversations private and your data safe, you have to be proactive. It’s time to move beyond the flimsy protections that come standard and take real steps to secure your communications.
Laying a Secure Foundation with TLS
Before we even get into the weeds of end-to-end encryption, the absolute first step is to secure the connection itself. This is where Transport Layer Security (TLS) comes in.
Think of TLS as the armored truck that carries your email from your server to the recipient's server. Without it, you're essentially sending a postcard that anyone along the route can read. It’s the fundamental layer of protection that everything else builds on.
Most good email providers handle this for you these days, but it’s a mistake to just assume it's working. It’s always worth a quick look in your email client’s settings. You're looking for connection options like "SSL/TLS" or "STARTTLS"—if you see those, you're on the right track.
This visual gives a great overview of the process, but remember, TLS is what protects the entire journey before any content-level security even kicks in.
While the graphic focuses on protecting the message contents, TLS is all about securing the pathway, preventing anyone from snooping while your email is in transit.
Prove You Are Who You Say You Are
Encrypting the connection is one thing, but you also need to prove your emails are actually coming from you. This is where domain authentication protocols team up with TLS to build a truly trustworthy system. They're your best defense against spoofing, where a bad actor fakes an email to look like it came from your address.
There are two key players here:
- Sender Policy Framework (SPF): This is basically a public list of all the mail servers that have permission to send emails for your domain. Think of it as your company's list of official, approved couriers.
- DomainKeys Identified Mail (DKIM): This adds a tamper-proof digital signature to every email you send. The receiving server checks this signature to make sure the message wasn't altered after it left your server.
Getting SPF and DKIM set up correctly signals to the world’s email servers that your messages are the real deal. This doesn't just lock down your security; it also does wonders for your deliverability, helping you stay out of the spam folder.
Without proper domain authentication, even a perfectly encrypted email can be impersonated. It's like sending a sealed letter with no return address—the message inside is secure, but the recipient has no way to verify who really sent it.
Watch Out for These Common TLS Mistakes
Setting up TLS should be pretty straightforward, but a few common slip-ups can completely undermine your security. The one I see most often is an expired or misconfigured SSL/TLS certificate on the mail server. This is what causes those scary security warnings in email clients and can even stop your emails from being sent or received.
Another classic mistake is sticking with old, outdated security protocols. You need to make sure your server is using a modern version, like TLS 1.2 or the even better TLS 1.3. Older versions have well-known security holes that are actively being exploited.
Make it a habit to regularly check your server's configuration and keep an eye on your certificate expiration dates. It’s a small bit of maintenance that pays huge dividends in keeping your email communications safe.
Implementing End-to-End Email Encryption
While TLS is great for securing the connection between mail servers, it doesn't protect the message itself. For true privacy, you need end-to-end encryption (E2EE). This is the gold standard.
Think of it this way: E2EE scrambles your email's content the moment you hit send, and it stays scrambled until your intended recipient unlocks it on their device. No one in between—not your email provider, not your ISP, not a hacker—can read a single word. This is absolutely essential when you're dealing with sensitive information like contracts, financial records, or personal health details.
