Ready to set up a professional email address like contact@yourbrand.com without opening your wallet? The secret is to pair a free domain name with a free email hosting service that plays nicely with custom domains. It's a straightforward two-part strategy that gives you a polished, credible presence from day one.
A Custom Email Domain Is a Serious Upgrade
Before we get into the "how," let's talk about the "why." Shifting from a generic address like yourbrand24@gmail.com to a sharp, branded one like hello@yourbrand.com is a massive leap in perception. It’s one of those small details that instantly tells potential clients, partners, and customers that you're serious about what you do.
This simple change packs a real punch. It shows you’ve taken the time to establish a proper brand identity—a detail that helps you stand out, especially if you’re a freelancer or a startup on a lean budget. It's a powerful way to look just as established as the big guys, and the best part is, it doesn't have to cost a thing. You can learn more about how a custom domain boosts your business credibility in our detailed guide.
The Two Core Pieces of the Puzzle
Getting this up and running is probably easier than you think. Your entire setup will depend on just two key components working together.
-
A Free Domain Name: This is your unique address on the web, like
yourbrand.ml. We'll look at services that offer these completely free of charge. -
A Free Email Hosting Service: This is the engine that actually handles sending, receiving, and storing your emails. A few excellent providers offer generous free plans that are perfect for this.
For example, a service like Freenom can provide the domain name at no cost. You'll use their interface to find and register a domain with an extension like .tk, .ml, or .ga.
Once you have your domain, you can connect it to a free email host like Typewire or Zoho Mail to create a fully functional, professional email system. The key is finding services that allow this custom domain integration on their free tiers.
Your Free Custom Email Toolkit
Here's a high-level look at the two essential parts you'll need to create your free custom email address. Understanding these components is the first step.
| Component | Its Role in Your Setup | Example Free Providers |
|---|---|---|
| Free Domain Name | Your unique address (the part after the "@"). It establishes your brand identity. | Freenom, Dot TK, GetFreeDomain.Name |
| Free Email Hosting | The service that powers your mailbox. It sends, receives, and stores your mail. | Typewire, Zoho Mail, GMX Mail |
By combining one from each column, you have everything you need. This approach is the foundation for building your brand's credibility and reinforcing your identity with every single email you send.
Finding and Securing Your Free Domain

Getting your own domain is the first real step in carving out your professional space online. It's the part of your email address that comes after the "@" symbol, and it's your unique piece of digital real estate. Forget the idea that this has to be a complicated or expensive process. Services like Freenom make it surprisingly simple, offering domains with extensions like .tk, .ml, or .ga at no cost.
Your main goal here is to find a name that's easy to remember, looks professional, and connects directly to you or your brand. I always suggest starting with a quick brainstorm of your core ideas—think about your name, what you do, or what your business is called. If you're a freelance writer named Jane Smith, something like janesmithwrites.tk or jsmithcreative.ml could work perfectly.
Brainstorming Your Perfect Domain
What if your first choice is already gone? It happens all the time, so don't get hung up on it. This is where you get to be a little creative. A simple trick is to add a verb, your location, or a word that describes your industry to make the domain unique.
Here are a few ideas to get you started:
- Add an action word:
Get[YourName]Creative.ga - Include your service:
[YourName]Designs.tk - Use your initials:
jscreative.ml
To make sure your custom email really pops, it's worth checking out some expert tips for finding good domain names that are both memorable and professional. While ".com" is the old standby, many pros are now strategically choosing other extensions to better reflect their role or industry.
For instance, it's become common to see people choose from over 100 brand-neutral domains to shape their email identity. Popular choices often include professional titles, like @consultant.com or @engineer.com. This is a great example of how a specific domain can reinforce your professional image, even without a traditional .com.
Key Takeaway: The most important thing is to pick a name that builds trust. A clear, professional domain sets the tone for every email you send, acting as a critical first impression for clients, colleagues, and collaborators.
One last piece of advice: always check the provider's renewal policy. Free domains almost always require an annual renewal. It's still free, but you have to do it to keep your domain active. I can't tell you how many people forget this, so do yourself a favor and set a calendar reminder. It’s a simple step that ensures you don't accidentally lose it.
