When you’re looking for the most secure email account, it really comes down to a few core principles: end-to-end encryption, a zero-knowledge framework, and a rock-solid legal foundation. This is why providers like Proton Mail and Tutanota often top the list. They’re built from the ground up to ensure no one—not even the company itself—can peek at your messages.
What Defines a Truly Secure Email Account?

Real email security is so much more than just a complex password. It’s a complete ecosystem built to defend your private conversations from every possible angle. Think of it like a medieval fortress protecting treasure. You wouldn't just lock the front gate and call it a day, right? You’d want high walls, a moat, and loyal guards who can’t be bribed.
In the email world, this means cutting through the marketing fluff and looking at the actual technology and policies that protect you. The most secure email accounts are built on a handful of key pillars that work in concert to create a formidable defense for your digital life.
The Pillars of Email Security
A genuinely secure email service isn't defined by fancy features but by a commitment to user confidentiality and control. These aren't just tech buzzwords; they're the foundational elements that separate a truly private inbox from one that leaves you vulnerable.
Here are the non-negotiables you should demand from any provider claiming to be secure:
- End-to-End Encryption (E2EE): This is the gold standard. It scrambles your message the instant you hit "send" and only unscrambles it once your recipient opens it with their unique key. Simply put, only you and the person you’re writing to can ever read the contents.
- Zero-Knowledge Architecture: This takes security a step further. It means the email provider cannot access your data, period. Because your encryption keys are stored on your device, it's technically impossible for the company to decrypt your messages—even if a court ordered them to. To dig deeper, you can learn what zero trust security is and why it matters for modern data protection.
- Privacy-Focused Legal Jurisdiction: Where your email provider is based matters immensely. Countries like Switzerland have some of the world's strictest privacy laws, creating a powerful legal shield that protects your data from government snooping and overreach.
- Open-Source Code: This is all about transparency. When a provider makes their code open-source, it allows independent security experts worldwide to poke, prod, and audit it for any weaknesses. This builds trust and verifies that the service is actually as secure as it claims to be.
To help you remember what to look for, we've put together a quick summary of these essential features.
Key Features of a Secure Email Account
A summary of the essential security features to look for in an email provider and why each is important for protecting your privacy.
| Security Feature | What It Means for You | Why It's Essential |
|---|---|---|
| End-to-End Encryption | Only you and the recipient can read your emails. | Prevents anyone in the middle—hackers, ISPs, or the provider—from intercepting and reading your messages. |
| Zero-Knowledge Architecture | The provider cannot access or decrypt your emails, ever. | Ensures your data remains private even if the company's servers are compromised or legally subpoenaed. |
| Privacy-First Jurisdiction | Your data is protected by strong, user-centric privacy laws. | Acts as a legal firewall against government surveillance requests from less privacy-friendly nations. |
| Open-Source Code | The service's security claims can be independently verified. | Builds trust through transparency, ensuring there are no hidden backdoors or vulnerabilities in the code. |
Ultimately, these pillars work together to form a comprehensive security strategy. Lacking even one can leave a significant gap in your digital defenses.
Understanding the Foundations of Email Security

Before you can pick the most secure email account, you need to know what you're looking for. It’s a bit like building a fortress to protect your messages—each piece has a specific job, and they all have to work together perfectly to keep things truly private.
These aren't just buzzwords. They’re the core principles that separate an email service that respects your privacy from one that just rents you a mailbox. Once you get a handle on these concepts, you'll be able to cut through the marketing fluff and judge any provider with a critical eye.
End-to-End Encryption: The Unbreakable Seal
The absolute cornerstone of any secure email is end-to-end encryption (E2EE). Think of it like this: you write a letter, but instead of a normal envelope, you put it in a high-tech case that instantly locks itself. Only the person you're sending it to has the unique key to open it. No one else—not the mail carrier, not the people at the post office, not even a determined spy—can peek inside.
That’s E2EE in a nutshell. The moment you hit "send," your message is scrambled into unreadable nonsense on your device. It only gets unscrambled back into a readable email when your recipient opens it on their end. This ensures the contents of your conversation stay completely hidden for the entire trip.
Without end-to-end encryption, any message you send can potentially be read by your provider, advertisers, or government agencies. It is the non-negotiable foundation of any claim to be the most secure email account.
The best services make this happen automatically behind the scenes. You don't need a technical degree to use it. It simply transforms your inbox from an open postcard that anyone can read into a private, locked diary.