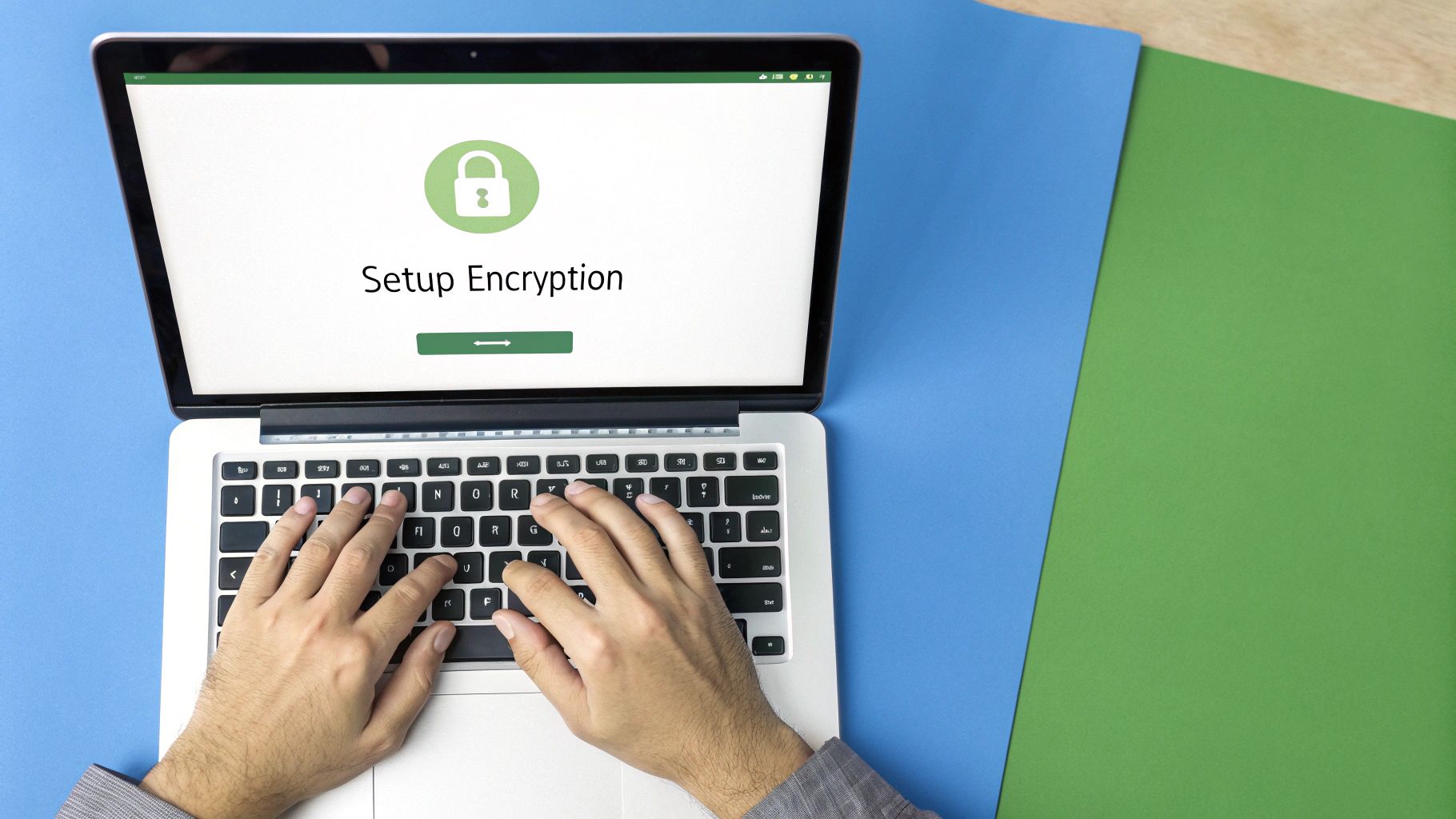
This screenshot shows the interface for Gpg4win, a popular tool for PGP encryption. At its core, E2EE is all about managing cryptographic keys. Your ability to send and receive secure messages hinges on how well you generate, share, and protect these digital keys.
Getting Started with PGP and S/MIME
When you dive into E2EE, you'll immediately run into two big names: Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME). They both get you to the same place—a fully encrypted email—but they take slightly different roads.
- PGP/GPG: This is a decentralized system built on a "web of trust." You create your own public and private keys. You share your public key with anyone who wants to send you a secure message, and you keep your private key under lock and key. It’s flexible and has a ton of support from third-party tools.
- S/MIME: This standard is more centralized. A trusted Certificate Authority (CA) issues and verifies your keys, much like the SSL/TLS certificates that secure websites. This is why you see it a lot in corporate settings, where an IT department can manage certificates for everyone in the company.
