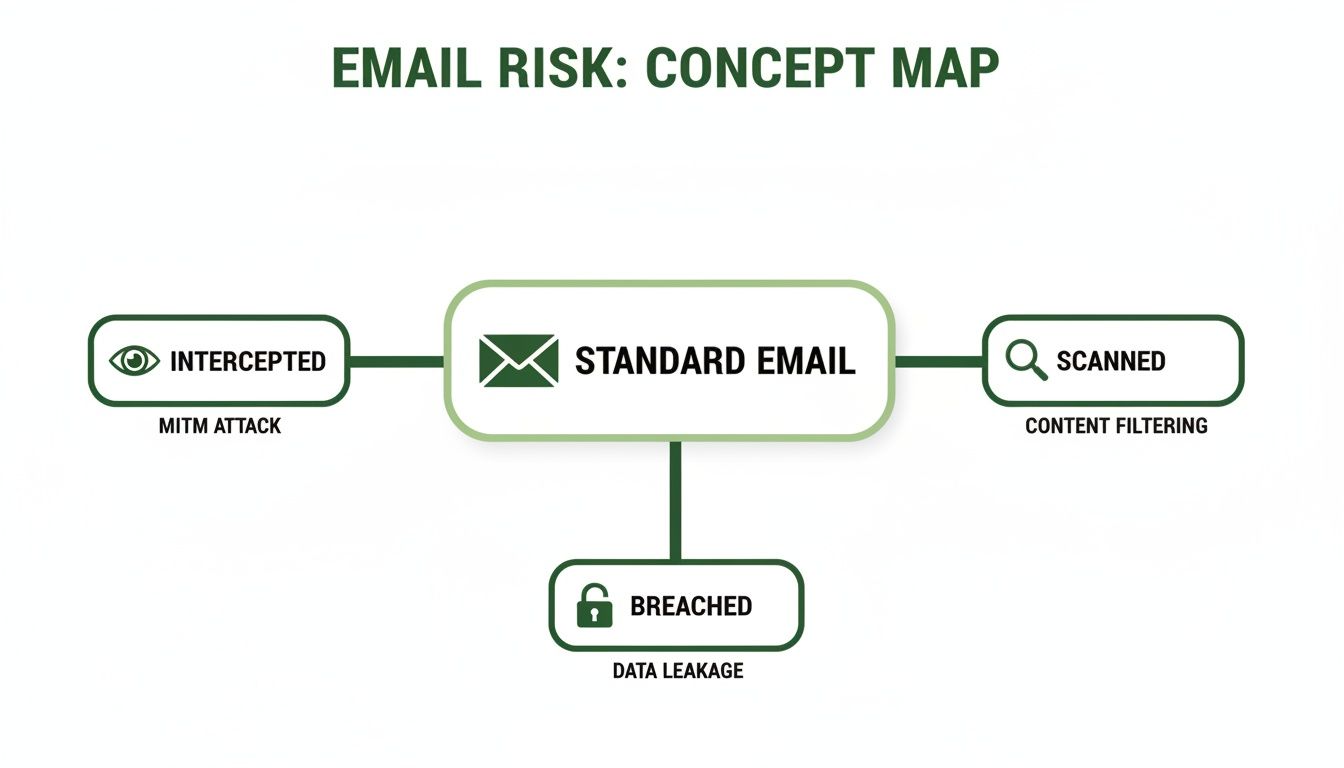
When you're looking for the best email hosting Canada has to offer, you're making a critical decision about email privacy, data security, and control. The top hosted email platforms prioritize storing your information on Canadian soil. This strategic choice keeps your data protected under strict Canadian law, shields it from foreign government access, and often leads to faster, more reliable performance for you and your contacts.
Why Canadian Email Hosting Is a Non-Negotiable for Data Privacy
Choosing an email provider is a significant security decision. You're not just picking an inbox; you're entrusting a hosted email platform with your most sensitive digital conversations. For any Canadian business or individual who takes privacy seriously, the physical location of those servers is paramount. Opting for email hosting in Canada provides your communications with a powerful legal and security shield.

This principle is known as data sovereignty—the concept that digital information is subject to the laws of the country where it’s physically stored. When your emails are hosted on servers located within Canada, they are governed entirely by Canadian privacy legislation, a cornerstone of email security.
The Power of PIPEDA Protection
The key piece of this legal protection is the Personal Information Protection and Electronic Documents Act (PIPEDA). This federal law establishes the ground rules for how private-sector organizations must handle personal information, a critical aspect of email privacy.
