When you hear "most secure email," don't think of a single brand. Think of a philosophy built on one simple rule: only you and your recipient should ever read your messages. This level of email security and privacy is primarily achieved through hosted email platforms designed specifically for this purpose.
It’s all about end-to-end encryption. This technology transforms your email from a readable postcard that anyone can glance at into a sealed, tamper-proof letter that only the intended person can open.
Decoding True Email Security and Privacy
Searching for the most secure email service means you're looking for a hosted email platform that puts your privacy and security first, period. Standard free email services often see your data as a product to be scanned and monetized. In sharp contrast, truly secure platforms are built from the ground up to shield your communications from everyone—including their own employees.
This isn't just a minor feature; it's a fundamental shift in how email works. Email privacy becomes the default, not an optional add-on you have to hunt for in the settings.
Top-tier providers like Proton Mail and Tutanota are great examples of this in action. They’re based in countries like Switzerland and Germany, which have some of the world's strongest privacy laws. This gives you a legal shield that you just don't get elsewhere. Their entire business model is based on the radical idea that your emails belong to you and you alone.
What Makes an Email Genuinely Secure?
So, what are the non-negotiable ingredients for a truly secure email service? It really comes down to a handful of core commitments—both in technology and in ethics—that work together to ensure your email privacy and security.
These are the absolute essentials you should look for in a hosted email platform:
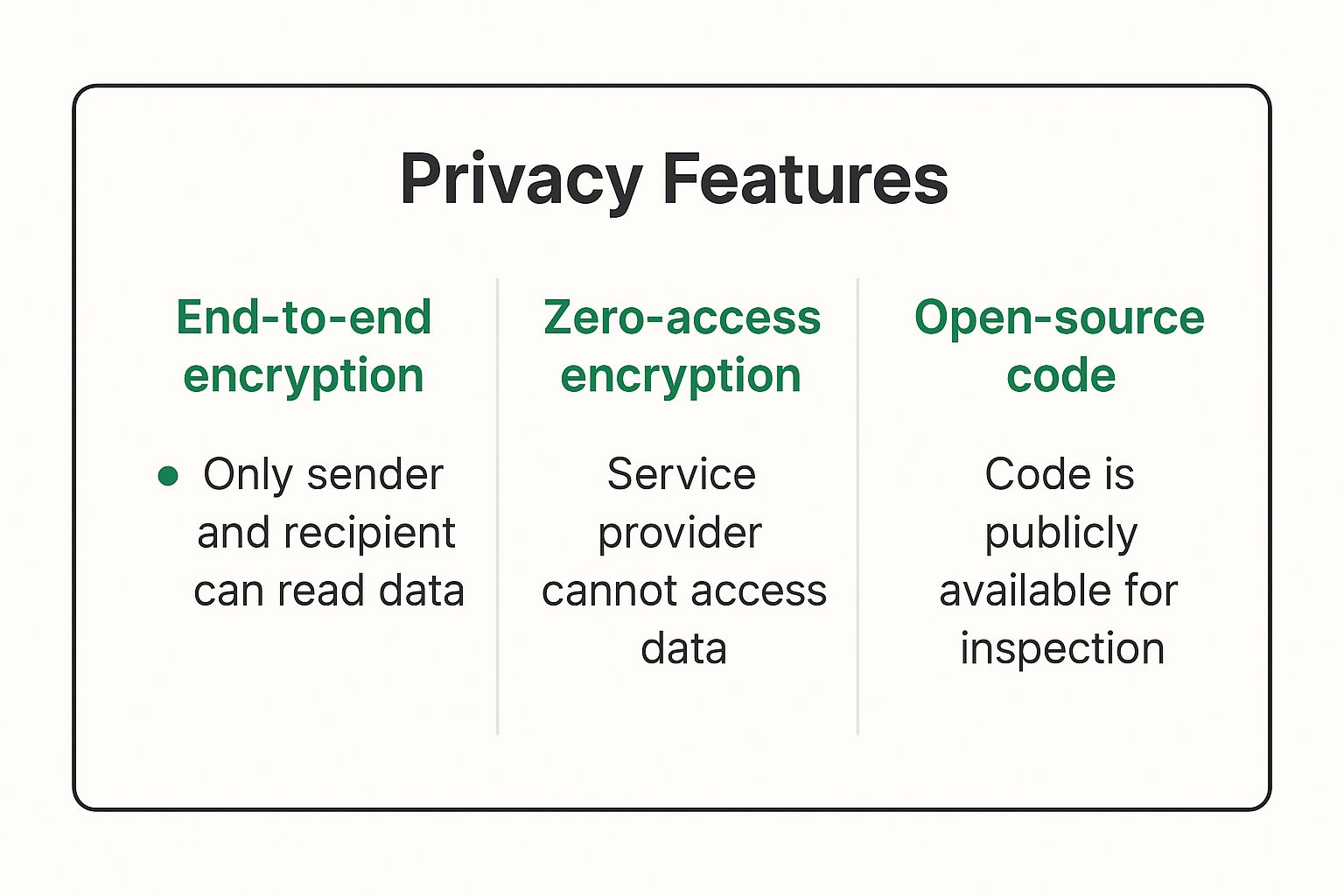
- End-to-End Encryption (E2EE): This is the crown jewel of email security. Your message is scrambled on your device and can only be unscrambled by your recipient. No one in the middle, not even your provider, can read it.