Choosing the Right Free Email Host for Your Needs
You've snagged your free domain—great! Now, you need to decide where your emails will actually be handled. This is the job of an email host, which acts as the behind-the-scenes engine for your new, professional email address. Your goal here isn't just to find any free service, but one that fits what you're trying to accomplish, whether that’s managing client communications or just simplifying your digital life.
Several providers offer solid free plans to get you started. Zoho Mail is a fan favorite for anyone who wants a full-fledged inbox without pulling out a credit card. Their "Forever Free Plan" is surprisingly powerful for a zero-cost option.
Full Inbox vs. Simple Forwarding
You're at a fork in the road, and your decision really comes down to two main approaches: a dedicated inbox or a simple forwarding service.
- A full inbox from a provider like Zoho gives you a completely separate mailbox. Think storage, a calendar, and contacts—the whole nine yards. This is perfect if you want a clear line between your professional and personal emails.
- A forwarding service like ImprovMX is a more lightweight solution. It simply takes any email sent to
you@yourdomain.comand automatically routes it to an existing address, like your personal Gmail. This is a fantastic way to consolidate all your messages in one place.
Here’s a look at the Zoho Mail interface. It’s clean, professional, and will feel familiar if you've used any other major email client before.

The user-friendly layout makes it easy to jump right in and start managing your emails without a steep learning curve.
Comparing Top Free Email Hosting Services
To help you decide, here’s a quick comparison of some of the leading free email hosting and forwarding providers. Each one shines in a different area, so think about what matters most for your specific needs.
| Provider | Best For | Storage Limit | Key Feature |
|---|---|---|---|
| Zoho Mail | Full-featured inbox for small businesses | 5 GB/user | Includes calendar, contacts, and notes |
| ImprovMX | Simple and reliable email forwarding | N/A | Easy setup and unlimited aliases |
| Forward Email | Privacy-focused forwarding | N/A | Open-source with a strong focus on security |
| Mailgun | Developers needing powerful APIs | 1,000 free emails/month | Primarily for transactional and marketing emails |
Ultimately, the "best" choice is the one that aligns with your technical comfort and daily workflow.
What to Look For Beyond the Basics
Making the right call means looking at the bigger picture. Security, for instance, is absolutely critical. It's easy to forget that providers offering free services still have significant infrastructure costs to cover—often around $0.14 per user per month. Because of this, they take security very seriously to protect their entire network. Thankfully, with multi-factor authentication usage expected to hit 95%, your account will be well-protected. You can find more details on email infrastructure costs and security in this 2025-2030 email statistics report.
My Advice: Don't get fixated on just the storage limit. I've found that the user interface, mobile app quality, and ease of DNS setup are what really make or break the experience. A confusing setup process can turn a free service into a massive headache.
For a more detailed comparison of different options, check out our guide on the 7 best small business email service providers in 2025.
Connecting Your Domain and Email Host
Alright, you've picked out your domain and have an email host ready to go. Now, it's time for the magic trick: getting them to talk to each other. Essentially, you need to tell your domain where to send all your incoming mail. This is done by tweaking your Domain Name System (DNS) settings, which sounds technical, but I promise it's more like changing a contact's address in your phone.
Think of DNS as the internet's grand central station for traffic. Your job is to add a specific signpost, called an MX (Mail Exchange) record, that directs all email-bound traffic to your hosting provider. This little record is the critical link ensuring emails actually make it to your inbox. Once you have your domain, the next logical step is integrating it correctly, which this guide on how to add your custom domain walks you through.
Pointing Your Domain in the Right Direction
First, you'll need to log into your domain registrar's dashboard—the same place you got your free domain. From there, look for a section called "DNS Management" or something similar. Your email provider will give you the exact values for the MX records you need to add. It's usually just a copy-and-paste job.
This diagram lays out the basic flow for getting your domain registrar and email host on the same page by adding and verifying these records.
