Setting up an anonymous email isn't just about picking a random username. The goal is to create a secure communication channel with no ties back to your real identity. This involves choosing a hosted email platform focused on privacy, masking your IP address with a VPN or Tor during setup, and meticulously avoiding the use of any real personal details.
Done right, this approach gives you a powerful tool that truly protects your identity and secures your communications.
Why You Need a Secure and Private Email Today
In a world where our data is constantly being bought and sold, your email address has become a digital passport. It's the key to your social media, your financial accounts, and countless private conversations. Strong email security isn't a luxury; it's a necessity.

Mainstream hosted email platforms like Gmail and Outlook are built for convenience, but they aren't designed for genuine email privacy. Their business models often rely on collecting your data to serve targeted ads, meaning your activity is perpetually linked to your personal profile.
Anonymous email flips that script. It’s built from the ground up to decouple your identity from your inbox. This isn't about hiding illicit activity; it's about reclaiming your fundamental right to privacy and enhancing your email security.
With over 4.6 billion people expected to use email daily by 2025, it’s clear that email is the central hub of our digital lives. That massive scale makes it more important than ever to have options that protect us from constant surveillance and data harvesting. You can dig deeper into these figures with recent email usage statistics.
Getting the Terminology Right
Before diving into the how-to, it’s crucial to understand a few key concepts that are central to email privacy and security.
- Anonymous Email: The primary objective is to hide who is sending the message. A truly anonymous email platform is built so the provider knows as little as possible about you. Your real name, IP address, and location should never be connected to the account.
- Private Email: This is all about data ownership and control. A private provider promises not to scan your emails, sell your data to advertisers, or track your activity. The focus is on ensuring your personal information remains confidential.
- Encrypted Email: This protects the content of your messages. Using end-to-end encryption, only you and the recipient can read the email. The message is unreadable to the email provider and anyone else who might intercept it, ensuring message confidentiality.
The gold standard is a hosted email platform where all three of these overlap. You want an anonymous account from a private, no-logs provider that also offers strong, end-to-end encryption for maximum email security.
For many, anonymity is a necessity. Journalists protecting sources, activists in oppressive regimes, and everyday people avoiding targeted ads all rely on secure email. It's a shield that enables free expression and keeps you safe.
Choosing the Right Anonymous Email Provider
Selecting your hosted email platform is the most critical decision in this process. Forget the big names; they are built for data collection, not confidentiality. A secure and anonymous email service prioritizes your privacy as the core of its platform.
This means you must look past the marketing and scrutinize the features that truly matter for email security. A provider's promises are only as strong as its technical implementation and legal framework.
Jurisdiction and Legal Protections
Where an email company is legally based can make or break your privacy. A provider headquartered in a country with strong privacy laws, like Switzerland or Germany, offers a powerful legal shield from the outset.
These countries are not part of major intelligence-sharing pacts like the "Five Eyes" alliance (US, UK, Canada, Australia, and New Zealand). This makes it significantly harder for foreign governments to compel a company to surrender your data.
A provider's location isn't just a mailing address; it's a legal shield. Choosing a service in a country with robust data protection laws is a non-negotiable first step for genuine email privacy.
No-Logs Policies and Encryption Standards
A provider’s privacy policy is a crucial document. You are looking for a service with a rock-solid zero-knowledge or no-logs policy. This means they don’t store any data that could identify you, such as your IP address, login times, or device information. If the data isn't collected, it can't be seized or leaked.
Equally critical is the encryption standard. End-to-end encryption (E2EE) should be the default. This ensures only you and the recipient can read the message; not even the provider can decrypt your emails. The gold standard for this is open-source technology like OpenPGP.
This infographic gives you a quick visual on how to weigh these key factors when you're comparing services.