Zero-Knowledge Architecture: The Vault Keeper with No Key
While E2EE protects your emails as they travel, zero-knowledge architecture protects them once they arrive on the provider's servers. Imagine you're storing valuables in a bank vault, but you're the only person in the world with the combination. The bank manager doesn't have a spare key and has no way to open it, even if they wanted to.
A provider with a zero-knowledge system is built so they literally cannot decrypt your data. Ever. Your encryption keys are stored only on your devices. This means that even if a court ordered them to hand over your emails, all they could provide is a jumbled mess of encrypted code.
This approach makes a powerful statement about who owns your data. It proves the provider is just a guardian for your encrypted information, not its owner. Building systems this secure often requires the specialized knowledge of cybersecurity professionals who understand how to create truly private architecture.
Essential Layers of Defense
Beyond encryption, a few other features are critical for locking down your account. Think of them as extra reinforcements for your digital fortress.
- Two-Factor Authentication (2FA): This is like adding a second, completely different lock to your main gate. Even if a thief steals your password (the first key), they can't get inside without that second piece—usually a code sent to your phone or a physical security key.
- Metadata Protection: Metadata is the information about your email, like who you sent it to, the subject line, and when you sent it. While many services encrypt the email itself, the most secure ones also work to hide or scramble this metadata, preventing prying eyes from seeing the patterns of your communication.
When you put it all together, you have a formidable defense. A strong password protects your login, 2FA stops password thieves cold, E2EE secures your conversations, and a zero-knowledge policy ensures even the provider can't compromise your trust.
Why Encryption and Privacy Laws Must Work Together

Powerful encryption is a fantastic shield for your data, but it’s really only half the story. The best technology on earth can be completely undermined by weak or invasive laws. This is precisely why the physical location of your email provider’s servers and headquarters is one of the most critical factors in figuring out what is the most secure email account for you.
Think of it like building a bank vault. You can install the thickest, most advanced steel door imaginable (that’s your encryption), but if the vault is located in a town where the sheriff can demand the keys at any time, that door doesn't mean much. Your digital security works the exact same way. Strong tech needs to be backed up by strong legal protections.
A provider’s legal jurisdiction is essentially its "legal firewall," and it dictates how much access governments and law enforcement have to your private data. This is where the world divides, sharply.
The Power of Privacy-First Jurisdictions
Some countries, like Switzerland and Germany, have built their entire reputation on robust, citizen-first privacy laws. These legal frameworks are specifically designed to protect individual data rights, making it incredibly difficult for anyone to get unauthorized access to your information. They act as a powerful buffer against wide-reaching surveillance programs.
On the flip side, other countries have laws that can force companies to hand over user data or even create "backdoors" into their encrypted systems. A provider based in a place like that may be legally obligated to compromise your privacy, no matter how good its technology is.
This is why a provider’s choice of home base isn't an accident—it's a clear statement about its commitment to you. Take Proton Mail, for example. Launched in 2014 and based in Switzerland, it’s a top-tier secure email provider largely because of its strategic location. Switzerland’s tough privacy laws, like the Swiss Federal Data Protection Act, complement its end-to-end encryption perfectly, giving users a powerful, two-layered defense.
Choosing an email provider is like choosing a digital country for your data to live in. Pick a nation with laws that respect your right to privacy, and you give your data the strongest legal protection possible.
How Legal Frameworks Shape Your Security
The impact of these laws is very real and practical. They determine the exact process and legal standard required for a company to even consider releasing user data.
- Switzerland: Famous for its neutrality and strict data privacy, Swiss law simply doesn't recognize foreign court orders. Any request for data has to go through the Swiss legal system and meet a very high bar for evidence.
- Germany: As an EU member, Germany is governed by the General Data Protection Regulation (GDPR), one of the most comprehensive data protection laws in the world. It gives users a huge amount of control over their personal information.
To see how these rules play out in the real world, you can look at how different online services handle their obligations. For instance, a cryptocurrency trading platform spells out its data and user protection commitments in their detailed Privacy Policy, which directly reflects the legal framework it operates under.
When technology and law work together, your security is amplified. End-to-end encryption protects your data from hackers, while a strong legal jurisdiction shields it from legal overreach. This combination is the true hallmark of a genuinely secure email service.
Comparing the Most Secure Email Providers
Now that we’ve covered the essentials of encryption and why server location matters, let's put it all into practice. It’s time to see how the top secure email providers actually stack up against each other.