For most people just starting out, PGP (or its open-source cousin, GnuPG) is the more practical choice. Tools like Gpg4win for Windows or GPG Suite for Mac plug right into common email clients like Outlook and Apple Mail, making encryption a seamless part of your daily workflow. If you want to get a better handle on the fundamentals, it helps to understand what encryption is and its different types.
The Critical Role of Key Management
I can't stress this enough: your encryption is only as strong as your key management.
Your private key is the one and only key that can decrypt messages sent to you. It must be kept completely secret. If someone gets their hands on it, they can read all of your encrypted correspondence, past and present.
On the other hand, your public key is designed to be shared far and wide. You can put it on your website, include it in your email signature, or upload it to a public keyserver. The easier it is for people to find your public key, the easier it is for them to send you a secure message.
A classic rookie mistake is trusting a public key without verifying it first. Before sending something highly sensitive, confirm your contact's public key through a separate channel you already trust, like a phone call or a face-to-face chat. This simple step can stop a man-in-the-middle attacker dead in their tracks.
Avoiding Common Encryption Pitfalls
Even with the best tools, we humans are often the weakest link. In fact, human error is the root cause of an estimated 95% of all data breaches. It's a sobering statistic.
To keep from becoming part of that number, build these habits into your routine:
- Encrypt and Sign: Don't just encrypt; digitally sign your messages, too. A signature proves the email actually came from you and wasn't tampered with along the way.
- Guard Your Private Key: Protect your private key file with a strong, memorable passphrase. Make backups and store them somewhere safe and offline, like on an encrypted USB drive.
- Mind Your Metadata: Remember, E2EE only scrambles the body of your email. The subject line, sender, and recipient addresses are still visible. Never put sensitive information in the subject line.
Building a Human Firewall to Prevent Breaches
End-to-end encryption is fantastic for sending emails securely, but it's completely powerless against a clever phishing attack or a simple typo in a recipient’s address. The hard truth is that the biggest vulnerability in any security system is often the person sitting at the keyboard. This is why building strong security habits is every bit as important as picking the right software.
Think of it as creating a “human firewall”—your active, thinking defense against threats that automated systems can easily miss. It’s all about fostering a healthy sense of skepticism and creating deliberate routines for handling sensitive information. After all, attackers are masters at exploiting human trust and a false sense of urgency.
Even the pros get caught off guard. When noted security researcher Troy Hunt had his Mailchimp account compromised, he pointed out how exhaustion and a perfectly crafted, urgent-but-not-panicky email created the ideal conditions for a mistake. It’s a powerful reminder that anyone can be vulnerable in a moment of weakness.
Creating Simple, Effective Security Habits
You don’t need a complicated rulebook to make a massive difference. The real goal is to turn mindful actions into automatic behaviors. You can start by weaving a few straightforward practices into your daily workflow.
-
Verify Recipient Addresses: Always, always double-check the "To:" field before hitting send on an email containing sensitive files. A simple typo could accidentally send your company's confidential data to a complete stranger.
-
Scrutinize Attachments and Links: If you weren't expecting an attachment or a link, don't open it. This holds true even if it seems to come from a trusted colleague or a known contact. A quick text or phone call to verify is all it takes.
-
Establish a "Four-Eyes" Rule: For really critical communications—think wiring instructions, legal documents, or major company announcements—have a second person review the email before it goes out. This simple check can catch mistakes before they snowball into disasters.
These habits aren’t just about following rules; they reinforce a security-first mindset, which is the bedrock of any modern defense strategy. If you want to explore this concept further, you can learn more about what zero-trust security is and why it matters in our detailed guide.
Technology provides the lock, but people hold the key. A strong human firewall relies on vigilance, process, and the understanding that security is a shared responsibility, not just an IT problem.