- Zero-Access Architecture: This fancy term means the provider designs their system so they physically can't access your stored emails. Your data is encrypted on their servers, and they don't have the key. You do.
- Privacy-First Jurisdiction: Where a company is legally based makes a huge difference for email privacy. Being headquartered in a country with robust privacy laws adds a powerful layer of protection against overreaching government data requests.
- Minimal Metadata Collection: It's not just about the content of your emails. Secure services also collect as little information as possible about who you're emailing and when, leaving a much smaller digital footprint.
These four pillars are what separate genuine privacy from mere security theater. To dig a little deeper into these concepts, check out our guide on what is a secure email and why is it crucial for your privacy.
To make this crystal clear, let's break down how these features compare to a standard, free email account.
Key Features of a Secure Email Service at a Glance
This table offers a quick snapshot of the critical differences between a standard inbox and one built for privacy.
| Security Feature | What It Means for Your Privacy | Found in Standard Email? | Found in Secure Email? |
|---|---|---|---|
| End-to-End Encryption | Only you and the recipient can read the email's content. | No (Typically not by default) | Yes (Core feature) |
| Zero-Access Architecture | The email provider cannot access or read your stored messages. | No | Yes |
| Anonymous Sign-up | You can create an account without providing personal information. | No | Often Yes |
| Minimal Metadata Logging | Reduces the digital trail of your communication habits. | No | Yes |
As you can see, the differences are stark. A secure email provider isn't just offering a service; it's making a promise to protect your right to a private conversation.
How Real Email Encryption Actually Works
If you want to find the most secure email, you have to look past the marketing slogans and get a handle on the technology that actually keeps your messages private. It all comes down to encryption, but here’s the thing: not all encryption is the same. There's a world of difference between what standard email services offer and what truly secure hosted email platforms provide.
The most common form of protection you'll see is Transport Layer Security (TLS). Think of it like an armored truck. Your email is the package inside, and the truck protects it while it's on the road between you and your provider. The problem? The delivery company—your email provider—has the keys to the truck and the package. They can open it anytime they want. This fundamentally undermines email privacy.
This is exactly how services like Gmail work. Your email is encrypted while in transit, but once it arrives on their servers, they can and do scan its contents. They look for keywords for advertising, gather data, and who knows what else. It’s a form of email security, but it’s certainly not privacy.
The Gold Standard: End-to-End Encryption
This is where end-to-end encryption (E2EE) completely changes the game for email security. Let's go back to our armored truck analogy. With E2EE, you first lock your message in a personal safe, and only you and your recipient have the key. Then, you put that locked safe inside the armored truck for delivery.
Now, even if the email provider opens up the truck, all they find is an impenetrable box. They have no way of seeing what's inside. Your message gets scrambled on your device before it ever leaves, and it can only be unscrambled on your recipient's device.
With E2EE, your email provider goes from being a potential eavesdropper to being a simple, blind courier. They can move the message from point A to point B, but they can never read it. This is the bedrock of any genuinely secure email service.
This infographic gives a great visual of how modern email security standards come together.

You can see how dedicated hardware, like a security key, works with complex encryption code to build a rock-solid defense for your private communications.
What Is Zero-Access Architecture?
To really make end-to-end encryption stick, the best secure hosted email platforms are built on what's called zero-access architecture. It's a design philosophy with a simple, powerful promise: not even the provider can get into your stored emails, guaranteeing your email privacy.
Here’s a quick rundown of how it works:
- Client-Side Encryption: Everything—your emails, contacts, calendar—is encrypted right on your device, using a key derived from your password.