By choosing a hosted email platform with servers in Canada, you ensure your email data falls squarely under PIPEDA's jurisdiction. This is your primary defence against the overreach of foreign surveillance programs and data requests.
This offers a stark contrast to hosting your email on servers in other countries, particularly the United States. Data stored in the U.S. can be accessed under laws like the CLOUD Act, which can grant American authorities access to your information, regardless of your citizenship. Our detailed guide explains more about how these Canadian data privacy laws provide a crucial safeguard.
Security and Performance Benefits
While legal compliance is a major driver, local hosting brings other practical advantages. Keeping data within Canada means it has less distance to travel, which can lower latency and improve email performance. Furthermore, a provider that owns and operates its own Canadian data centres has complete control over its security infrastructure, from physical server access to network-level digital defences. This autonomy is a hallmark of secure hosted email platforms.
This focus on secure, local infrastructure is becoming more critical than ever. The email marketing software market in Canada, which is closely linked to hosting, is growing at a compound annual growth rate (CAGR) of 10.93% from 2023 to 2033. This boom is fuelled by the need to comply with strict regulations like CASL and a growing demand for secure communication channels. This surge highlights just how vital trustworthy email infrastructure is. It’s where providers like Typewire stand out by offering PIPEDA-protected, ad-free hosting on their own private servers in Vancouver, shielding users from the invasive tracking so common on mainstream platforms. You can dig into more data on the growth of the Canadian email marketing market on SphericalInsights.com.
Defining Your Email Security and Privacy Needs
Before evaluating providers, you must define your specific needs. Choosing an email hosting Canada service isn’t just a hunt for features; it’s about finding a hosted email platform whose security and privacy architecture aligns with your requirements. Getting this step right is crucial for protecting your digital communications.
It all starts with looking past marketing claims and understanding how these companies actually handle and protect your data.
The Three Pillars of Evaluation
To get a clear picture of any hosted email platform, I always break my analysis down into three core areas. Each pillar focuses on a different aspect of how your information is protected, giving you a comprehensive view of a provider's strengths and weaknesses.
- Privacy: How Your Data Is Stored. This is all about who can access your emails once they're on a server. The gold standard for email privacy is zero-access encryption. With this method, not even the provider’s own staff can read your stored messages.
- Security: How Your Data Is Protected. This covers all the active defenses against external threats. Essential email security features include advanced spam and phishing filters, robust two-factor authentication (2FA), and mandatory encryption for data in transit (like TLS).
- Compliance: How Your Data Is Governed. For any Canadian entity, this means PIPEDA. True compliance requires that servers are physically located in Canada, placing your data firmly under the protection of Canadian law.
A provider might have excellent security but weak privacy. For instance, they could offer top-tier anti-phishing tools (security) but not implement zero-access encryption (privacy), meaning they can still scan your inbox. A balanced approach across all three pillars is what you should be looking for in a hosted email platform.
Demystifying Encryption
Encryption is a term used frequently in discussions of email security, but it's often poorly understood. When it comes to email, there are two types you absolutely need to know.
End-to-end encryption (E2EE) is ideal for securing a message as it travels from you to the recipient, making it unreadable if intercepted. However, it typically requires both parties to use compatible software, which can be impractical.
Zero-access encryption, on the other hand, protects your data while it's stored on the server. The provider stores the encrypted data, but only you hold the key to decrypt it. This is a fundamental feature for true email privacy. For a much deeper look at this, our guide to private email hosting services breaks it down even further.
Building Your Personal Checklist
With these concepts clear, you can create a simple checklist to evaluate any hosted email platform. While our focus is on email, having a broader perspective on digital protection is valuable. Understanding the process of choosing a robust cyber security firm can set a higher standard for what you expect from any company handling your data.
Use these questions as your starting point:
- Data Residency: Are their primary and backup servers located exclusively in Canada?
- Encryption Standards: Do they provide zero-access encryption for stored emails? Is TLS encryption mandatory for all connections?
- Security Features: Is multi-factor authentication available? What specific technologies do they use to combat spam and phishing?
- Privacy Policy: Does their business model involve advertising or selling user data? Is their privacy policy clear and easy to understand?
Answering these questions will give you a powerful scorecard to compare your options and find a service that truly delivers on email privacy and security.
A Closer Look at Canadian Email Hosting Providers
When choosing a hosted email platform in Canada, it’s easy to get lost in feature lists. The real differentiators—those that impact your email privacy and security—are often found in the operational details. From global giants to local specialists, the right choice depends on understanding what’s happening with your data behind the scenes.