Each service brings something unique to the table, mixing security, privacy, and ease of use in different ways. Pinpointing their individual strengths is the key to finding the right fit for you, whether you're an individual who values privacy above all else or a business that can't afford to compromise on security.
We'll look at three of the biggest names in the space: Proton Mail, Tutanota, and Zoho Mail. Each has carved out a loyal following for good reason, and together they give us a great picture of what truly private communication looks like.
Proton Mail: The Swiss Standard for Usability
Proton Mail has practically become the poster child for secure email. Why? It brilliantly combines the legal muscle of its Swiss jurisdiction with an interface that anyone can use. Being based in Geneva, Switzerland, means it’s protected by some of the strongest privacy laws on the planet—a huge legal advantage right from the start.
But its real genius is in making high-level security feel effortless. End-to-end encryption is automatic when you email other Proton users, and its zero-access architecture means not even Proton's own employees can peek at your messages. This makes it a fantastic choice for anyone who wants maximum security without having to read a technical manual first.
This chart gives you a quick visual comparison of how leading secure email providers rate in terms of their encryption strength.
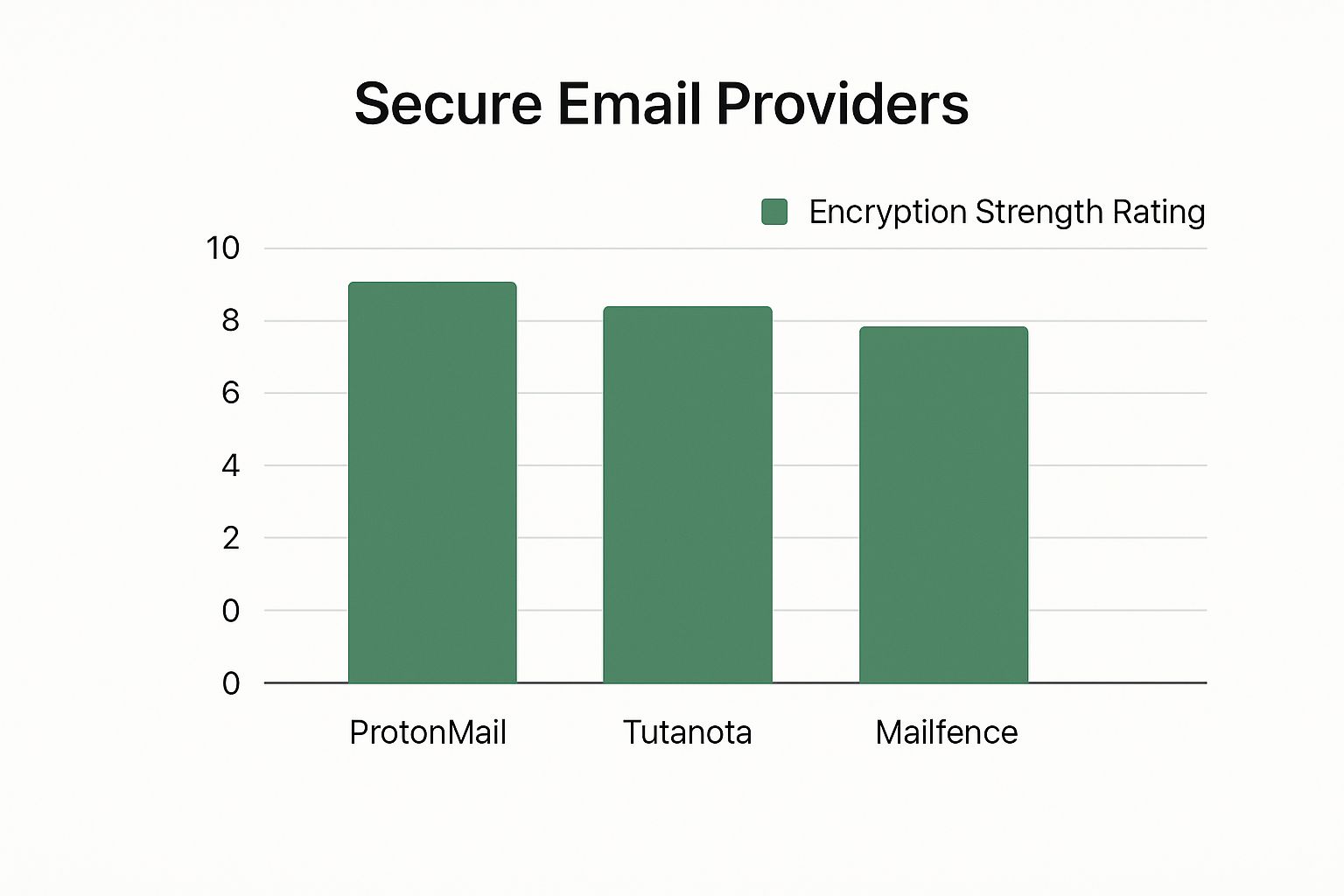
As you can see, while they all offer solid encryption, the subtle differences in their overall security design are what set them apart.