- Encrypted Storage: This scrambled, unreadable data is then sent to the provider's servers for storage. Since they never see your password, they have absolutely no way to decrypt the information they're holding.
- User-Controlled Decryption: When you log in, that scrambled data is sent back to your device, where your password unlocks it locally for you to read.
This architecture means your privacy isn't just based on a company's policy or a pinky promise; it's guaranteed by math. The provider literally cannot hand over your readable data to anyone, because they don't have it. It’s a model that puts control back where it belongs: with you. For a deeper dive, check out our guide that explains what end-to-end encryption is in simple terms.
Getting these concepts is the key to finding the most secure email. It helps you cut through the noise and ask the right questions. Does a service use E2EE by default? Is it built on a zero-access architecture? These are the technical details that separate true privacy from a mere illusion of it.
The Hidden Privacy Costs of Free Email Services
Ever wonder why some of the most powerful and feature-rich email platforms on the planet are completely free? There's an old saying in tech that rings truer than ever: "If you're not paying for the product, you are the product." This simple truth is why the search for the most secure email has become so critical for anyone who values their privacy.

When you create an account with a "free" service, you're not really a customer. You're a data point. These companies generate massive revenue by systematically analyzing everything in your inbox, from personal chats to purchase receipts. It's a straightforward transaction: you get a free email address, and they get to mine your life for data. This isn't some hidden conspiracy; it's right there in the terms of service most of us click past. This model is the opposite of a secure, hosted email platform focused on user privacy.
This constant scanning allows them to build incredibly detailed profiles on you—what you buy, where you travel, who you talk to. Your private messages are the raw material for their real business: selling hyper-targeted advertising.
You Are The Product
The entire business model is built on monetizing your information, which directly compromises your email privacy. Every single email you send or receive is another piece of the puzzle that helps these companies predict what you’ll buy next.
But this data collection is about more than just showing you ads. Your conversations are fed into their AI models to make them smarter, used to train their voice assistants, and leveraged to refine their algorithms. In short, your private life is a free resource they use to build more profitable technology.
The fundamental trade-off with free email is accepting constant, automated surveillance. Your inbox isn't a private space; it's a data mine.
This creates a massive conflict of interest. A company that makes money by reading your data has zero incentive to offer you genuine, zero-access privacy. Their financial model depends on being able to see what's inside.
The Vulnerabilities of the "Free" Model
Beyond the built-in privacy invasion, this centralized approach creates huge email security risks. When your emails are stored in a readable format on a provider's servers, they become a honeypot for hackers and a convenient target for government agencies.
This system has three glaring vulnerabilities:
- Data Breaches: Giant servers holding the unencrypted emails of billions of people are an irresistible target. A single breach can expose a staggering amount of sensitive personal and financial information.
- Government Data Requests: Email providers are often legally required to hand over user data to law enforcement. Since they hold the keys to your inbox, they can comply with these requests, often without you ever knowing.
- Lack of User Control: At the end of the day, it's not your data—you're just renting space on their servers. The provider can change its privacy policy at will, lock you out, or even shut down, leaving you with no control.
The growing awareness of these issues is fueling the shift toward secure email. In just the first half of 2022, there were over 1,200 reported data breaches, a huge number of which involved email accounts. This is precisely why hosted email platforms offering end-to-end encryption are becoming essential, not just for privacy, but for meeting compliance standards like GDPR and HIPAA. To see how different services stack up, you can explore detailed comparisons of top encrypted email providers for 2025.
Understanding these hidden costs is the first step toward reclaiming your digital privacy. The convenience of "free" comes at a steep price, paid with your most personal information. Choosing a secure email provider isn't just about better tech; it's about choosing a business model that actually respects you and your data.
Comparing the Top Secure Email Providers
Now that we've broken down what truly makes an email service secure, let's see how the leading hosted email platforms put those principles into practice. The search for the most secure email usually narrows down to a few key players who have staked their entire reputation on protecting user data.
Think of them as the practical application of everything we've just discussed—turning complex ideas like end-to-end encryption into tools anyone can use.

This isn't just about listing features. It's about connecting the dots between their design choices—from legal jurisdiction to encryption architecture—and how they solve the email privacy and security problems baked into mainstream email. We'll see how these services stack up against each other and, more importantly, against the free services most of us use every day.
Proton Mail: The Swiss Standard Bearer
You can’t really talk about secure email without mentioning Proton Mail. It has become the benchmark for private communication, proving that a service can be incredibly secure without being impossible to use. Its biggest strengths are a direct reflection of the email security and privacy pillars we’ve covered.