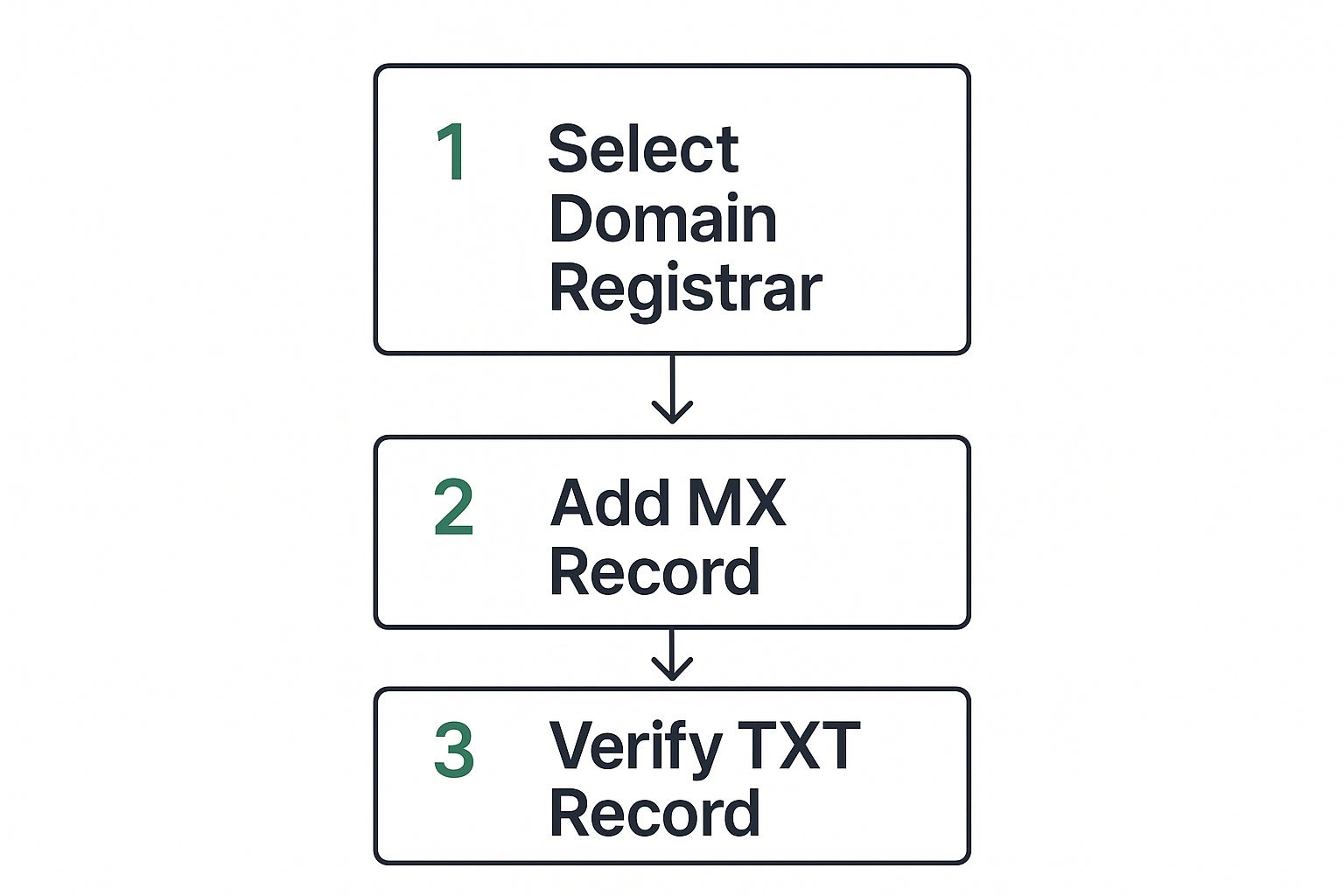
As you can see, the core of the process is adding that MX record. Then, you'll often use a TXT record to verify that you actually own the domain you're trying to set up.