The decision ultimately comes down to three interconnected needs: keeping your communications private, securing them against threats, and meeting your legal compliance obligations.
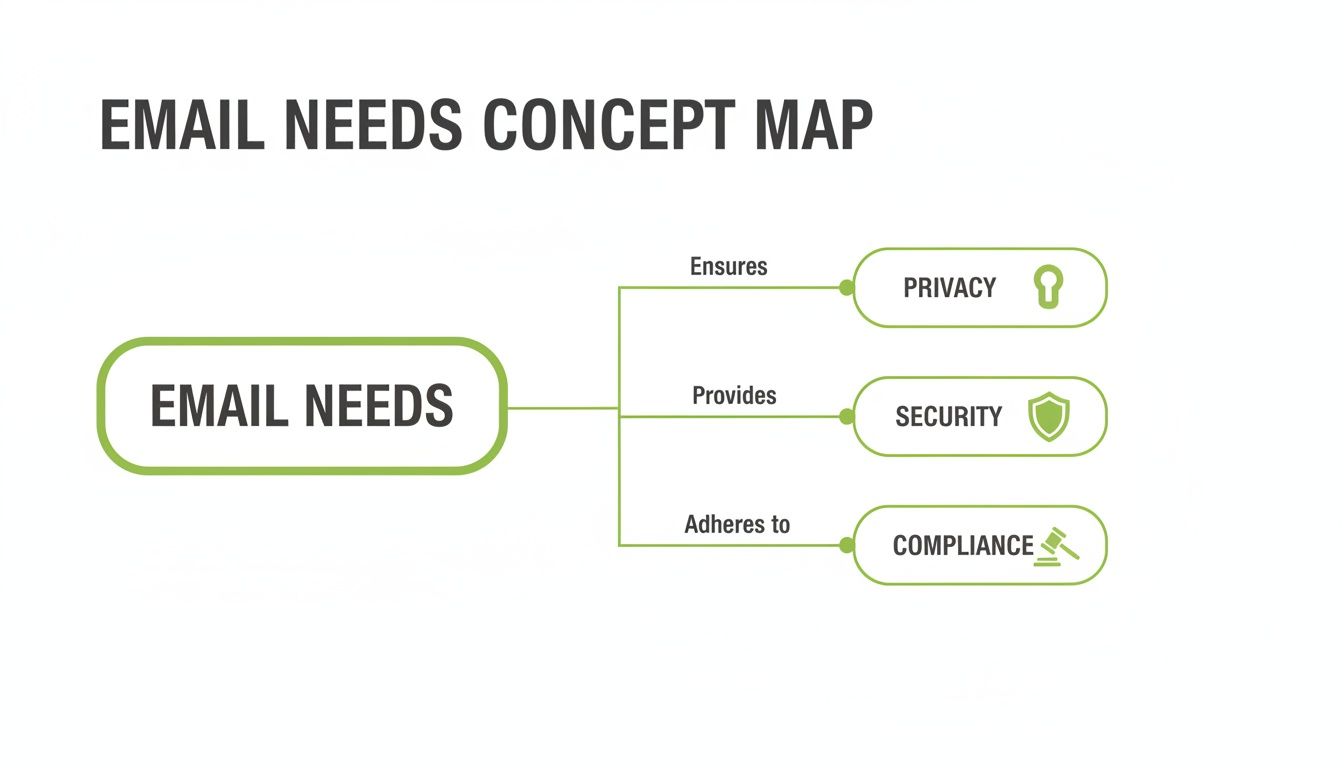
As this illustrates, a weakness in one area compromises the entire structure. A security failure can lead to a privacy breach, which in turn becomes a compliance disaster.
H3: Data Residency and Who Owns the Servers
This is arguably the most critical distinction between providers. Where is your data truly stored, and who controls the hardware? Many services claim to offer Canadian hosting, but a closer look is necessary.
Many providers simply rent space in a Canadian data centre owned by a foreign corporation. While your data is physically located in Canada, it resides on another company's infrastructure, potentially subject to their internal policies and access protocols.
In contrast, a provider like Typewire owns and operates its entire server infrastructure in Canada. This complete control eliminates grey areas and shared security responsibilities, a key feature of a truly secure hosted email platform.
When a provider owns its servers, it controls every aspect of security, from physical access to network configuration. This avoids the "shared responsibility" model common with third-party cloud services, ensuring your data's protection isn't dependent on another company's security posture.