Founded by CERN scientists in 2013, Proton Mail is headquartered in Switzerland, a country famous for its iron-clad privacy laws. It’s built on a foundation of end-to-end encryption and a zero-access architecture, meaning not even they can read your emails. Features like self-destructing messages give you even more control.
With over 25 million users, Proton Mail has clearly struck a chord. Their free plan is a great starting point, offering 1 GB of storage and up to 150 messages daily. For heavier users, paid plans unlock more features and capacity, making it a go-to for both individuals and businesses. These aren’t just marketing bullet points; they represent a fundamental promise that you are the customer, not the product.
Tutanota: The Open-Source Alternative
Another major contender is Tutanota (now Tuta). Based in Germany—another country with strong data protection laws—Tutanota takes a slightly different path to encryption that comes with its own unique advantages.
While Proton Mail uses the widely adopted OpenPGP standard, Tutanota developed its own encryption protocol. This might sound like a minor detail, but it allows them to encrypt more of your data for enhanced email privacy.
Here’s what sets Tutanota apart:
- Complete Encryption: Their custom standard encrypts the entire mailbox, including subject lines—something OpenPGP doesn't do. It's a more comprehensive privacy shield.
- Open-Source Commitment: Tutanota’s apps are completely open-source. This transparency allows security experts and the community to independently verify their code.
- Budget-Friendly: The service is known for its competitive pricing, putting top-tier privacy within reach for more people.
The trade-off? Its custom encryption isn’t directly compatible with other PGP-based services. However, it delivers a perfectly seamless, fully encrypted experience for anyone communicating within the Tuta ecosystem. For a deeper dive, check out our complete list of the 12 best secure email providers for privacy in 2025.
Secure Email Provider Feature Comparison
To really see the difference, let’s put these hosted email platforms side-by-side with a standard free email provider like Gmail. This table cuts through the marketing and shows how their core philosophies result in very different security and privacy outcomes.
| Feature | Proton Mail | Tutanota | Standard Free Email (e.g., Gmail) |
|---|---|---|---|
| Jurisdiction | Switzerland (Strong Privacy Laws) | Germany (Strong Privacy Laws) | United States (Five Eyes) |
| Encryption Model | End-to-End (OpenPGP) | End-to-End (Proprietary) | In Transit Only (TLS) |
| Zero-Access Storage | Yes | Yes | No |
| Subject Line Encryption | No | Yes | No |
| Anonymous Sign-up | Yes (Tor/VPN supported) | Yes (No phone number required) | No |
| Business Model | User Subscriptions | User Subscriptions | Data Collection & Advertising |
Laying it out like this makes the choice pretty clear. A standard free email service gives you convenience, but the price is your privacy. In stark contrast, Proton Mail and Tutanota are built from the ground up on a "privacy by design" foundation, ensuring your conversations stay yours and yours alone. They answer the question of "what is the most secure email" by aligning their entire business model with your best interests.
What to Look For Besides Encryption
End-to-end encryption is the absolute bedrock of a secure email service. You can't have one without the other. But it's only the starting point. Think of it like a bank vault door—incredibly strong, but you still need guards, security cameras, and anonymous safe deposit boxes to have a truly secure system.
The best hosted email platforms understand this. They build a fortress around your communications, protecting not just what you say, but who you are and how you say it.
Keeping Your Identity and Activities Under Wraps
A truly secure email service should let you fly under the radar from the very beginning. This starts with anonymous registration. Can you sign up without giving them your phone number or another email address? If a service demands personal information just to create an account, it’s already chipping away at your email privacy.
Then there's the issue of metadata protection. Metadata is all the information about your email: who sent it, who received it, the subject line, and the timestamp. Even if the message itself is a locked box, this "envelope" information can tell a surprisingly detailed story.
Just by looking at metadata, someone could figure out:
- Your entire network of contacts and how often you talk.
- The general topics of your conversations from subject lines.
- Your daily routine, based on when you're most active.
Top-tier services go to great lengths to strip this metadata or hide it, making it nearly impossible for anyone to map out your digital life. This is a key aspect of email privacy.
Location, Location, Location: Legal and Physical Shields
It might sound strange, but where an email provider's servers are located and where the company is registered legally is a massive security feature. A company based in a country like Switzerland, for instance, is protected by some of the strongest privacy laws on the planet. This gives them a legal backbone to fight off data requests from governments.