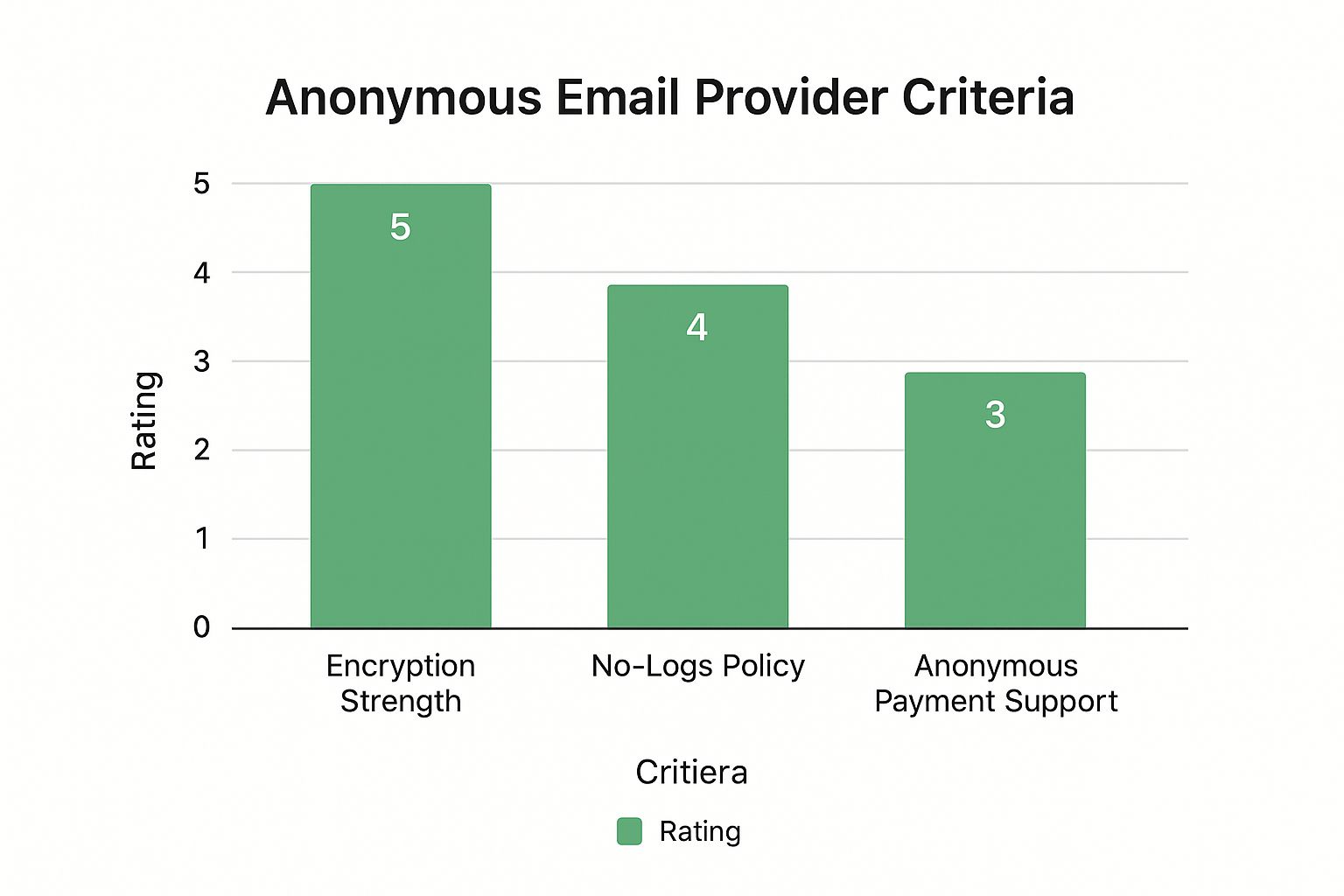
As you can see, the best services don't just excel in one area. They offer a comprehensive suite of privacy protections.
Anonymous Payments and Account Creation
How you pay for a service can instantly link it to your real identity. The best private email providers understand this and offer payment methods that preserve your anonymity.
- Cryptocurrency: Paying with privacy coins like Monero, or even Bitcoin, is a standard feature for top-tier services.
- Cash Payments: Some services even allow you to mail cash to a PO box, offering the ultimate in anonymous payments, though with less convenience.
- No Personal Info Required: The sign-up process itself should be minimal. If a provider demands your name or phone number, it’s a major red flag for privacy.
To help you compare options, here is a quick overview of leading hosted email platforms in the privacy space.
Comparing Top Anonymous Email Providers
This table breaks down how different hosted email platforms stack up against the most important privacy and security features we've discussed.
| Provider | Jurisdiction | Encryption Type | No-Logs Policy | Anonymous Payment |
|---|---|---|---|---|
| Proton Mail | Switzerland | End-to-End (OpenPGP) | Yes (Zero-Access) | Yes (Crypto/Cash) |
| Tutanota | Germany | End-to-End (Proprietary) | Yes (Strict) | Yes (Crypto) |
| Mailfence | Belgium | End-to-End (OpenPGP) | Yes (No tracking) | Yes (Crypto) |
| CounterMail | Sweden | End-to-End (OpenPGP) | Yes (Diskless servers) | Yes (Crypto) |
Ultimately, the best choice depends on your specific threat model and which security features you prioritize, but hosted email platforms like these are designed from the ground up for email privacy.