Tutanota: The German Fortress of Privacy
Tutanota, founded in Germany back in 2011, takes a slightly more hardcore approach to encryption. It gets the benefit of Europe's strict GDPR laws, but what really makes it stand out is its obsession with encrypting everything. We're not just talking about the email body; Tutanota encrypts subject lines, your contacts, and even your calendar.
Another huge plus is that the entire platform is open-source. This means security experts from anywhere in the world can comb through the code, looking for flaws and keeping the company honest. This radical transparency builds a ton of trust and makes Tutanota a go-to for users who demand the highest level of technical privacy.
Tutanota's decision to encrypt metadata like subject lines is a significant privacy advantage. It prevents outsiders from inferring the context of your conversations, even if they can't read the message content itself.
This meticulous security is perfect for journalists, activists, or anyone whose communications are so sensitive that even the topic of a conversation needs to be hidden. If you want to dive deeper, you can see how Tutanota and others compare in our complete guide to the top 7 best email providers for privacy in 2025.
Zoho Mail: Security for the Business World
While Proton Mail and Tutanota are laser-focused on individual privacy, Zoho Mail targets businesses that need to blend security with a full suite of productivity tools. It's not just an email service; it’s part of a massive ecosystem that includes a CRM, project management software, and document editors that all work together.
Don't think that makes its security an afterthought, though. Zoho Mail is packed with features designed for a corporate environment:
- S/MIME Encryption: It uses this strong industry standard to keep messages secure both on their servers and while they’re in transit.
- Advanced Policy Controls: Admins can get really granular, forcing things like two-factor authentication or restricting access based on location.
- Data Center Security: Zoho owns and operates its own data centers, meaning it has complete control over physical and network security—a huge comfort for any business.
This all-in-one approach makes Zoho Mail a fantastic option for companies that need a secure, compliant, and powerful email platform without juggling a dozen different services.
Secure Email Provider Feature Comparison
To make things even clearer, here’s a head-to-head breakdown of how these three services compare on the features that matter most.
| Feature | Proton Mail | Tutanota | Zoho Mail |
|---|---|---|---|
| End-to-End Encryption | Yes (OpenPGP) | Yes (AES & RSA) | Yes (S/MIME) |
| Zero-Knowledge | Yes (for emails) | Yes (for emails, contacts, calendar) | No (admin access possible) |
| Jurisdiction | Switzerland | Germany | India/USA |
| Open-Source | Yes (web, mobile, Bridge) | Yes (all clients) | No |
| Metadata Encryption | No (subject lines are not E2EE) | Yes (subject lines are encrypted) | No |
| Business-Focused Tools | Yes (Proton for Business) | Yes (with custom domains) | Yes (fully integrated suite) |
This table highlights the core trade-offs. Tutanota offers the most comprehensive encryption, Proton Mail provides a great balance of security and usability with strong legal protections, and Zoho Mail is the clear winner for businesses needing an integrated productivity suite. Ultimately, the "best" choice really depends on what you value most.
Finding the Balance: Can You Have Strong Security and Business Productivity?
Lots of businesses hesitate to switch to a super-secure email service, and for good reason. They worry it’ll throw a wrench in their team's workflow. After all, what good is the most locked-down email account on the planet if it’s clunky, slows everyone down, or won’t play nice with the tools you rely on every day? This is the classic tug-of-war: airtight security versus real-world business needs.
But here’s the good news: you don’t have to pick a side. Some providers have figured out how to close that gap. They’ve built powerful security features into platforms designed from the ground up for professional teams. They get that a business needs a lot more than just an encrypted inbox—it needs integrated calendars, shared contacts, and custom domain support to actually get work done.
Hitting the Sweet Spot for Your Team
The trick is to find a service that doesn't just bolt on security as an afterthought. You want a platform where security is part of its DNA. A great example is Zoho Mail. It started life as a full-blown business productivity suite and has since become a go-to for companies that need serious security baked right into their tools.