This isn't just a technicality; it's fundamental for robust email security, PIPEDA compliance, and data sovereignty. An independent, Canadian-owned infrastructure is the strongest guarantee that your data remains under Canadian law.
H3: Encryption: The Difference Between At-Rest and In-Transit
Encryption is another area where the details are critical for email security. Any reputable provider uses TLS (Transport Layer Security) to encrypt emails in transit. The real test of a provider's commitment to your email privacy is how they handle data at rest—when it's stored on their servers.
Here’s the typical breakdown:
- Standard Encryption at Rest: The provider encrypts the hard drives where your data is stored. This is a solid security measure against physical theft of hardware. However, the provider holds the encryption keys, meaning they can still access your data.
- Zero-Access Encryption: This is the gold standard for email privacy. With zero-access encryption, your emails are encrypted with a key that only you possess. The provider cannot decrypt or read your messages, even under legal compulsion.
For anyone handling sensitive information, zero-access encryption is an essential email security feature. Our secure email hosting services comparison breaks down which providers actually offer this level of protection.
H3: Spam Filtering and Business-Ready Tools
Beyond core security, you need an email service that is reliable and efficient. This means having excellent spam filtering and the tools to manage business communications effectively.
While most services offer basic spam filters, the best hosted email platforms use machine learning to adapt to new threats, catching sophisticated phishing emails without blocking important messages.
When you're comparing features for business use, keep an eye out for:
- Custom Domain Support: Every professional needs a custom domain (e.g.,
contact@yourbusiness.ca). Look for hosts that easily handle multiple domains and aliases under one account. - User Management: A clean, centralized dashboard for managing users, storage, and permissions is essential for any team.
- Migration Support: Moving from another provider can be challenging. A service that offers guided migration can save time and prevent data loss.
The Canadian web hosting market is lively, with major players like Shopify holding 27.1%, Tucows at 11.9%, and OVHcloud at 9.1%. This competition creates an opportunity for independent providers to stand out by focusing on email privacy and local data control. This is exactly where a solution like Typewire fits in, using its privately owned, PIPEDA-compliant infrastructure in Vancouver to offer a truly secure alternative.
H3: Feature Comparison of Canadian Email Hosting Providers
To highlight the differences, this table compares the typical offerings of hosted email platforms. It focuses on features critical for Canadian businesses and privacy-conscious users.
| Feature | Typewire | Global Provider A | Canadian Provider B |
|---|---|---|---|
| Data Residency | Guaranteed Canadian on privately owned servers | Can be selected, but often part of a global network subject to foreign laws. | Typically Canadian, but often on rented third-party infrastructure. |
| Encryption at Rest | Zero-access encryption standard on all plans | Standard encryption; provider retains access for data processing. | Standard disk-level encryption is common; zero-access is rare. |
| Server Ownership | 100% privately owned and operated in Canada | Hosted on massive, third-party cloud infrastructure (e.g., AWS, Azure, GCP). | A mix of owned and rented servers, sometimes from foreign corps. |
| Business Model | Subscription-based. Your data is never monetized. | Data is often used for analytics, product improvement, and ad targeting. | Primarily web hosting sales; email is often a bundled add-on. |
| PIPEDA Compliance | Built from the ground up for full PIPEDA compliance. | Compliant, but data may cross borders, creating legal complexities. | Generally compliant, but depends on their data centre partners. |
| Admin & User Tools | Modern UI/UX with simple multi-domain and alias management. | Powerful but can be complex; designed for large enterprises. | Often basic interfaces, tied into a larger web hosting panel. |
| Support | Direct access to specialized, expert support. | Large-scale, often automated support systems; can be hard to reach a human. | General support covering a wide range of web services. |
This comparison makes it clear that your choice has real consequences for email privacy and security. For those who prioritize data sovereignty and absolute privacy, the decision goes far beyond price and storage. It’s about asking who owns the servers, what kind of encryption they use, and what their business model is. For many Canadians, the answer points toward providers who built their foundation on keeping data safe and local.
Which Email Host Is Right for Your Specific Use Case?
Choosing the right provider for email hosting in Canada isn't about ticking boxes on a pricing page. The best hosted email platform is the one that fits how you work, what you need to protect, and your day-to-day operations. A feature that’s critical for one user might be irrelevant to another.
To be practical, let's examine three common scenarios. We’ll look at each user profile and match it with a hosted email solution that solves their biggest email security and privacy challenges.
For the Solo Entrepreneur or Freelancer
If you're a solo entrepreneur, your primary mission is building a professional brand. Sending emails from a generic free account can undermine credibility. An address like contact@yourbusiness.ca instantly signals legitimacy and trustworthiness.