For a more in-depth look, check out our guide on the top 7 best email providers for privacy in 2025, which details the pros and cons of each. By evaluating jurisdiction, logging policies, encryption, and payments, you can confidently choose a platform that truly protects you.
Setting Up Your Account for True Anonymity
Choosing the right hosted email platform is just the first step. The real test of anonymity and security lies in how you set up and manage your account. Every choice during sign-up can either strengthen your email privacy or create a vulnerability.

First, Mask Your Digital Footprint
Before you even visit your chosen email provider's website, activate a reputable VPN. This is a non-negotiable step for your email security.
A VPN encrypts your connection and routes it through a server elsewhere in the world. This means your email service provider sees the VPN's IP address, not your personal one. This simple action is crucial for severing the link between your real-world location and your new anonymous email account.
Craft an Identity From Scratch
With your connection now cloaked, it's time to create the account. This requires creativity and strict discipline. Your mission is to avoid any detail that could possibly trace back to you.
Your username should not be a variation of your real name, a known nickname, or anything used on other platforms. If your name is Jane Doe and you were born in '92, "JaneDoe92" is a poor choice. Something random like "WinterCoyote4" or a generated passphrase is much more secure.
The same discipline applies to your password and any recovery information.
- Create a Unique, Strong Password: Use a password manager to generate a long, complex password you've never used before. Reusing passwords across services is a critical security flaw that could link your anonymous account to other profiles.
- Dodge Personal Recovery Emails: Never list your personal Gmail or Outlook account as a recovery option. This creates a direct, permanent link between your anonymous and real identities. If a recovery email is required, create a second anonymous email solely for that purpose.
Think of your anonymous identity as a complete fabrication. No real names, no familiar handles, and zero ties to your existing online life. Every bit of information you provide should be generic and untraceable.
Some services may request a phone number for verification, which is a significant privacy concern. You can bypass this using temporary or virtual phone numbers for verification. Better yet, choose one of the many email providers that don't require phone number verification.
Harden Your Account with Aliases and Settings
Your account is created, but the work isn't done. Most secure hosted email platforms offer features that can significantly boost your anonymity and email security.
Email aliases are a powerful tool. An alias is a disposable forwarding address that directs mail to your main inbox. You can create a unique one for every service you sign up for. If an alias is compromised or spammed, you can simply delete it without affecting your primary account.
Finally, dive deep into your account settings. Many email clients load remote images by default, but these can contain tracking pixels that reveal when and where you opened a message. Disable this feature. By meticulously configuring these settings, you can transform a basic secure account into a truly anonymous communication channel.
Daily Habits for Maintaining Email Privacy
Setting up your anonymous email correctly is a major win for your privacy, but it's just the beginning. True anonymity is not a one-time setup; it's a daily practice. The key to long-term protection is building a security-first mindset and developing strong habits.
Your security tools are only as effective as how you use them. Every email you send and every link you click is a decision that can either protect or expose you. The goal is to make email privacy a natural part of your routine.
Practice Smart Operational Security
This is where OpSec, or Operational Security, is essential. It involves protecting your sensitive information by managing your own behavior. For anonymous email, this means creating a strict separation between your real and anonymous identities.
- Never Mix Identities: This is the golden rule. Your anonymous email is for anonymous activities only. Do not use it for personal accounts, and keep your personal email completely separate.
- Use a Dedicated Browser: Access your anonymous email from a privacy-focused browser like Brave or the Tor Browser. Avoid your everyday browser, which is likely filled with cookies, trackers, and logged-in sessions tied to your real identity.
- Physical Security Matters: Don't neglect the physical world. A critical part of keeping your email private is adopting smart routines, including proper data wiping practices for old devices before disposal. You don't want residual data to compromise your security.
This discipline is non-negotiable. It prevents accidental slip-ups that can link your two worlds. Even one mistake, like checking personal social media in your "anonymous" browser, can undermine your entire setup.
Anonymity is a continuous process of vigilance. Your daily habits—from the browser you open to the way you write a message—are what ultimately keep your identity private.
Mind Your Metadata and Attachments
The content of your email is just one part of the story. The hidden data attached to your messages and files can be just as revealing and pose a significant email security risk.
Even your writing style can act as a digital fingerprint. Linguistic analysis can potentially connect your anonymous writing with public posts on forums or social media. Consider consciously adopting a different tone or sentence structure to obscure this connection.