On the flip side, providers headquartered in a Five Eyes nation (that’s the US, UK, Canada, Australia, and New Zealand) are part of an intelligence-sharing pact. This can make it much easier for government agencies to get their hands on user data. Choosing a provider in a jurisdiction that respects privacy is like building your house in a country with strong property rights—it’s an external layer of defense that’s just as critical as the locks on your door.
Don't just skim the "About Us" page. A provider's legal home base isn't just fine print; it's a fundamental feature that dictates how well they can actually protect your data from surveillance and legal demands.
Practical Tools for Your Everyday Security
The best platforms don't just build a fortress; they hand you the keys. They provide practical, easy-to-use tools that give you direct control over your own email security.
The most important of these is two-factor authentication (2FA). It's a simple concept: to log in, you need your password plus a second piece of information, usually a temporary code from an app on your phone. This single step is a game-changer. Since a hacker would need to steal both your password and your physical phone, it effectively blocks about 99.9% of automated cyberattacks.
Other incredibly useful features include:
- Self-Destructing Messages: This lets you put a timer on an email. After it expires, the message vanishes from the recipient's inbox for good. No trace left behind.
- Tracking Pixel Protection: Marketing emails are often loaded with tiny, invisible images called tracking pixels. They snitch on you, reporting back when and where you opened the message. A good secure email service blocks these trackers automatically, keeping your reading habits private.
When you combine these practical tools with powerful encryption and a safe legal jurisdiction, you get a complete security ecosystem. It’s this multi-layered defense that truly answers the question of "what is the most secure email" by ensuring every angle is covered, from the moment you sign up to the moment an email disappears forever.
Secure Email: Your Questions Answered
Switching to a secure email provider is a big step, and it's natural to have a few questions. The technology sounds complicated, but using it day-to-day is surprisingly simple. Let's clear up some of the most common things people wonder about when they decide to take back their inbox privacy.
Getting these answers will help you feel confident that you're picking a service that actually protects your conversations.
Is a Paid Email Service Really More Secure?
Not always, but the business model makes all the difference. Free services like Gmail make their money by scanning your data to sell ads. With them, you’re the product, not the customer. This business model is fundamentally at odds with email privacy and security.
Paid secure email providers, on the other hand, charge a subscription fee. This small shift changes everything. Their success depends entirely on protecting your privacy, not selling it out. You are their customer, and their job is to keep your data safe. While many great secure services offer free plans, their paid tiers are what fund a business built on trust.
Can I Send a Secure Email to Someone on Gmail?
Absolutely, it just takes one simple, extra step. If you send an email directly from your secure account to a standard Gmail address, it won't be end-to-end encrypted by default. The link between the two services is the weak point.
To solve this, the best secure hosted email platforms let you send a password-protected, encrypted message. Your friend on Gmail gets an email with a link. When they click it, they’ll be prompted to enter a password (that you’ve shared with them separately) to unlock and read your message on a secure web page. It's a clever way to keep the conversation private, even when the other person isn't in the same secure ecosystem.
Do I Actually Need Secure Email for Everyday Stuff?
This really comes down to your personal "privacy line." For signing up for a newsletter or a quick chat with a friend about lunch plans, a standard email account might be perfectly fine.
But think about anything sensitive you send: financial documents, legal contracts, confidential business plans, or private health updates. For those, secure email is a must. It's like the difference between a simple latch on a garden shed and a heavy-duty deadbolt on your front door. Secure email is the deadbolt for your important digital life, protecting it from data miners, hackers, and prying eyes.
Choosing secure email isn't about paranoia. It's about proactively deciding which conversations deserve the highest level of protection before a problem ever happens.
What Is Metadata, and Why Should I Care?
People often call metadata "data about your data." For email, this includes things like who you sent a message to, who it came from, the subject line, and the exact time it was sent and received.
Here's the scary part: even if the body of your email is completely unreadable, the metadata can still paint a shockingly detailed picture of your life. It can reveal your entire social and professional network, the topics you're discussing, and your daily routines.
The best secure email services are built to collect and store as little metadata as possible. Protecting this information is a critical, often-overlooked layer of email privacy. It stops anyone from mapping out your life, even if they can't read a single word you've written.
Ready to take control of your inbox with a truly private email solution? Typewire offers secure, ad-free email hosting built on a foundation of privacy. With our privately owned infrastructure, zero tracking, and powerful security features, your communications remain yours and yours alone.
Start your 7-day free trial today and experience the peace of mind that comes with a genuinely secure email service. Learn more at Typewire.