For this user, the needs are straightforward:
- Custom Domain Support: This is priority number one for branding.
- Reliability and Simplicity: They need a platform that is easy to manage without technical expertise.
- Affordability: As a one-person operation, cost-effectiveness is key.
A privacy-first Canadian host with a simple custom domain setup and an intuitive control panel is the perfect fit. Deep administrative tools are not necessary, but strong spam filtering and guaranteed uptime are essential for maintaining a professional image and ensuring smooth communication.
For the Healthcare or Legal Professional
Professionals in fields like healthcare, law, or finance are custodians of incredibly sensitive personal information. For them, email privacy and security are legal and ethical mandates, not just best practices. Their choice of hosted email platform must reflect this serious responsibility.
The real deciding factor here is how a provider handles data at rest. Zero-access encryption is a must-have, as it guarantees that not even the hosting company's employees can read stored patient or client communications. It ensures absolute confidentiality.
The evaluation criteria become much stricter here:
- Strict PIPEDA Compliance: The provider needs an ironclad commitment to Canadian data residency on privately owned servers.
- Zero-Access Encryption: This is non-negotiable for protecting client privilege and patient confidentiality.
- Robust Security Measures: Advanced phishing protection and mandatory two-factor authentication are crucial email security features to prevent unauthorized access.
For this professional, a provider like Typewire becomes the only sensible option. Its entire foundation is built on Canadian-owned infrastructure and default zero-access encryption, directly addressing the core compliance and email privacy demands of handling sensitive data.
For the IT Manager of a Small Business
An IT manager for a team of 10-50 employees faces a different set of challenges. Email security is a top concern, but their focus also includes efficient administration, scalability, and seamless team collaboration. They need a hosted email platform that simplifies their job.
Their critical feature checklist includes:
- Centralized User Management: A clean dashboard to add or remove users, set storage quotas, and manage permissions is vital.
- Multi-Domain and Alias Support: Managing emails for different departments (e.g.,
sales@andsupport@) from a single account saves time. - Advanced Deliverability and Anti-Spam: They must ensure company emails reach client inboxes while protecting employees from sophisticated threats.
For businesses that rely on team collaboration, it’s also wise to see how a host supports shared inbox solutions. This use case demands a balanced solution—one that combines strong email security with powerful, easy-to-use administrative tools built for a business environment.
This focus on business communication is becoming even more critical. E-mail advertising spending in Canada is projected to hit US$322.13 million in 2025, largely because consumers want more authentic messaging from brands. This trend makes secure hosting even more urgent, as businesses need to block tracking pixels and keep their communications free from data harvesting—reinforcing the need for private, PIPEDA-compliant solutions. You can find more insights about Canadian email advertising trends on Statista.com.
Your Actionable Checklist for a Seamless Email Migration
Moving your company’s email hosting feels like a massive undertaking, but with a solid plan, you can avoid common pitfalls. A well-planned migration is more than just transferring data; it's about ensuring business continuity. Breaking the process into manageable stages is key to preventing downtime and data loss.

Before any technical work begins, preparation and communication are crucial. This groundwork prevents surprises and ensures your team is ready for the switch. A truly smooth transition starts long before the first email is moved.
Phase 1: Pre-Migration Planning
The success of your entire migration hinges on this first phase. Rushing this stage often leads to forgotten accounts, lost emails, and a frustrated team. Take the time to map everything out carefully.
Here’s what you need to do before you start:
- Inventory Your Accounts: Create a complete list of every email address in use, including user inboxes, shared aliases like
info@orsales@, and any forwarding rules. - Communicate with Your Team: Inform everyone about the migration. Provide a clear timeline, explain what to expect, and designate a point of contact for questions.
- Perform a Full Backup: Before making any changes, back up everything. This is your safety net. If anything goes wrong, you'll have a complete copy of your historical data.
Many businesses overlook or rush the backup step, assuming the new provider’s import tool will be flawless. Think of a separate, offline backup as your ultimate insurance policy. It protects you from data corruption or transfer errors, guaranteeing you can restore critical information no matter what.
Phase 2: The Technical Migration
With your preparation complete, it's time for the technical side of the migration. Here, you will configure the new service and begin moving your historical data. Precision is critical—a wrong setting can disrupt your email flow.
Reputable hosted email platforms usually offer migration tools or hands-on support to minimize downtime.
Follow these steps carefully:
- Create New Mailboxes: Using your inventory list, set up all user accounts, aliases, and forwarders on your new email platform.