While Zoho is headquartered in India, which has its own evolving privacy laws, they lean heavily on strong technical safeguards to keep user data protected. They use the industry-standard S/MIME protocol for end-to-end encryption, encrypt all your data when it's sitting on their servers (at rest) and while it's flying across the internet (in transit), and offer two-factor authentication (2FA) to lock down logins. You can see a deeper dive into how Zoho Mail merges security with business functionality over at CyberInsider.com.
For any business, productivity and security aren't opposing forces—they're two sides of the same coin. A security breach is the ultimate productivity killer, which makes a secure-by-design platform one of the smartest investments you can make.
With this kind of integrated approach, your team can schedule meetings, manage client contacts, and collaborate without ever having to second-guess if their communications are protected. It just works.
The Non-Negotiables for Secure Business Email
When you're vetting a new email provider for your company, you need to look for that perfect blend of security muscle and practical, everyday tools.
Here’s what should be on your checklist:
- Custom Domain Support: Using your own domain (
you@yourcompany.com) is absolutely essential. It’s about branding, trust, and professionalism. - An Integrated Suite: Does it come with a calendar, contact manager, and task lists that are built to work together, not fight each other?
- Admin Controls: You need a powerful admin dashboard. This lets you set company-wide security rules, manage who has access to what, and keep your organization compliant.
- Rock-Solid Authentication: Passwords aren't enough anymore. Insist on a service that offers strong multi-factor authentication to prevent account takeovers.
The end goal is simple: find a platform where security makes your team more productive, not less. By choosing a provider that weaves these elements together, you’re not just getting a secure inbox; you’re building a digital workspace that’s efficient, resilient, and fundamentally safe.
How to Choose the Right Secure Email for You
Picking the right secure email service isn't about finding a single "best" provider for everyone. It's about finding the best fit for you.
Before you start comparing features, circle back to the core principles we’ve covered. A truly secure email starts with end-to-end encryption, a strict zero-knowledge policy, and a home base in a country with serious privacy laws, like Switzerland or Germany. These are the non-negotiables.
With those fundamentals in mind, the real question becomes: what do you actually need your email to do? Your answer is what will ultimately point you to the perfect provider.
Match Your Needs to the Right Provider
Think about which of these descriptions sounds most like you:
-
The Privacy Advocate: Are you mainly trying to escape the constant data harvesting of Big Tech and reclaim your inbox from targeted ads? A service like Proton Mail is a fantastic starting point. It strikes a great balance between top-tier legal protection and a clean, easy-to-use interface.
-
The High-Risk User: If you're a journalist, activist, or anyone whose communications are extremely sensitive, you need an extra layer of defense. Tutanota is built for this, encrypting metadata like subject lines, which most others don't. That’s a critical advantage when confidentiality is paramount.
-
The Secure Business: Do you need more than just a locked-down inbox? If you're looking for productivity tools like calendars, cloud storage, and support for your own custom domain, a business-focused suite from Zoho Mail or Typewire is the way to go.
By lining up a provider's strengths with what you do every day, you can choose a service with confidence. This ensures your inbox isn't just secure, but also practical for your life—especially if you're ready to learn how to stop email ads for good.
A Few Common Questions About Secure Email
Diving into the world of secure email can bring up a few questions. Let's tackle some of the most common ones to clear things up.
Are Paid Email Accounts Really More Secure Than Free Ones?
In most cases, yes. While free plans from secure providers are a great way to get started, they usually come with limits on storage or features. More importantly, paying for an email account fundamentally changes your relationship with the provider.
When you pay for an email service, you become the customer, not the product. This simple shift means the company's success depends on protecting your privacy, not selling your data to advertisers.
Can I Actually Send a Secure Email to Someone on Gmail?
You absolutely can. Most secure email services have a clever way to handle this. For example, providers like Proton Mail let you send an encrypted, password-protected message to any email address.
Your recipient simply gets a link. When they click it and enter the password you've shared with them, they can view the message in a secure web portal. The email's contents remain private and never touch Google's servers unencrypted.
Do I Need to Be a Tech Whiz to Use This Stuff?
Not at all. The best secure email platforms are built to be just as easy to use as the big-name services you're used to.
If you're emailing someone who uses the same provider, the encryption is completely automatic—you don't have to do a thing. The entire experience, from setup to sending your first message, feels familiar and intuitive.
Ready to take back control of your inbox with an email service that truly respects your privacy? Typewire gives you end-to-end encryption, zero tracking, and powerful anti-spam filters, all running on our private Canadian servers. Start your 7-day free trial today and feel the difference.