A Quick Word of Advice: Once you hit 'save' on those new records, don't expect your email to work instantly. It can take anywhere from 30 minutes to 48 hours for these changes to fully update across the global internet. This waiting period is called "propagation." So, grab a coffee and be patient before you start thinking something's broken.
Fine-Tuning and Securing Your New Professional Email

Alright, the technical plumbing is connected. Now it's time for the fun part: turning your basic setup into a professional communication tool that's both polished and secure. This is where you move beyond just sending and receiving messages and start building trust from your very first email.
A simple but powerful first step is crafting a professional email signature. Think of it as your digital business card. It should be clean and instantly reinforce your brand in every message. Be sure to include your name, title, and a link back to your website or primary social profile.
You should also look into using email aliases. An alias like info@yourdomain.com or support@yourdomain.com can make a one-person operation feel much bigger. It helps you organize incoming mail and maintain a professional front, all while managing everything from a single inbox.
Beefing Up Your Account Security
Getting a free email domain set up is one thing, but keeping it locked down is a whole different ballgame. Your absolute top priority now should be building strong defenses to protect your account from bad actors who could seriously damage your reputation.
Account security isn't just an optional add-on; it's the bedrock of professional communication. A single breach can expose sensitive client data, shatter trust, and bring your business to a screeching halt. Robust protection is non-negotiable.
This all starts with a strong, unique password that you haven't used anywhere else. But let's be honest, a password alone isn't enough anymore. The single most effective thing you can do for your security is to turn on two-factor authentication (2FA).
Enabling 2FA adds a second verification step, usually a temporary code sent to your phone. It means that even if a hacker steals your password, they're stopped in their tracks because they don't have your phone. It’s a simple move that makes a huge difference. To really nail this down, you can learn more about how to authenticate your email with a real-world setup guide and ensure your conversations stay private.
Got Questions About Free Email Domains? We've Got Answers
Setting up a free email domain for the first time can bring up a few questions, even when the steps seem simple. I get it. Let’s clear up some of the common uncertainties so you can move ahead with confidence and make the most of your new professional email.
Are Free Email Domains Really Free Forever?
Here’s the deal: most free domains, especially those ending in .tk or .ml, aren't a "set it and forget it" situation. You usually have to renew them, and while the renewal itself is free, it's a manual step you need to take. This could be every month or once a year, depending on the provider. It's an easy thing to forget, and a common reason people lose their free domains.
The same logic applies to free email hosting. These services often have caps on storage, the number of users you can add, or other features. Their whole business model is built on the hope that as you grow, you'll eventually upgrade to a paid plan for more horsepower.
My Advice: The moment you register your domain, open your calendar and set a reminder for the renewal date. Seriously, do it right away. And always take a few minutes to skim the terms of service for both your domain and email providers to avoid any surprises.
Can I Use My Custom Email with Gmail or Outlook?
Absolutely! This is one of the best parts. You don't have to learn a whole new email platform. You have a couple of great options for managing your new email address from a client you already use every day.
- Full Integration (IMAP/POP): If you go with a service like Zoho Mail, you can plug your custom email directly into Gmail, Outlook, or Apple Mail. They give you all the server settings you need, and you can send and receive emails from your custom address right inside that familiar interface.
- Email Forwarding: A simpler route is using a forwarding service like ImprovMX. This just creates a rule that sends any email from
contact@yourdomain.comstraight to your personal Gmail or Outlook. Easy.
What Is the Biggest Downside of a Free Email Domain?
The two main trade-offs are perception and long-term stability. Let's be honest, some free domain extensions have a bit of a reputation for being used for spam. This could mean your emails have a slightly higher chance of landing in a junk folder, or that some people might not take your address as seriously.
You’re also banking on the provider sticking around and keeping its free service going. For a critical business, spending a few bucks a year on a standard .com or .io domain is usually the safer, more professional bet. But for a personal project, a new side-hustle, or just testing out an idea? A free domain is a fantastic and practical way to get started.
Ready for a secure, private email experience without the ads and tracking? Typewire provides robust email hosting with custom domain support, ensuring your communications remain under your control. Start your 7-day free trial and experience the difference today at https://typewire.com.