By integrating these small behavioral changes into your routine, you create a powerful and surprisingly resilient layer of defense. This human element is the essential partner to your technical security measures, working together to ensure your private communications stay that way.
Troubleshooting Your Secure Email Setup
Even the best-laid plans for a secure email system can hit a bump in the road. When you're juggling encryption, certificates, and different servers, even a tiny misstep can create a major headache. The real trick is knowing where to start looking when things go wrong so you can keep your communications locked down.

Instead of jumping into panic mode, it pays to be methodical. I always start with the most common culprits because, frankly, they're responsible for most of the problems you'll see. A little focused diagnostic work now can save you from a complete communication meltdown later on.
Diagnosing TLS Connection Failures
One of the most common issues I run into is a failed Transport Layer Security (TLS) connection. You'll usually see this as an error in your email client complaining it can't securely connect to the mail server. Before you start digging into complex network tools, just check the basics first.
More often than not, the problem is a simple settings mismatch right in your email client.
Here’s my go-to checklist:
- Server Ports: Are you absolutely sure you're using the right port numbers? For sending mail (SMTP), that’s almost always 587 (with STARTTLS) or 465 (for SSL/TLS). For receiving (IMAP), it should be 993 (SSL/TLS).
- Encryption Method: Double-check that your client is explicitly set to use SSL/TLS or STARTTLS, not "None." You'd be surprised how often this gets switched off by accident during an update or initial setup.
- Certificate Validity: Is the server's SSL/TLS certificate still good? An expired certificate is a classic reason for email clients to flat-out refuse a connection. If you're using a major provider, they handle this, but for self-hosted folks, this is a critical point to verify.
What to Do with Encryption Key Problems
When you're dealing with end-to-end encryption like PGP, the problems almost always come down to key management. For example, you send an encrypted message, and your recipient replies saying they can't open it. This is a tell-tale sign of a key mismatch. It means you almost certainly used the wrong public key to encrypt that email.
In my experience, the number one PGP error is using an old or incorrect public key for your contact. People update their keys, so you have to make sure your keychain is current.
To fix this, you need to get their latest public key from a source you trust, like their website or a public keyserver. Once you have it, delete their old key from your local keychain and import the new one. This one simple action solves the vast majority of "can't decrypt" errors and really drives home the importance of keeping your keys in order.
Got Questions About Secure Email? We've Got Answers
Diving into the world of secure email often brings up some practical questions. It's easy to get tangled in the terminology, so let's clear up a few of the most common points of confusion I see.
Can I Send a Secure Email to Someone Who Doesn't Use Encryption?
This is a great question, and the answer is a classic "yes, but…"
You can always protect your email on its journey using TLS, which is a huge step in the right direction. It encrypts the connection between servers. However, for true end-to-end encryption (like PGP), both you and your recipient need to be on board with the right tools installed and configured.
If your contact isn't set up for it, the message will land on their server unencrypted, leaving it exposed. For anything truly sensitive, you’re better off helping them get set up or finding another secure way to communicate.
Is a Secure Email Provider Enough on Its Own?
Switching to one of the top 7 best email providers for privacy in 2025 is a fantastic move. These services make privacy easy by handling the technical side of encryption for you.
The catch? This automatic, seamless encryption usually only works when you're emailing someone else on the same service.
If you send a message from your private provider to a friend on Gmail, it will probably travel unencrypted unless you've manually set up PGP. Think of these providers as a strong foundation for your security, not a magic bullet that removes the need for good habits.
Here's an analogy I like to use: TLS is like putting your letter in a locked mailbag for the mail truck. It protects the message while it's in transit. PGP, on the other hand, is like writing the letter itself in a secret code. Even if someone intercepts the mailbag, they can't read the letter. For the best security, you really want both.
Ready to take full control of your inbox? Typewire offers private, secure email hosting without ads, tracking, or data mining. Start your 7-day free trial and experience true email privacy today at https://typewire.com.