Attachments are an even bigger risk. Before sending a file, you must strip it of its metadata. This hidden EXIF data can contain a startling amount of personal information, including:
- The exact camera or phone model used to take a photo.
- The GPS coordinates of where that photo was taken.
- The name of the author or owner of a document.
Always use a metadata removal tool before attaching files. Conversely, be extremely cautious with any links or attachments you receive, as a single click on a malicious link can compromise your security.
To enhance your daily privacy toolkit, explore the ultimate guide to an email alias service. By integrating these habits into your routine, you move beyond a simple setup to a sustainable practice of real anonymity and strong email security.
Common Mistakes That Compromise Your Anonymity
You can choose the best private hosted email platform and use a top-tier VPN, but a few simple mistakes can unravel your entire security setup. The tools are just the foundation; your habits are what truly maintain your anonymity. Avoiding these common blunders is as important as the initial setup.

The classic mistake? Forgetting to enable your VPN or Tor connection before logging in. This single oversight has major consequences. Just one login without that protection exposes your real IP address directly to the email server, creating an immediate link between your "anonymous" account and your physical location.
This is like carefully crafting a secret identity, only to leave a trail of breadcrumbs leading right back to your front door.
Overlooking Hidden Data Leaks
It’s easy to focus on the text of an email, but what about the invisible data that accompanies your attachments? This metadata can be a goldmine for anyone trying to uncover your identity.
Attachments are the biggest culprits here. An innocent-looking photo or document can be packed with EXIF data that reveals:
- The exact GPS coordinates where a photo was taken.
- The make and model of the camera or phone used.
- The author’s name embedded in a PDF or Word document.
Always run your files through a metadata stripping tool before you attach them. This simple step prevents you from accidentally broadcasting sensitive information.
Anonymity isn’t just about what you say; it's about what your data says for you. Every file attachment and every login is a potential weak point that requires your full attention.
Your Words Can Betray You
Here's a subtle threat to your email privacy most people overlook: your writing style. Your unique phrasing, sentence structure, and even common typos create a "stylometric fingerprint." It’s surprisingly feasible for analysts to use this fingerprint to link your anonymous emails to public posts on social media, forums, or a personal blog.
To mitigate this, be deliberate. Consciously alter your writing style. Use different vocabulary, vary your sentence lengths, and adopt a tone that isn't your natural one. The goal is to create a new voice for your new identity, making it much harder to connect the dots.
Finally, don’t consolidate your risk. Using a single anonymous account for everything is a huge security risk. A much smarter strategy is to create disposable email addresses or aliases for different services. If an alias is ever compromised in a data breach, you can just delete it without any damage to your main anonymous inbox.
This compartmentalization is a powerful buffer that ensures one mistake doesn't bring your entire privacy setup crashing down. This is an advanced tactic that is essential for long-term anonymous and secure communication.
Common Questions About Anonymous Email
Diving into the world of digital privacy can be overwhelming, and it's natural to have questions. Let's clarify some of the most common points about setting up a truly anonymous email.
Is a VPN Enough for Anonymous Email?
A VPN is an essential component of email security, but it is not a complete solution. It serves as your first line of defense by hiding your real IP address from the email service, breaking the direct link between the account and your physical location.
However, a VPN does nothing to hide your identity from the email provider itself. If you use a VPN to log into a service like Gmail, Google still knows who you are. They can still read your non-encrypted messages and link your activity to your account. For true anonymity and email privacy, you must combine a VPN with a hosted email platform specifically designed for privacy.
Can Anonymous Emails Be Traced?
When set up and used correctly, tracing an email back to you becomes incredibly difficult—so impractical that it's nearly impossible for most adversaries. The entire strategy relies on building layers of separation between your real and anonymous identities.
Your email security is only as strong as its weakest link, so you must cover all bases:
- No-Logs Email Provider: Your hosted email platform must have a strict, verified policy of not logging your IP address or other identifying activity.
- Privacy-First Jurisdiction: The provider's legal location matters. Choose one in a country with robust data protection laws, like Switzerland or Germany.
- Secure Connections: Never access your account without a trusted VPN or the Tor network active.
- Smart OpSec: This is your responsibility. Do not use personal details, be mindful of metadata, and never cross-contaminate your anonymous and real identities.
When you combine a secure provider, the right tools, and disciplined habits, your anonymous email becomes a powerful shield. You create a formidable barrier against anyone attempting to discover your identity.
What Is the Difference Between Encrypted and Anonymous Email?