- Import Historical Data: Initiate the data transfer using your new provider's import tool. This process will pull over old emails, contacts, and calendar entries. Start this during off-peak hours to minimize disruption.
- Update Your Domain's DNS Records: This is the "flip the switch" moment. Update your domain's MX records to point to your new email host. Once this change propagates, all new incoming mail will be directed to your new provider.
Phase 3: Post-Migration Verification
The technical part is done, but the process isn't complete. The final phase is about confirming everything works as expected and helping your team adjust. This final check ensures a successful transition.
- Test Email Flow: Send test emails to and from each new mailbox to confirm that sending and receiving are functioning correctly.
- Provide User Support: Be available to help your team set up their email clients (like Outlook or Apple Mail) and answer questions about the new system.
- Decommission the Old Service: Only after you are 100% confident that all data is migrated and the new system is running smoothly should you cancel your old email hosting service.
By following this checklist, you can manage the migration process with confidence, ensuring a smooth and secure move to your new Canadian email host.
A Few Common Questions About Email Hosting in Canada
When researching hosted email platforms in Canada, a few key questions consistently arise. Getting clear answers is the final step before confidently selecting a service that protects your communications and meets your business needs.
Let's address some of the most common queries about email privacy and security.
Why Is PIPEDA Compliance Such a Big Deal for Email Hosting?
Think of PIPEDA (the Personal Information Protection and Electronic Documents Act) as Canada’s privacy rulebook for the private sector. It governs how businesses must handle personal information. For your email, this is a legal framework that safeguards your data.
Choosing a Canadian email host with servers located exclusively on Canadian soil ensures your digital conversations are protected by our laws. This is a crucial distinction from using a provider with servers in other countries, like the United States. Data stored in the U.S. may be subject to laws like the CLOUD Act, potentially giving foreign governments access to your private information.
The single best way to guarantee data sovereignty is to choose a hosted email platform built around PIPEDA. This ensures your private emails, client information, and business records are all kept under the protection of Canadian law, creating a solid defense against foreign data requests.
Ultimately, PIPEDA compliance is your assurance that a provider is serious about your email privacy and has the legal and technical infrastructure to back it up.
What's the Real Difference Between End-to-End and Zero-Access Encryption?
These two encryption methods sound similar but protect your data in very different ways, highlighting a provider's commitment to true email privacy.
End-to-end encryption (E2EE) protects data in transit. It scrambles a message on the sender's device, and only the recipient's device can unscramble it. This makes it unreadable if intercepted. However, true E2EE often requires both parties to use compatible software, which can be impractical for everyday business.
Zero-access encryption, on the other hand, protects your data at rest on the provider's servers. It means your stored emails are encrypted with a key that only you possess. The hosting provider cannot read your messages, even if legally compelled to do so, because they don't have the key.
The most secure email platforms combine strong in-transit encryption (like TLS) with zero-access encryption for stored data. This creates a comprehensive privacy and security shield, protecting your information at all times.
Can I Use My Own Domain With a Private Canadian Email Host?
Absolutely. This is an essential feature for any professional or business. Any reputable Canadian hosted email platform will fully support custom domains, allowing you to set up professional addresses like yourname@yourcompany.ca. Using your own domain is crucial for building a credible brand and gives you complete control over your email identity.
The setup process is typically straightforward, involving a simple update to your domain's DNS records to point to the new email host. The best providers offer clear instructions and support to guide you through these changes.
Is a Free Email Service Really Good Enough for My Business?
That "free" price tag comes with significant hidden costs, primarily to your email privacy and professionalism. Free email services typically generate revenue by scanning your emails to build advertising profiles. Their business model is fundamentally at odds with data privacy.
From a practical standpoint, free services also lack essential business features:
- No Custom Domain: A generic email address can damage client trust and look unprofessional.
- Weaker Security: These services are prime targets for phishing attacks and often lack the advanced email security tools you need.
- Limited Support: When issues arise, you are often left with community forums rather than dedicated expert support.
For any serious business, the risks of data mining, a damaged reputation, and privacy breaches far outweigh the perceived "savings." Investing in a paid, private hosted email platform isn't an expense; it's a foundational investment in your email security and brand integrity.
Ready to secure your communications with a truly private Canadian email solution? Typewire offers zero-access encrypted email on 100% Canadian-owned servers, fully compliant with PIPEDA. Protect your data, use your own domain, and enjoy an ad-free inbox. Start your free 7-day trial today at https://typewire.com.