This is an excellent question, and the distinction is critical for understanding email security. They are two different concepts that solve two different problems.
Encryption is about protecting the content of your message. It scrambles the email so that only the person with the correct key (your recipient) can unscramble and read it.
Anonymity, on the other hand, is about protecting your identity. It’s focused on concealing who sent the message in the first place.
For maximum security, you need both. You want an anonymous account that also provides strong, end-to-end encryption. That way, both who you are and what you say are kept completely private.
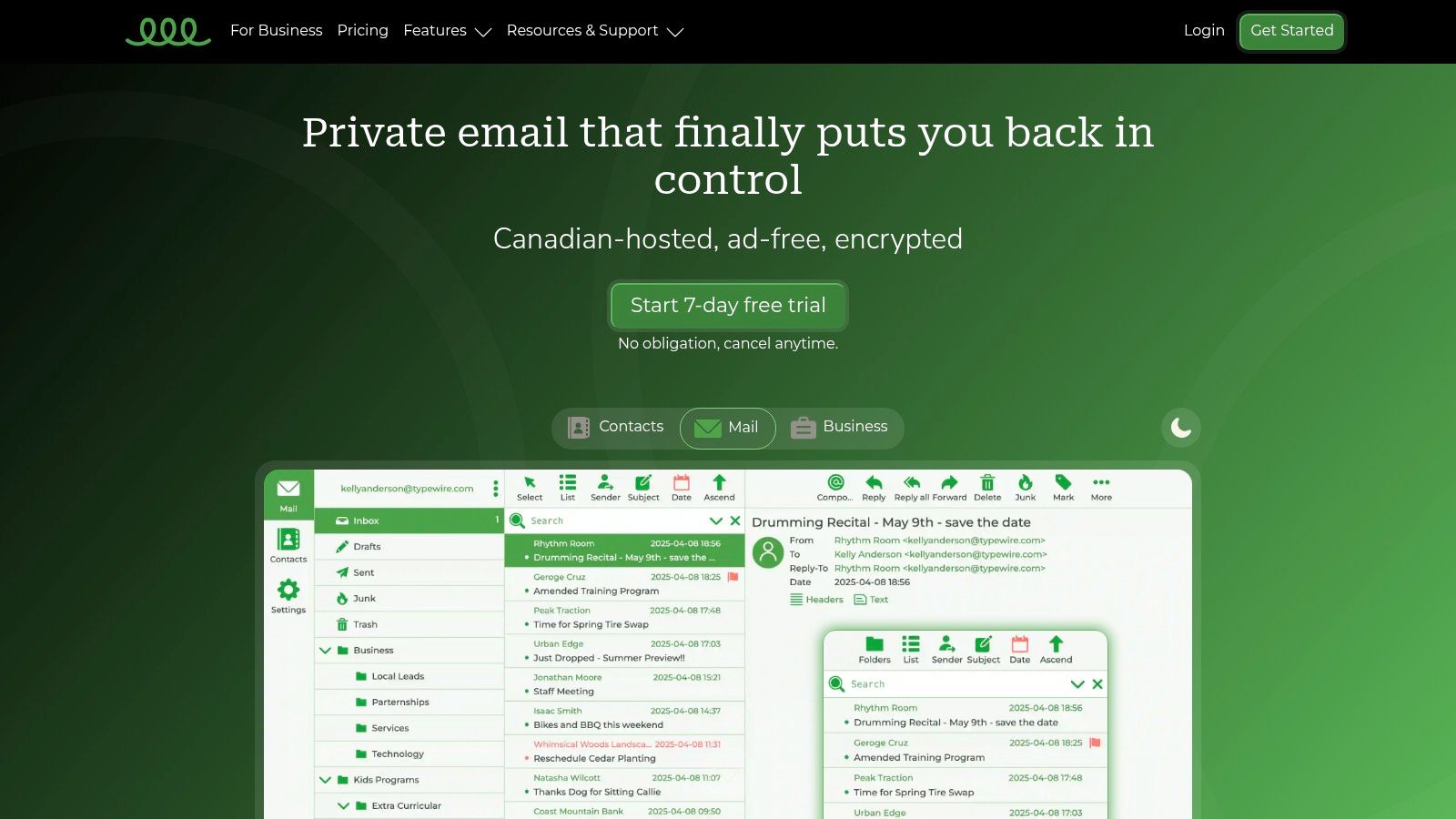
Ready to take back your inbox? Typewire offers secure, private email hosting with no ads, no tracking, and zero data mining. Start your 7-day free trial and experience what true email privacy feels like.